Fraudsteds massively employ Microsoft Azure hosting to start Microsoft Security scam pages. They range from a scary warning that blocks your browser window to a phishing pages, indistinguishable from real. Let’s see the most typical types of these scams and their features.
What is Windows Defender Security Warning?
Fake Windows Defender Security Warning (Microsoft Security Warning) is a malicious attempt to deceive users into believing their system is compromised or at risk. In reality, these warnings are part of a scam. Cybercriminals create deceptive pop-up notifications or messages that mimic the appearance and language of genuine Windows Defender alerts. These counterfeit warnings often use scare tactics.
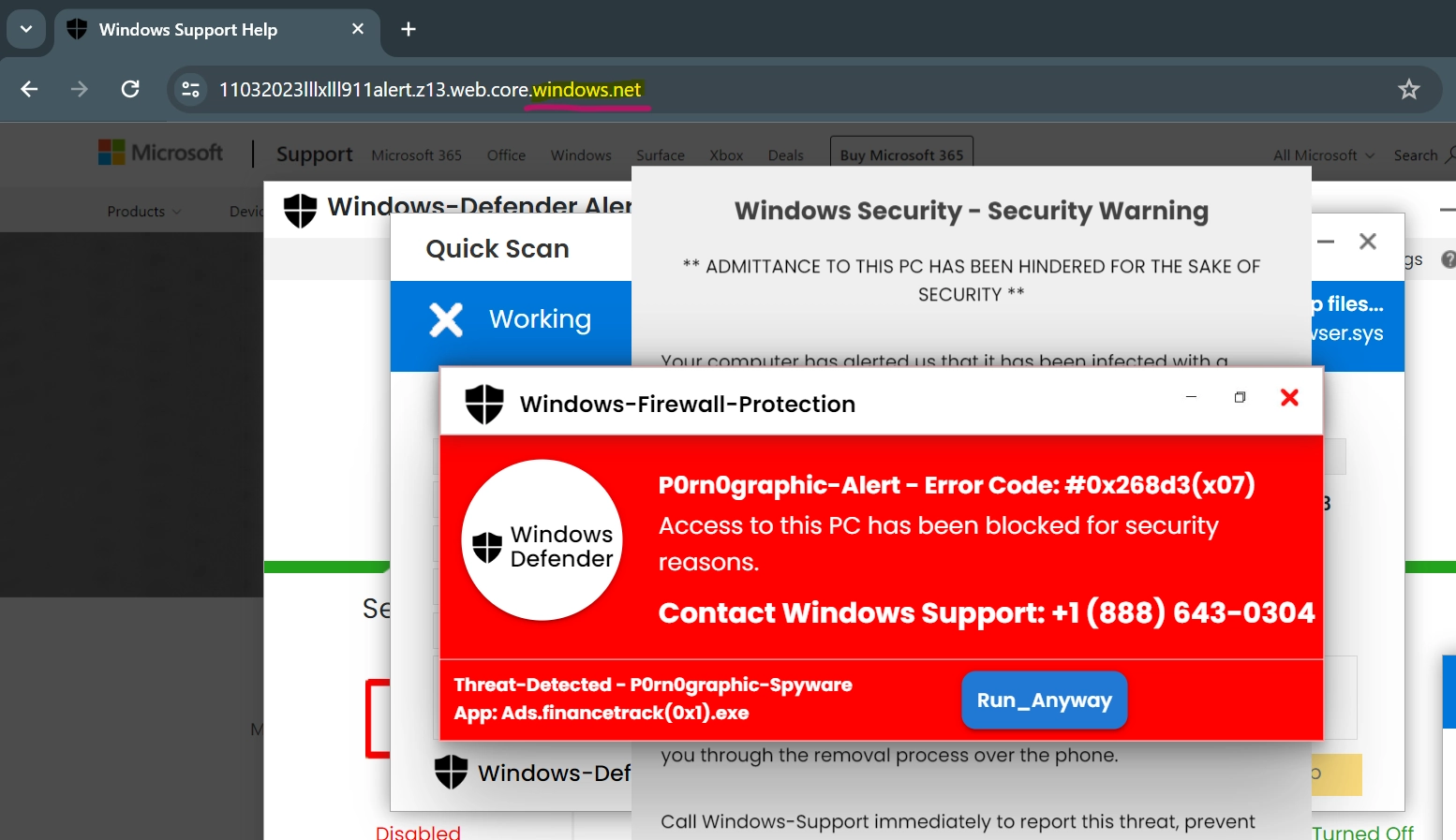
Usually, such sites claim the presence of malware, viruses, or security breaches on the user’s system. They aim to trick users into taking immediate, unwarranted actions. It can be clicking on malicious links, downloading fraudulent software, or providing sensitive information like login credentials or credit card details.
What makes these fake warnings even more convincing is the abuse of Microsoft Azure services. In short, Microsoft Azure is a reputable cloud computing platform that provides tools and services for legitimate purposes, including hosting websites and applications. However, cybercriminals exploit Azure’s flexibility to host their malicious landing pages and phishing sites, thereby lending an air of legitimacy to their schemes.
By leveraging Azure, scammers can secure SSL certificates and create deceptive subdomains, making their fake security warnings appear more convincing. They use Azure to build seemingly genuine login forms and landing pages, often targeting users with Microsoft, Office 365, Outlook, or OneDrive accounts.
How Does This Scam Work?
There are two most common scenarios for this kind of scam, and we’re going to look at them now.
Fake Login Page
In the first common scenario, attackers launch spam email campaigns that appear to originate from a reputable organization. For example, these scammers do their best to trap victims by mimicking the official login pages for Microsoft, Office 365, Outlook, and OneDrive. More often than not, these pages are indistinguishable from the real thing. For example, they may have a Microsoft logo, the correct color schemes, and even a nearly identical URL. Many users may genuinely believe they are on a legitimate Microsoft page.
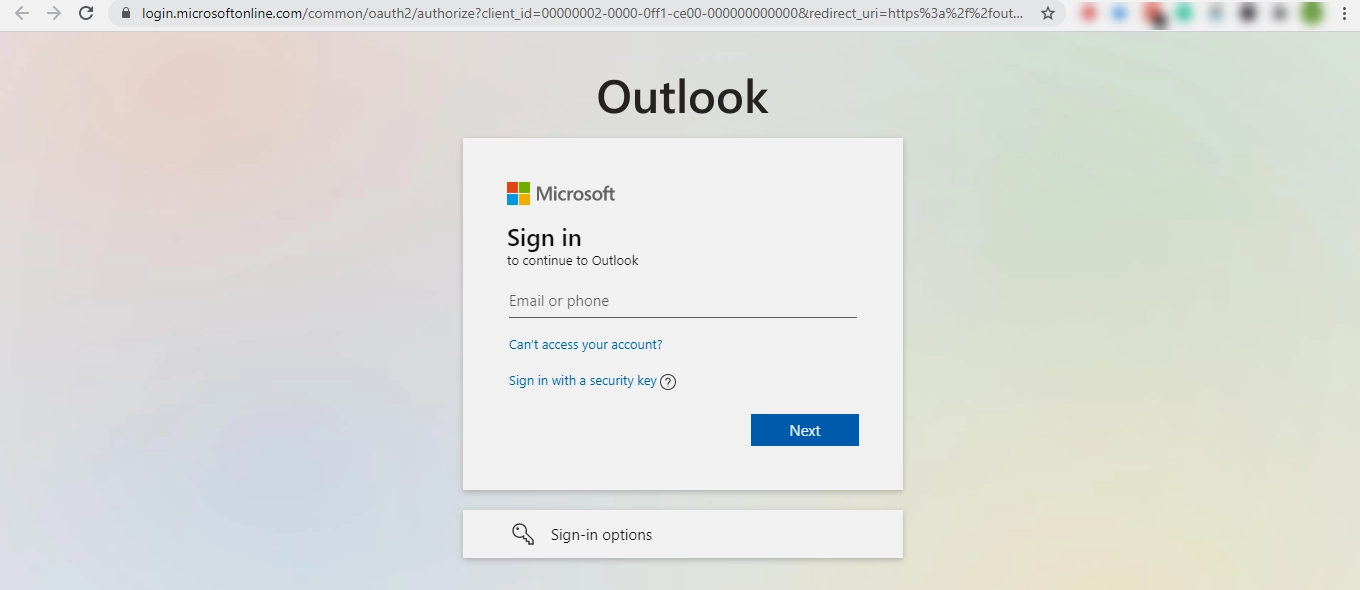
To make their attacks even more convincing, attackers use Transport Layer Security (TLS) certificates. These certificates encrypt data between a user and a website and often serve as an indicator of trust. In this case, the certificates issued by Microsoft Azure TLS Issuing CA 05 for the *.1.azurestaticapps.net domain make the fake pages indistinguishable from the real ones. Attackers go even further to make their phishing pages attractive to attack users of other platforms such as Rackspace, AOL, Yahoo, and other email services. In this case, the spoofing becomes particularly camouflaged thanks to legitimate Microsoft security certificates.
When users are trying to determine if a phishing attack is targeting them, they are usually advised to carefully check the URL in the browser bar when prompted to enter credentials. However, in the case of phishing campaigns abusing Azure Static Web Apps, this advice is meaningless, as the azurestaticapps.net subdomain and the presence of a valid TLS security certificate will fool many users.
Tech Support Scam
Fake Microsoft Technical Support Scam – involves a scheme in which attackers impersonate Microsoft representatives or certified technicians. Usually, this scheme starts with a phishing site that contains a fake Microsoft Security Warning. This leads to the victim calling the scammers, hoping to get help solving the “problem”. They may use a variety of techniques to gain the attention and trust of potential victims. But, sometimes, scammers call random users and claim that the user’s computer has serious problems, viruses, or security breaches and offer to help resolve them.
To “help” users, scammers may ask permission to control the computer remotely. If the user agrees, attackers gain full access to the system and can install malware or steal personal data. In addition, scammers often ask the user to provide personal information such as credit card numbers, passwords, addresses, and other sensitive information.
How To Avoid These Scams?
To avoid falling victim to phishing scams like the ones abusing Azure Static Web Apps, it’s essential to follow the next practices for online security and remain vigilant. Here are some steps you can take to protect yourself:
- Check URLs before entering data. You should check the URL in the address bar when you’re asked to enter your account credentials on a login page. Look for any unusual subdomains or misspellings that could indicate a phishing site. Ensure that the domain is the official one for the service you’re using.
- Be careful with suspicious emails. Please don’t click on links or download attachments from unsolicited or unexpected emails. Always verify the legitimacy of an email, even if it appears to come from a trusted source.
- Verify the Source. When you receive an email requesting sensitive information or actions, contact the supposed sender directly through official channels to verify the request’s authenticity.
- Use a Password Manager. Thus, you can create strong, unique passwords for your online accounts. This prevents a single compromised password from affecting multiple accounts.
- Enable Two-Factor Authentication. Whenever possible, enable 2FA for your online accounts. This adds another layer of security and requires a second form of verification, such as a temporary code sent to your phone.
- Educate Yourself. It is crucial to keep yourself updated on the latest phishing techniques and common scam tactics to stay informed and protected. Be vigilant and cautious while browsing the internet or dealing with suspicious emails or messages. The more you know, the better you can protect yourself.
- Use Security Software. We recommend installing reputable anti-malware solutions on your devices. It can help detect and block malicious websites and emails.
- Keep Software Updated. Keep your operating system, web browsers, and security software up-to-date. This ensures that any known vulnerabilities are fixed.
By following these precautions and maintaining a healthy level of skepticism, you can significantly reduce the risk of falling victim to phishing scams. Cybercriminals continuously adapt their tactics, so staying vigilant is essential to your online security.




