Mobile Security
Google Releases Two Android Zero-Day Fixes, Exploited in the Wild
Google addressed two critical Android zero-day vulnerabilities in Android, identified as CVE-2024-53150 and CVE-2024-53197, through the April 2025 security update.…
Salvador Stealer: Dangerous Android Banking Malware Targeting Financial Data
Salvador Stealer is a sophisticated Android banking trojan that targets financial applications through advanced phishing techniques. This malware creates convincing…
Your iPhone Has Been Hacked
“Your iPhone Has Been Hacked” is a fake web browser notification designed to trick users into installing dangerous software. In…
List of Scammer Phone Numbers 2025
Phone scams continue to plague consumers worldwide, with fraudsters developing increasingly sophisticated tactics to steal personal information and money. Our…
Top 3 MMS Scams: What Threats Can Messages Bring
MMS is a rather old technology that is being pushed out of the market by proper messenger applications. Nonetheless, fraudsters…
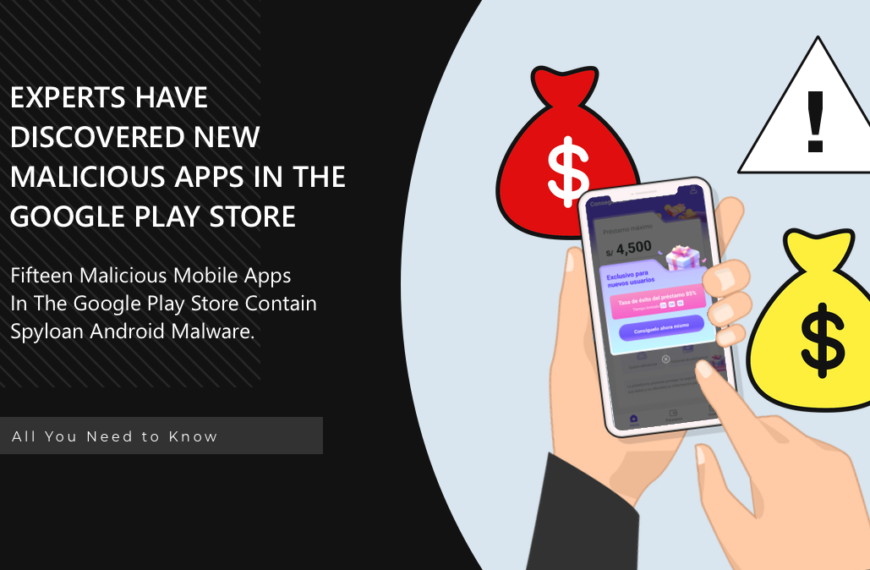
SpyLoan Virus Found in Loan Apps on Google Play Store
Experts reported the discovery of a new set of 15…
Two Android Zero-Day Flaws in Google Pixel Exploited
Google has disclosed that two Android zero-day security vulnerabilities have…
SecuriDropper Bypasses Google Play & Android Defenses
SecuriDropper is a rare example of the Android dropper malware…
Malicious WhatsApp Mods Spread Through Telegram
Some WhatsApp mods, which are unofficial versions of the app,…
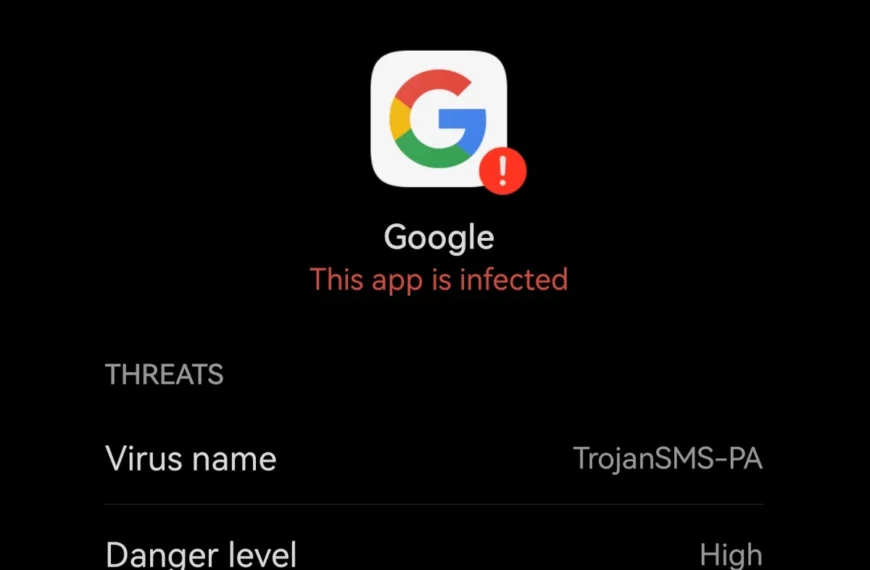
What is Android:TrojanSMS-PA detection?
Android:TrojanSMS-PA is a detection name from a built-in Huawei security…
Android Malware With Almost 500M Downloads Resides in Google Play
Millions of Android users may be at risk of a…
ChatGPT Causes New Wave of Fleeceware
Artificial intelligence is one of the most significant advances in…
Android Malware. Is Malware on Android Phone Possible?
Android malware is a common name for all malicious software…
Can Someone Track My Device When Location Settings Off?
Any smartphone already has built-in location tracking services. At the…
How To Know If Your Phone is Hacked?
If your phone stopped working correctly and started showing obvious…
Vulnerability in Apple iCloud puts billion users at risk
Security of over a billion iPhone owners and users of…
Unofficial fixes released for 0-day issue in Windows Mobile Device Management Service
Unofficial fixes released for 0-day issue in Windows Mobile Device…