Cybersecurity researchers have found a large-scale ad fraud scheme called “Scallywag”. It used WordPress plugins to generate massive fraudulent ad traffic. As for now, interventions from law enforcement agencies have drastically reduced the traffic, but domain rotations and new monetization models suggest the issue persists, albeit at a lower scale.
WordPress Ad-Fraud Plugins and the Scallywag Operation
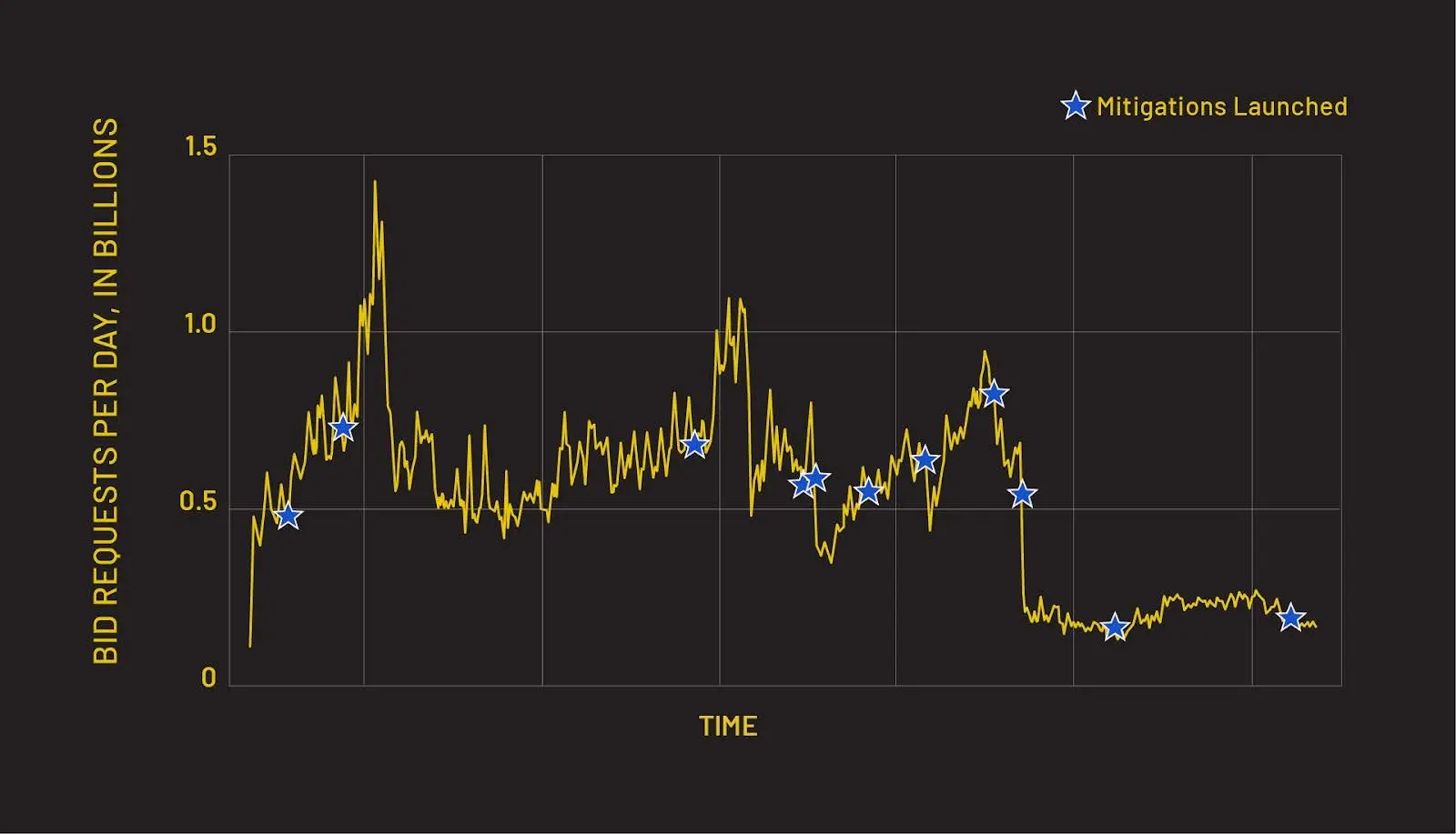
Recently, cybersecurity firm HUMAN has uncovered a massive ad fraud operation known as “Scallywag”. This scheme used specially crafted WordPress plugins to hijack traffic from pirating and URL shortening sites, generating up to 1.4 billion fake ad requests per day at its peak.
The operation relied on a vast network of 407 domains, which were mapped out during the investigation. While Scallywag’s activity has since dropped by 95% thanks to aggressive blocking and takedown efforts, the threat actors behind it are proving annoyingly persistent. They are rotating domains and shifting to new monetization tactics, like digital cockroaches refusing to die.
Operation Details
Scallywag operates as a “fraud-as-a-service” model, utilizing specific WordPress extensions to monetize digital piracy and URL-shortening services. The WordPress plugins involved in the operation include Soralink, which is claimed to have been created in 2016, Yu Idea, with documentation dating back to 2017, WPSafeLink, reportedly developed in 2020, and Droplink, which appeared in 2022 and was distributed for free through various cashout blogs.
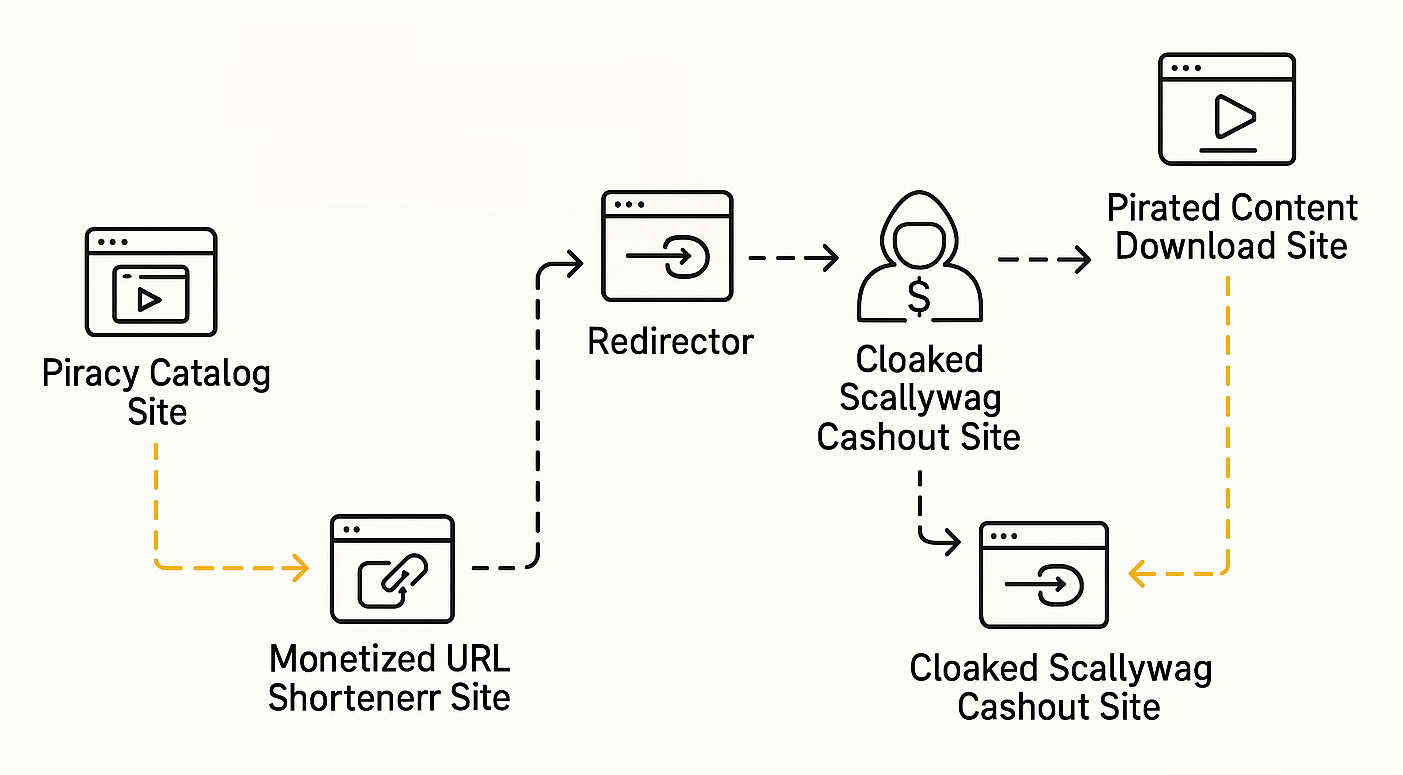
These plugins facilitate the insertion of intermediary pages loaded with ads, deceptive buttons, and artifacts, often requiring users to navigate through CAPTCHAs or wait times to access promised content. This method maximizes ad impressions and revenue, particularly from piracy catalog sites and URL shorteners, which are typically shunned by legitimate advertisers due to legal and brand safety risks.
The operation employs cloaking techniques, where direct visits from advertisers show benign blog content, while traffic from piracy or URL-shortening domains triggers ad-heavy pages. Additionally, open redirectors, such as those from Google or X, are used to sanitize referrer data, obscuring the fraudulent nature of the traffic.
Scale and Impact
As said above, at its peak in early 2024, Scallywag accounted for 1.4 billion fraudulent bid requests daily. The operation’s network spanned 407 cashout domains, with detailed lists available as of February 2025. Detecting Scallywag involves analyzing traffic patterns, such as high ad impression volumes, cloaking behavior, forced wait times, and CAPTCHA usage. The operation’s use of deep linking to decloak content and open redirects complicates attribution.
The monetization strategy involves selling access to these WordPress extensions, empowering independent cybercriminals to launch their own ad fraud campaigns. Some threat actors have even shared instructional videos on YouTube, coaching others on maximizing the use of Scallywag extensions, further amplifying the operation’s reach.
After traffic analysis and domain blocking, have led to a 95% reduction in Scallywag’s traffic from its peak, dropping daily ad fraud requests to nearly zero. However, the threat actors also have shown resilience, adapting by rotating domains and introducing new cashout sites to evade mitigations. Some have pivoted to content discovery networks, indicating ongoing evolution in their tactics.
How to Protect Against Fraudulent Sites?
To avoid such sites and malicious ads, you just need to do the following two rules. First and most importantly, avoid visiting pirate sites. Apart from the fact that in most cases it can cause legal problems, as we can see, it is also a source of all sorts of threats, from advertising questionable things to spreading malware. If you doubt the reliability of a website, you can use our free Website Reputation Checker to quickly check the reliability of a website.
The second fundamental recommendation is to use anti-malware software. I recommend GridinSoft Anti-Malware because it contains an Internet Security module that blocks potentially dangerous sites. Of course, this does not cancel the previous point and does not give you permission to browser dubious sites. Rather, this item complements the previous one by ensuring that in case of an unintentional visit to a malicious site, this solution will notify the user of the potential risk and block access to the site.