The Evil Corp group switched to using the LockBit ransomware to avoid sanctions imposed earlier by the Office of Foreign Assets Control of the US Department of the Treasury (OFAC).
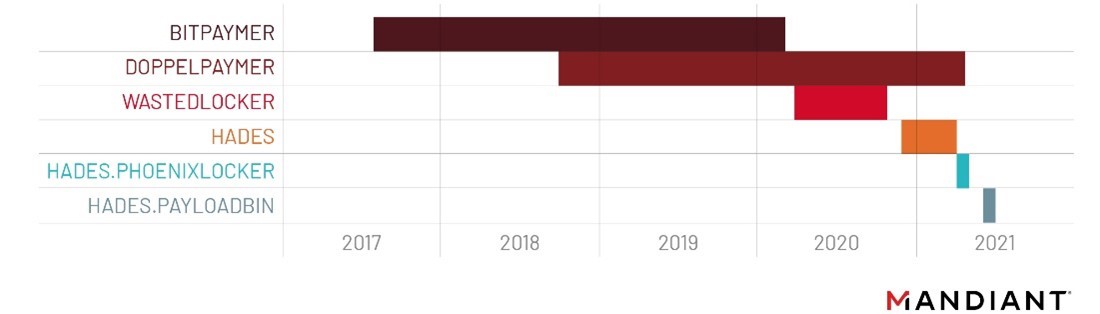
Let me remind you that Evil Corp has existed since at least 2007, but at first hackers more often acted as partners for other groups. It was only later that Evil Corp began to focus on its own attacks, creating the well-known banking Trojan Dridex. Over time, when it became a ransomware, attacks became more profitable, and Evil Corp launched its own BitPaymer ransomware, delivering it to victims’ machines via Dridex. The latter gradually evolved from an ordinary banker into a complex and multifunctional tool.
All this led to the fact that in 2019 the US authorities filed charges against two Russians who, according to law enforcement officers, were behind the development of the Dridex malware and other malicious operations. Also, the US authorities imposed sanctions on 24 organizations and individuals associated with Evil Corp and the mentioned suspects. As a result, the negotiating companies, which usually negotiate with extortionists to pay a ransom and decrypt the data, refused to “work” with Evil Corp in order to avoid fines and lawsuits from the US Department of the Treasury. And it became much more difficult for the victims themselves to pay the ransom.
After that, in June 2020, Evil Corp switched to using the WastedLocker malware, in 2021 the Hades ransomware appeared (a 64-bit version of WastedLocker, updated with additional code obfuscation and a number of functions), and then the group has already carried out several “rebrands” and impersonated for the PayloadBin grouping and used other ransomware: Macaw and Phoenix.
Now, Mandiant analysts noticed that criminals have made a new attempt to distance themselves from hacking tools known to experts so that their victims can pay ransoms without violating OFAC rules.
The activity cluster, which Mandiant tracks as UNC2165, previously deploying the Hades ransomware and associated with Evil Corp, is now “partnering” with the developers of the LockBit ransomware.
It is assumed that the new tactics will allow hackers to spend the time saved on developing their own malware to expand operations.
Experts also offer another theory: it is likely that the transition to other people’s malicious tools will help Evil Corp free up enough of its own resources to develop a new ransomware from scratch, which can subsequently seriously complicate tracking the new operations of the hack group.




