The developer of the popular npm package node-ipc has released updated versions of his library and in this update expressed its protest against the ongoing Russian aggression in Ukraine.
New versions of the package delete all data and overwrite files on the machines of developers from Russia and Belarus, and also create text files with calls for peace.
It’s worth noting that node-ipc gets over 1M downloads a week and is an important package that many other libraries rely on, including the Vue.js CLI for example.
The Bleeping Computer publication reports that the destructive code contains package versions 10.1.1 and 10.1.2, which are now tracked under the identifier CVE-2022-23812 as malware.
It all started with the fact that on March 8, the developer Brandon Nozaki Miller, known under the nickname RIAEvangelist, published peacenotwar and oneday-test open source packages (both on npm and on GitHub). These packages appear to have been created as a protest, as they add a “call for peace” to the desktop of any user who installs them.
However, it has now been discovered that some versions of the famous node-ipc library, also maintained by RIAEvangelist, contain much more destructive payloads aimed at destroying all data and overwriting their users’ files. The malicious code, introduced into packages by the developer on March 7, 2022, targets the external IP address of the system and deletes data (by overwriting files) only for users from Russia and Belarus.
A simplified version of this code, already published by the researchers, shows that for users from Russia and Belarus, the code will overwrite the contents of all files present in the system, replacing them with emoji hearts, thereby effectively deleting data.
Because node-ipc versions 9.2.2, 11.0.0 and later include Peacenotwar, affected users also find a “WITH-LOVE-FROM-AMERICA.txt” message on their desktop where the author calls for peace.
Researchers at Snyk also discovered and analysed this malicious activity. On the blog, the experts write:
Snyk analysts suspect that systems-damaging versions of node-ipc 10.1.1 and 10.1.2 were removed by npm within 24 hours of posting. However, node-ipc versions 11.0.0 and higher are still available and contain the mentioned Peacenotwar component, which leaves “peace calls” on the desktop.
Worse, the panic associated with what happened has already affected users of the popular Vue.js JavaScript framework, which also uses node-ipc in its dependencies. Following the incident, users have reached out to the Vue.js developers to only use secure versions of node-ipc that don’t try to destroy all their data.
Let me remind you that we reported that Hacker groups split up: some of them support Russia, others Ukraine.
At the same time, BleepingComputer notes that Vue.js is not the only open source project that has had problems due to this sabotage. For example, developers Lukas Mertens and Fedor are already warning other developers not to use a malicious version of node-ipc.
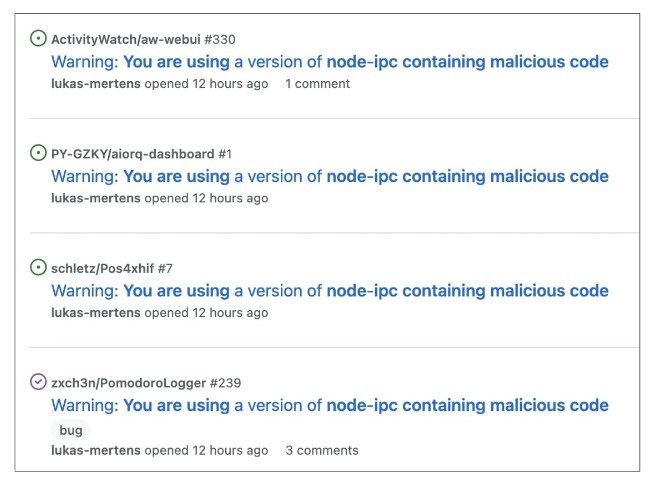
Currently, the safe version of node-ipc is 9.2.1. However, developers should exercise caution when using node-ipc and other RIAEvangelist libraries, as there is no guarantee that future versions of any of its libraries will be safe, at least as long as the killer and dictator Putin is alive.
And also we wrote that DuckDuckGo downgraded Russian state media in search results.

