The Raspberry Robin worm uses new tactics to evade detection and seeks to confuse security experts if it runs in a sandbox or notices debugging tools.
To do this, the malware uses fake payloads, Trend Micro experts say.
Let me remind you that Raspberry Robin is a dropper that has the functionality of a worm, the authors of which sell access to compromised networks to extortion groups and operators of other malware. Experts have previously associated it with hack groups such as FIN11 and Clop, as well as payload distributions of Bumblebee, IcedID and TrueBot.
The first Raspberry Robin was found by analysts from Red Canary. In the spring of this year, it became known that the malware is distributed using USB drives (it infects devices with malware after clicking on the .LNK. file) and has been active since at least September 2021. The cybersecurity company Sekoia even observed that back in November last year, malware used Qnap NAS devices as control servers.
It was previously noted that the malware is heavily obfuscated to protect its code from antiviruses and researchers, and also has several layers containing hard-coded values to decrypt the next one.
To make things even more difficult for security professionals, Raspberry Robin recently began using different payloads depending on how it runs on the device, Trend Micro researchers now report. So, if the malware detects that it is running in a sandbox or they try to analyze it, the loader resets the fake payload. If nothing suspicious is found, the real Raspberry Robin malware is launched.
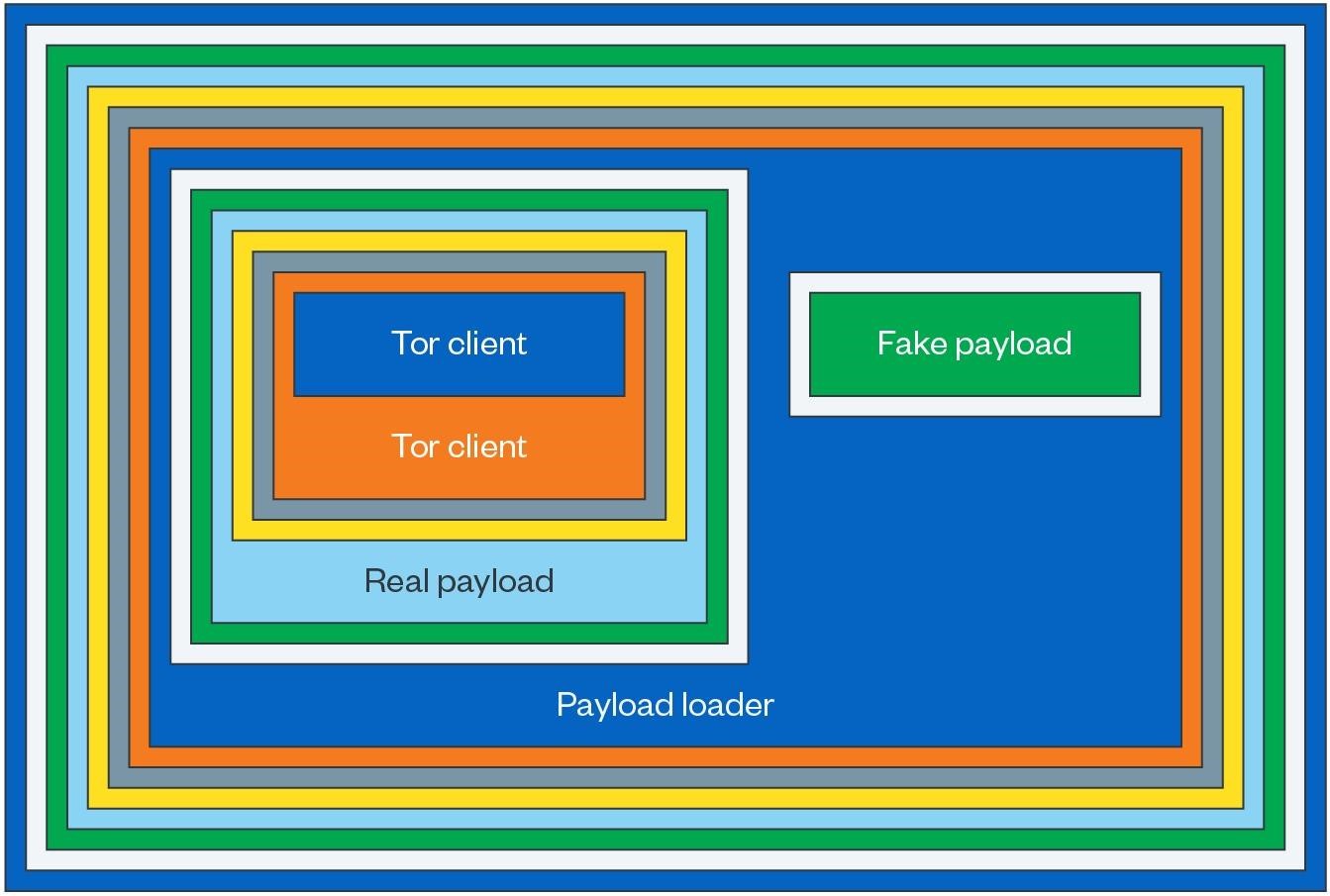
The fake fake payload has two additional layers: a shellcode with an embedded PE file and a PE file with the MZ header and PE signature removed. Once executed, it examines the Windows registry for signs of infection and then proceeds to collect basic information about the system.
The fake then tries to download and run the BrowserAssistant adware to make the researchers think it is the final payload. In fact, in truly infected systems that did not arouse suspicion in the malware, a real Raspberry Robin payload is loaded with a built-in customized Tor client for communication. Trend Micro’s report highlights that even with the fake payload being used as a distraction, the real payload is still packaged with ten levels of obfuscation, making it much more difficult to analyze.
The real payload is also said to check if the user is an administrator on startup, and if not, it uses the ucmDccwCOMMethod privilege escalation technique in UACMe to gain administrator rights. The malware also makes changes to the registry to maintain its presence in the system between reboots, using two different methods for this (for a user with and without administrator rights).
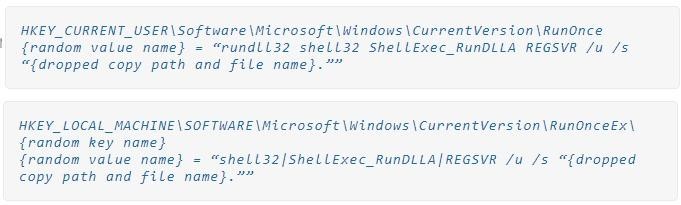
The malware then attempts to connect to hard-coded Tor addresses and establishes a communication channel with its carriers. However, the Tor client process uses names that mimic standard Windows system files, including dllhost.exe, regsvr32.exe, and rundll32.exe.
It is noteworthy that the main procedures are performed within Session 0, that is, in a specialized session reserved by Windows exclusively for services and applications that do not need or should not interact with the user.
Also Raspberry Robin still copies itself to any connected USB drives to infect other systems. At the same time, the researchers believe that the current campaign is more of a reconnaissance operation and an attempt to evaluate the effectiveness of new mechanisms, and not the initial stage of real attacks.
Let me remind you that we also wrote that Microsoft Links Raspberry Robin Worm to Evil Corp.




