SecuriDropper is a rare example of the Android dropper malware that operates under the dropper-as-a-service (DaaS) model. This malware is raising significant concerns among experts due to its ability to bypass Google’s enhanced security measures and deliver a variety of malicious payloads.
What is SecuriDropper Malware?
SecuriDropper represents the latest evolution in the ever-changing world of cyber threats. It serves as a conduit for cybercriminals to efficiently distribute their malware in a convenient way. This, actually, is a key point of the dropper-as-a-service model. Such innovation enables threat actors to separate the development and execution of an attack from the installation of malware. This trick offers a level of sophistication that is both concerning and challenging to combat.
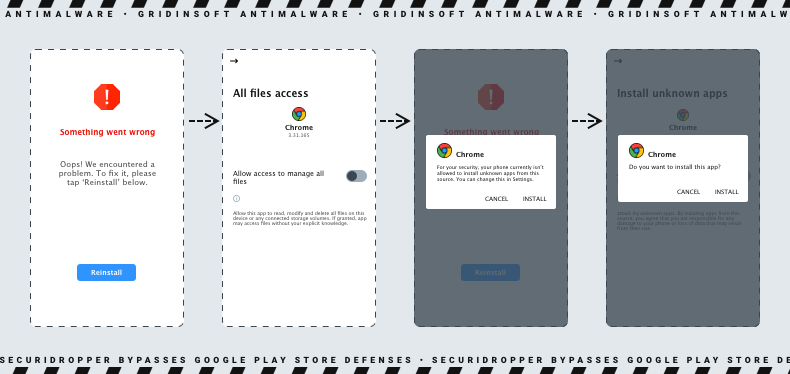
Dropper malware plays a crucial role in the cybercriminal ecosystem. It acts as a precursor tool designed to provide initial access to the target system. Its primary function is to download and install a malicious payload on the victim’s device, making it a valuable tool for threat actors. This strategic approach allows malicious actors to advertise their services to other criminal groups, creating a lucrative business model.
Distribution of Malicious Payloads
SecuriDropper has been observed distributing a range of malicious payloads, including Android banking trojans such as SpyNote and ERMAC. These trojans are often disguised as legitimate applications and are distributed through deceptive websites and third-party platforms like Discord. The resurgence of Zombinder, another Dropper-as-a-Service tool, has further amplified concerns about the distribution of malware payloads through sideloaded apps.
SecuriDropper is a stark reminder that the fight against cyber threats is an ongoing and evolving battle. As Android continues to implement enhanced security measures, cybercriminals adapt and innovate, finding new ways to infiltrate devices and distribute malware. Dropper-as-a-Service platforms have become powerful tools for malicious actors, posing significant challenges to Android security.
Android 13 Feature Blocks SecuriDropper
Despite quite depressing statements from the above, things are not that bad. Users who got Android 13 updates for their devices are able to counteract SecuriDropper on their own. The new feature called Restricted Settings does what it sounds like to the side-loaded applications.
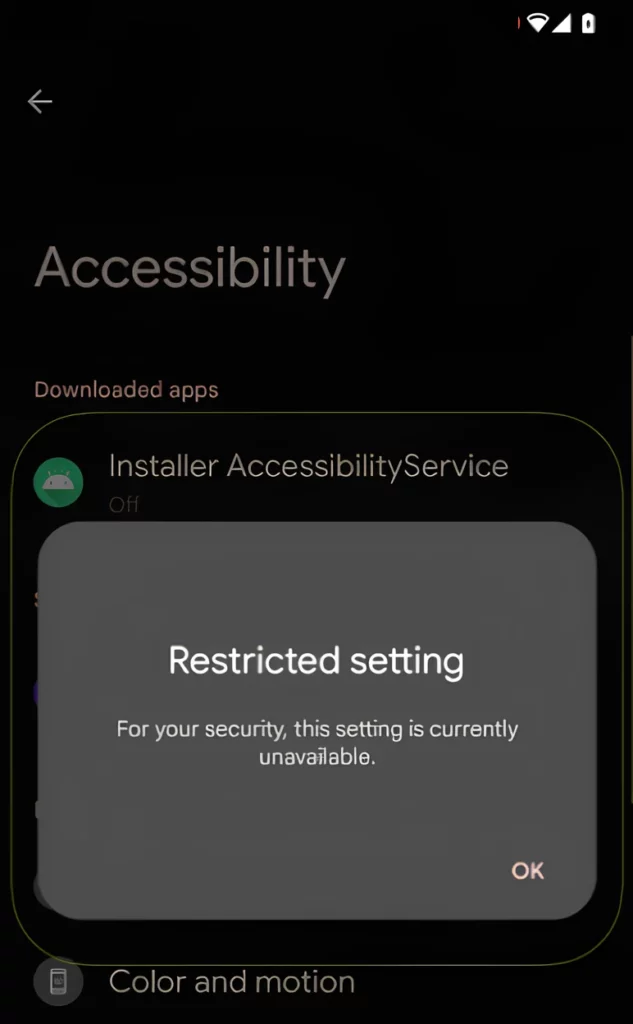
As the dropper aims at getting excessive permissions, particularly to Accessibility and Notifications, the feature will block such permissions by default. This, however, is an Android 13-only feature, so users of earlier OS versions should be careful when granting permissions.
Folks with the most recent updates should not be reckless either. There is a chance of an infected app in the Google Play Market, which diminishes any anti-side-loaded apps tricks. And since Google hesitates with implementing security features to its official app sources, it remains a source of a threat.
How to Protect Yourself from SecuriDropper
SecuriDropper is a sophisticated Android dropper-as-a-service malware that poses a significant threat to the security of Android devices. To protect yourself from this emerging threat and similar malware, follow these security measures:
- Only download applications from official app stores like Google Play Store. These platforms implement stringent security measures to ensure the safety of the apps they host.
- Regularly update your Android device’s operating system and installed applications. Software updates often include security patches that address known vulnerabilities.
- Install a reputable mobile security solution on your device. These security apps can help detect and remove threats like SecuriDropper from your device.
- Be cautious when considering sideloaded apps obtained from unofficial sources. While sideloading offers access to a wider range of apps, it also presents security risks. Ensure you trust the source and origin of sideloaded apps.
- Pay close attention to the permissions requested by apps during installation. Avoid granting unnecessary permissions to apps. For example, if a simple flashlight app requests access to your contacts and camera, it may be suspicious.
- Regularly backup your important data to a secure location or cloud storage. This ensures you can recover your data in case of a malware infection.
By following these security measures, you can reduce the risk of falling victim to SecuriDropper and other similar threats. Remember that staying vigilant and proactive in protecting your Android device is essential in today’s evolving threat landscape.




