The Security Blog From Gridinsoft
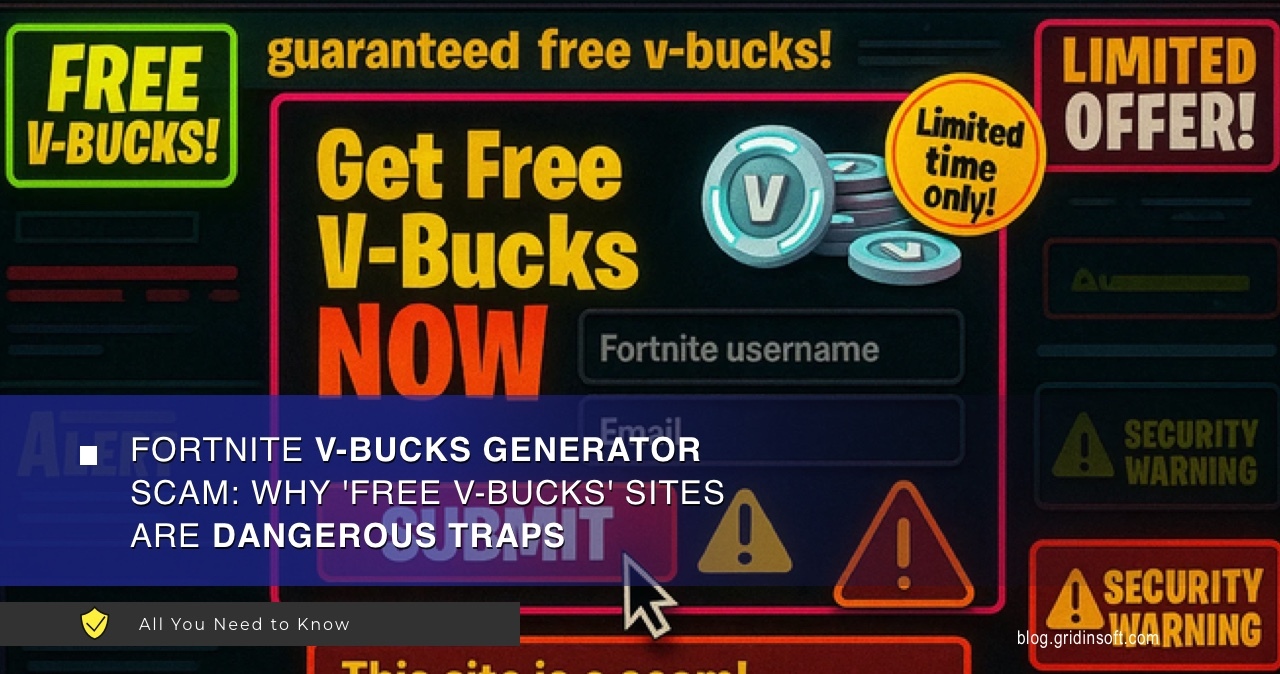
Fortnite V-Bucks Generator Scam: Why ‘Free V-Bucks’ Sites Are Dangerous
When you see a website promising free Fortnite V-Bucks, you’re looking at a carefully crafted trap. These sites can’t actually…
Odyssey Stealer: Russian ‘Love Trump’ Malware Replaces Ledger Live Crypto Wallet App
A new macOS malware campaign is targeting users through social engineering, masquerading as legitimate Cloudflare security verification. The Odyssey Stealer…
Cybercriminal campaign exploiting Booking.com
Cybercriminals are running a two-pronged attack targeting both travelers and hotel staff through the Booking.com platform, according to security research…
Noodlophile Stealer: Cybercriminals Hijack AI Hype to Steal Your Data
Just when you thought cybercriminals couldn’t get more creative, they’ve found a way to weaponize our collective obsession with AI.…
Octalyn Stealer: How This Threat Steals Passwords, Crypto & Browser Data
Octalyn Stealer is an information-stealing malware that’s currently being promoted on GitHub – because apparently, even cybercriminals believe in open-source…
Octalyn Stealer: How This Threat Steals Passwords, Crypto & Browser Data
Octalyn Stealer is an information-stealing malware that’s currently being promoted…
Elon Musk’s “Double Your Crypto” Scams: Too Good To Be True
So apparently, some people still believe internet strangers will double…
Investment Scams on Facebook: How Cybercriminals Filter and Target Victims
Investment scams continue to evolve in sophistication, with cybercriminals deploying…
BreachForums is Down, Admins Posted a PGP-Signed Message
BreachForums, an infamous Darknet forum, has gone offline recently, only…
$GROK Presale Scam: Crypto Investment Fraud
The $GROK Presale Scam tricks people into investing in a…
CVE-2025-21605 Redis DoS Vulnerability Discovered, Patch Now
So Redis walks into a bar and the bartender asks,…
WordPress Ad-Fraud Plugins and the Scallywag Operation
Cybersecurity researchers have found a large-scale ad fraud scheme called…
MITRE Warns CVE Program Funding Expires on April 16
MITRE, a key player in cybersecurity awareness, has issued a…
CVE-2025-32395 Vite Vulnerability Exposes Sensitive Files
A newly discovered Vite vulnerability, a widely used frontend development…
Google Releases Two Android Zero-Day Fixes, Exploited in the Wild
Google addressed two critical Android zero-day vulnerabilities in Android, identified…
Urgent Reminder Tax Scam
The “Urgent reminder” tax scam is a yearly phishing effort…
Samsung Tickets Data Leak
The Samsung tickets data leak involves a breach affecting Samsung…