Trojan Wacatac is an umbrella detection for a wide range of malicious software, that shares functionality and code. In particular, the Wacatac name points to malware with dropper capabilities that are used to deliver ransomware.
In this article, I will consider both variants: Trojan:Script/Wacatac.B!ml and Trojan:Win32/Wacatac.B!ml. At first glance, the difference may seem small, but in fact, these are two different types of infections. So, let’s get started!
Trojan Wacatac Detection
Trojan:Script/Wacatac.B!ml and Trojan:Win32/Wacatac.B!ml detection is one of the numerous detection names that Microsoft assigns to minor malware families. A lot of similar-yet-different malicious software received this name because of the use of the same code solutions and similar functionality. Microsoft’s name often becomes a common noun for all similar malware.
When it comes to functionality, Wacatac is mostly spyware or stealer malware. Some of the sub-specimens may be distinctive for using Discord, Telegram, or Mastodon as data exfiltration channels. To have a more clear understanding of what the malware under the Wacatac name looks like, let’s analyze a sample of malware detected as Wacatac.
Trojan:Script/Wacatac.B!ml
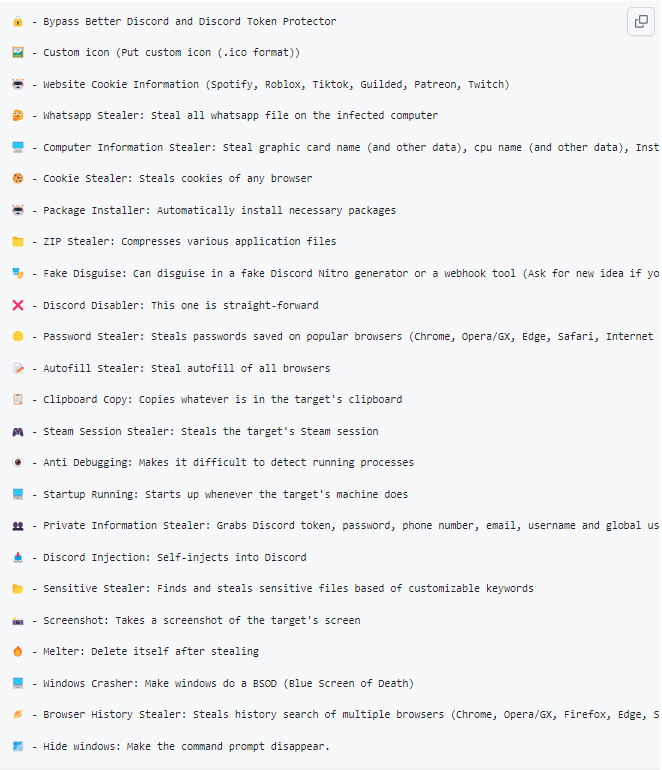
For the analysis of a real-world Wacatac trojan example, I’ve opted for a Trap Stealer. Microsoft detects it as Trojan:Script/Wacatac.B!ml (sample on VirusTotal). The Python-based malware sample is pretty unique – it is an open-source stealer with the source code listed on GitHub. Its builder features extensive functionality, particularly offers to create a disguise out of the box. But let’s have a more precise look.
On the GitHub repository that contains the source code of the malware, its devs show most of the functionality. It corresponds to the abilities of a classic stealer: malware gathers info from WhatsApp, steals cookies, and contents of the clipboard and AutoFill, scrapes passwords, and can capture screenshots. On top of that, Trap Stealers boast of the ability to mischief the host system.
Detection Evasion Methods
I’d pay additional attention to how this malware disguises itself. As I said, the builder offers not only to specify a Discord webhook as a relay server, but also to establish a “shell” that will make the user launch the malware deliberately. Currently, there are two options for this shell – a fake Discord webhook creation tool and a pseudo-Discord Nitro generator. Malware masters may choose one during the building, or choose none at all.
Though, these methods are called to evade user suspicion. Against anti-malware software, especially malware analysis environments, malware has several dedicated tricks up its sleeve.
Upon execution, this malware performs a row of checks that ensure that the system is not running a debug environment, resides away from the banned countries, and is not a virtual machine. If one of the checks returns an unacceptable result, any further execution will be terminated.
| Checks | Purpose |
|---|---|
| check_dll | Scans the list of running DLLs, searching for ones related to virtualization software |
| check_IP | Compares the system IP to the embedded blacklist of countries |
| check_registry | Scans the Windows Registry for specific entries related to VMWare programs |
| check_windows | Enumerates open windows and checks whether any of them are related to reverse engineering/debugging tools. |
Establishing Persistence
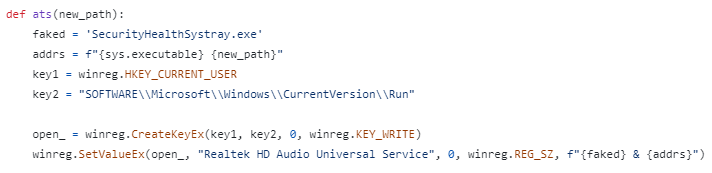
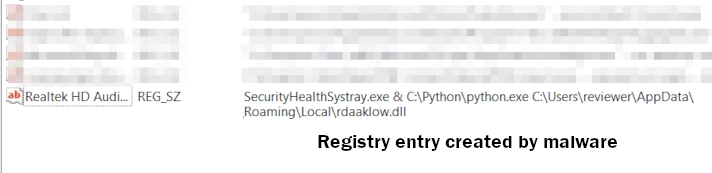
Once all the aforementioned checks are done, Wacatac makes itself persistent to the attacked environment. It creates its randomly-named copy in a random directory in the AppData or LocalAppData folder of a user directory. Then, the malware adds a corresponding value to the Run entry of the system registry. This ensures the malware startup with the system.
These steps may be accompanied by more, if additional actions were specified in the process of sample building. For instance, malware can hook up to the Discord startup, or establish persistence using the user startup folder instead of the registry key.
Data Gathering
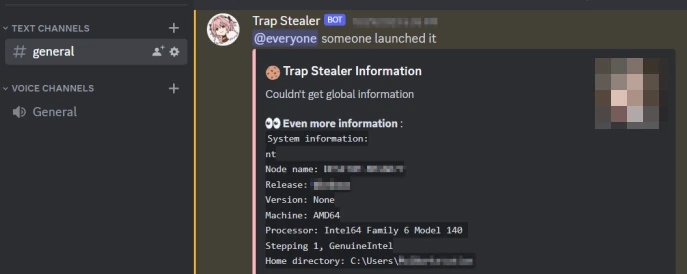
The malware proceeds to its normal activity after establishing persistence. The first thing to do is to collect all the data about the system – it gathers quite a big list of it. Interestingly enough, the malware sends the log with this info to the command server almost instantly. This contrasts with the typical fashion of doing things, when the stealer will get everything it can reach and only then send it to the C2.
| System Info | Malware Instance Info | Software & Hardware Info |
|---|---|---|
| Username | Node Name | OS Name |
| IP Address | Release | System Activation Key |
| Country | Version | PC Name |
| Postal code | Machine | CPU Model |
| Region | Home Directory | GPU Model |
| City | Installed Antivirus | |
| Longitude/Latitude |
This extensive list of system data is then accompanied by collected passwords and cookies. For stealing passwords, Wacatac particularly aims at web browser files. There, it seeks specific files that programs use to keep the info. Aside from files that can contain credentials, Wacatac also collects all the cookies it can find. All the stuff is then kept in the specific files in the AppData\Local\Temp directory, under specific names that start with the “wp” particle.
This Wacatac instance particularly goes for browsing history. Since the way it is handled is more or less unified for most of the browsers, malware targets quite a few of them. Here is the list:
- Safari
- Firefox
- Chrome
- Opera
- Edge
- Opera GX
- Internet Explorer
Stealing Discord Tokens
The Trojan:Script/Wacatac.B!ml sample we are reviewing pays significant attention to Discord, though it is not unique for stealers. Moreover, the method it uses to extract the session tokens is more or less the same for all malware samples. Let’s dive into it.
To get Discord tokens from web browsers, Wacatac seeks for leveldb files (.ldb). It is a database file specific to Chromium-based browsers, that stores auth tokens, keys, and things the like. As there are quite a few popular browsers that derive from Chromium core, malware tries to target them all.
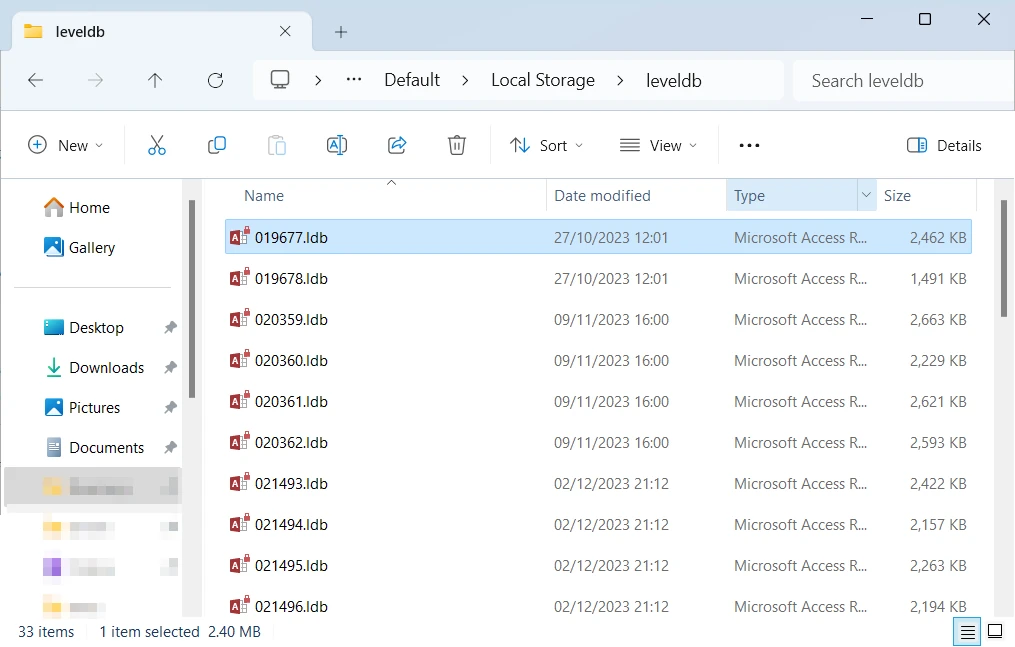
For the sake of clarity, it is worth noting that non-Chromium browsers are not invulnerable to such manipulations. By using database calls, malware can easily extract the info it needs, or even everything all at once. The fact that a browser keeps the data differently means just the need for a couple more lines in malware code.
Aside from crawling through the browser files, the malware also tries to grab the same Discord session tokens from the app’s directory. As there are a few different clients out there, the malware tries targeting them all by scanning for corresponding folders in the AppData\Roaming directory.
Stealing Data of Crypto Wallets & Gaming Apps
Another typical edge of interest for Trojan:Script/Wacatac.B!ml is crypto wallets as extensions, desktop apps, and gaming applications. It particularly aims for Metamask, Atomic, Exodus, and NationsGlory crypto wallets. However, stealing other wallets is just a question of a proper configuration, so they may appear in the future. All the collected data is compressed into a .zip folder and sent to the C2.
For gaming apps, malware particularly aims at Steam and Riot Client. Malware seeks for their folders in AppData\Local and then creates a zipped copy of their directories.
Exfiltration and C&C Connections
Once Trojan:Script/Wacatac.B!ml finishes the extraction, it will keep idling, waiting for new data to steal. Upon every startup, it will go through all the scans I’ve mentioned above, trying to find new stuff to steal. However, a malware master can order it to self-destruct when it finishes the data collection, or even enforce the system crash at this moment. This all is needed to hide the traces of malware activity.
Protecting Against Trojan:Script/Wacatac.B!ml
Stealer malware, such as Trojan:Script/Wacatac.B!ml, is often easily detectable by well-designed antivirus programs. An antivirus program equipped with heuristic detection systems and AI assistance can readily identify and remove this threat. GridinSoft Anti-Malware, in particular, is a reliable choice for this task. It can remove the malware and ensure your PC remains safeguarded for an extended period.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.