
Multi-Factor Authentication
Multi-Factor Authentication or MFA is a user identification that requires the user to provide two or more identity verification factors to access a resource. This can be an application, an Internet account, or a VPN. MFA is a core component of a strict Identity and Access Management (IAM) policy. The primary goal of MFA is to create a layered defense that will prevent an unauthorized person from accessing a target, such as a physical location, computing device, network, or database. Even if one factor is compromised, an attacker still has at least one or more barriers to overcome before successfully penetrating a target.
Why is MFA used?
One of the most significant disadvantages of traditional login with a user ID and password is that passwords can be easily compromised, costing organizations millions of dollars. In addition, brute force attacks are a real threat, as attackers can use automated tools to crack passwords. Thus, the program will try different combinations of usernames and passwords until it finds the correct sequence. Hackers still have many other ways to access the system, even if the targeted security system locks an account after several incorrect login attempts. This is why multifactor authentication is so important, as it can help reduce security risks.
How Does MFA work?
In a classic scheme, users need to enter their username and password when they log into an account. In the case of multifactor authentication, the system will prompt them to verify their identity, usually with several options available. These might include sending a one-time password (OTP) via SMS or an authentication app, or the special app to enter biometric information such as a fingerprint or facial scan. Some corporate organizations may want users to authenticate with a physical token, such as a key or reader card. Many corporate MFA solutions also support adaptive authentication. This type of authentication makes it easier for users to gain access to critical systems without compromising account security.
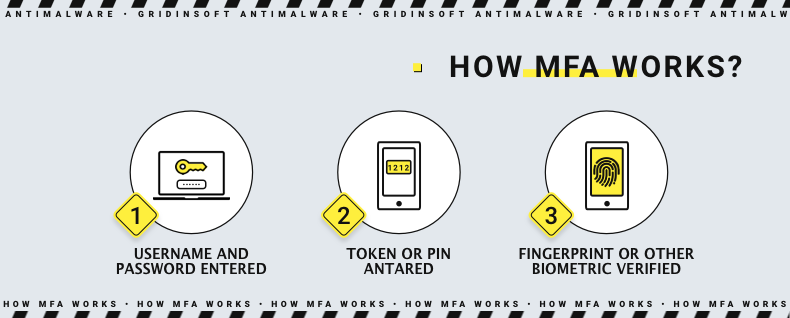
What are the types of MFA?
In general, MFA authentication methods can be divided into three categories. All of the remaining methodologies are based on one of these three types:
Things you know (knowledge)
Knowledge-based authentication usually requires the user to answer a personal control question. Knowledge factor techniques typically include passwords, four-digit personal identification numbers (PINs), and one-time passwords (OTPs). Typical user scenarios include the following:
- Reading a debit card and entering the PIN at the checkout counter at the grocery store;
- Downloading a VPN client with a valid digital certificate and logging into a VPN before gaining access to the network;
- Providing information, such as the mother's maiden name or previous address, to gain access to the system.
Things you have (possession)
To log in, the user must carry something specific, such as a badge, token, key fob, or SIM card with the caller ID module. For mobile authentication, the smartphone often provides a possession factor in combination with the OTP application. Possession factor technologies include:
- Security tokens are small hardware devices that store a user's personal information and are used to identify that person electronically. The device can be a smart card, a chip embedded in an object, such as a USB drive, or a wireless tag.
- The software security token application creates a one-time PIN to log in. software tokens are often used for mobile multi factor authentication, where the device, such as a smartphone, provides ownership factor authentication.
- Typical user possession factor scenarios include mobile authentication, where users receive a code through their smartphone to gain or grant access. Options include text messages and phone calls sent to the user as an out-of-band method, smartphone OTP applications, SIM cards, and smart cards with stored authentication data. It may also suppose connecting a hardware USB token to a desktop that generates OTP and using it to log into the VPN client.
Things you are (inalienability)
This can be any biological traits of the user confirmed at login. In addition, affiliation factor technologies include the following biometric verification methods:
- Retinal or iris scans;
- Fingerprint scanning;
- Voice authentication;
- Face recognition;
- Hand geometry;
- Digital signature scanners;
- Earlobe geometry.
The components of the biometric device include a reader, a database, and software to convert the scanned biometric data into digital data and to compare matching points between the observed data and the stored data. Typical inalienability factor scenarios include the following:
- Using fingerprint or facial recognition to access a smartphone;
- Providing EDS at a retail cash register;
- Identifying the perpetrator by earlobe geometry;
Other Types of Multi-Factor Authentication
Another subspecies of MFA is adaptive authentication, also called risk-based authentication. Adaptive authentication analyzes additional factors, taking into account context and authentication behavior, and often uses these values to determine the level of risk associated with a login attempt. For example:
- Where was the attempted access to information made?
- When was the attempted access to company information made? (I.e. during working hours or in after hours)
- What device is being used? (I.e. same as usual or different)
- Is the connection through a private network or a public network?
Based on the answers to these questions, the risk level is calculated, and the system decides whether the user will be asked to enter an additional authentication factor or will be allowed to log in. When using adaptive authentication, the user only needs to enter a username and password when logging in from the office as workday starts. However, a user who logs in from a coffee shop late at night, which is not typical, may need to enter a code sent in a text message to his phone, in addition to standard authentication.
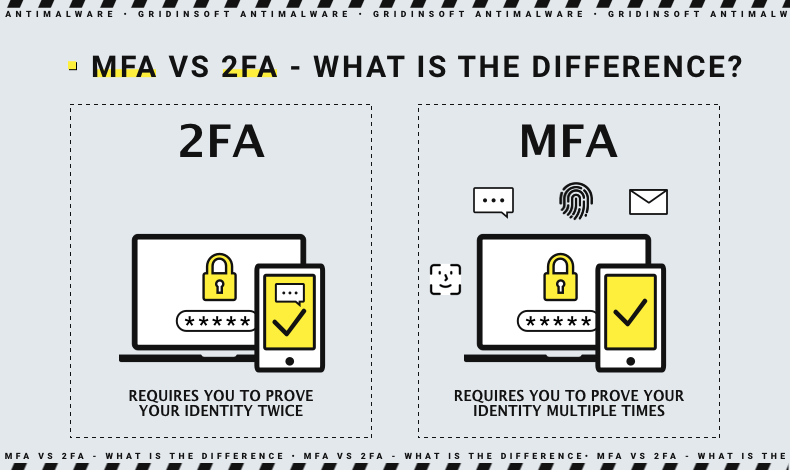
Difference between MFA and Two-Factor Authentication (2FA)
MFA is often equated with two-factor authentication (2FA). They are similar, but 2FA is a simplified subspecies of MFA because 2FA limits the number of required factors to only two, whereas MFA can be two or more. MFA is a broader practice, which accepts several possible ways to authenticate the user, and thus more relevant for corporation-scale cybersecurity solutions. Two-factor authentication is generally easier to establish and maintain, as you should not keep all possible information needed for authorization. It get a widespread application for sole users' cybersecurity approaches.
What are the pros and cons of MFA?
Multi-factor authentication was introduced to increase the security of access to systems and applications through software and hardware. The goal was to identify users' identities and guarantee the integrity of their digital transactions. The disadvantage of MFA is that users often forget the answers to the control questions that confirm their identity, and some users exchange personal identifiers and passwords. MFA has both advantages and disadvantages.
Pros
- Adds additional layers of security at the hardware, software, and personal identification levels;
- Can use one-time passwords sent to phones that are randomly generated in real-time and difficult for hackers to crack;
- Can reduce security breaches by up to 99.9% compared to passwords alone;
- Users can easily customize it;
- Allows businesses to restrict access based on specific characteristics, such as time of day or location;
- It is scalable in cost, as there are both expensive and complex MFA tools and more affordable ones for small businesses.
Cons
- Requires a phone to receive a text message code;
- Hardware tokens can be lost or stolen;
- Phones can also be lost or stolen;
- Biometric data by MFA algorithms for personal identifiers, such as fingerprints, are not always accurate and may create false positive or negative results;
- MFA checks may fail in the absence of the Internet;
- MFA methods must be continually improved to protect against criminals who work tirelessly to hack them.
The future of MFA: AI, ML, and more
Multi-factor authentication is constantly evolving, providing more secure access for organizations and sometimes being inconvenient for users. But, again, biometrics is the optimal solution. It's safer because it's difficult to tamper with a fingerprint or face. After all, the user doesn't have to remember everything (such as a password) or make any other effort. Here are some of the advances shaping multi-factor authentication today.
Artificial Intelligence (AI) and Machine Learning (ML) - AI and ML can be used to recognize behavior, indicating whether a given access request is "normal" and therefore requires no additional authentication (or conversely, to identify abnormal behavior). This, in particular, is currently performed with the help of user behavior analytics (UBA).
Fast Identity Online (FIDO) - FIDO authentication is based on the FIDO Alliance's set of free and open standards. It allows you to replace login with a password with a secure and fast login to websites and applications.
Passwordless authentication. Instead of using a password as the primary method of identity verification and supplementing it with other non-password methods, password-free authentication eliminates passwords as a form of authentication.
Rest assured that multi-factor authentication will continue to change and improve in finding ways for people to verify their identity - reliably and without jumping through hoops.
Frequently Asked Questions
SSO, or Single Sign-On, is a login mechanism where the user logs into a single account that is considered safe. After that it has the ability to use all the sites and services that are related to the login account without the need to log in once again. SSO is applied in a chain of services from Google and Bing.
Meanwhile, MFA is about asking for several identity confirmations before letting the user in. It is also about the login way, but supposes much less trust and fits better at the places that does not suppose the trusted login. Still, they may be combined (first you log in with MFA, then you can use all services with SSO).
