Microsoft analysts have noticed that the access broker, which the company tracks as DEV-0206, is using the Raspberry Robin Windows worm to deploy the malware loader on networks where traces of malicious activity by Evil Corp are also detected.
Let me remind you that we also wrote that The Austrian Company DSIRF Was Linked to the Knotweed Hack Group and the Subzero Malware, and also that Experts Find Similarities Between LockBit and BlackMatter.
Let me remind you that last month, researchers discovered the presence of the Raspberry Robin worm in the networks of hundreds of organizations from various industries, some of which worked in the technology and manufacturing sectors. Although Microsoft observed how the malware binds to addresses on the Tor network, the attackers’ targets remained unknown, as they did not yet have access to their victims’ networks.
Raspberry Robin malware was first found by analysts from Red Canary. In the spring of this year, it became known that the malware has the capabilities of a worm, spreads using USB drives, and has been active since at least September 2021. Security company Sekoia even observed how malware used Qnap NAS devices as control servers back in November last year.
While the hackers did nothing, Microsoft labelled the campaign as high-risk, given that attackers could download and deploy additional malware on victims’ networks at any time and elevate their privileges.
Now, researchers have finally seen the first signs of how the hackers intend to exploit the access they have gained to their victims’ networks with the Raspberry Robin.
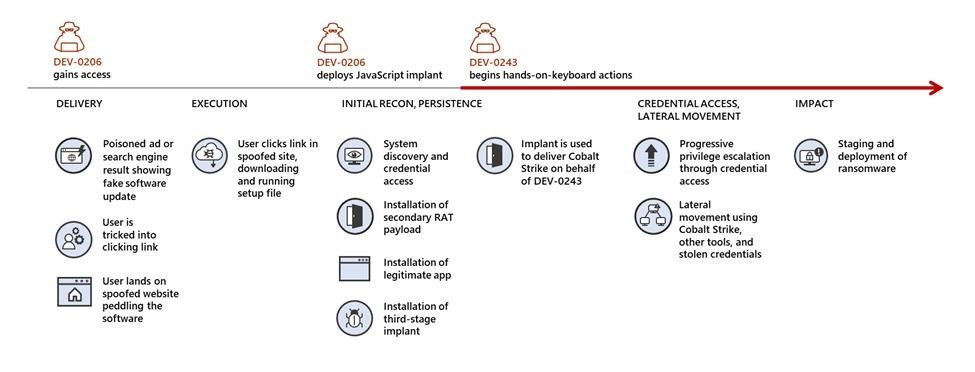
The aforementioned DEV-0206 is the code name for an access broker that deploys the FakeUpdates malware on victim machines, forcing the victim to download fake browser updates as ZIP archives. This malware essentially works as a conduit for other malicious campaigns and attackers who use access acquired from DEV-0206 to spread their payloads. So, the noticed Cobalt Strike loaders, apparently, are associated with the DEV-0243 group, better known as Evil Corp.
In June 2022, cybersecurity experts noticed that Evil Corp switched to using the LockBit ransomware to avoid sanctions previously imposed by the US Department of the Treasury’s Office of Foreign Assets Control (OFAC). It was assumed that the use of other people’s resources and this new tactic would allow hackers to spend the time saved on developing their own malware to expand their operations.

