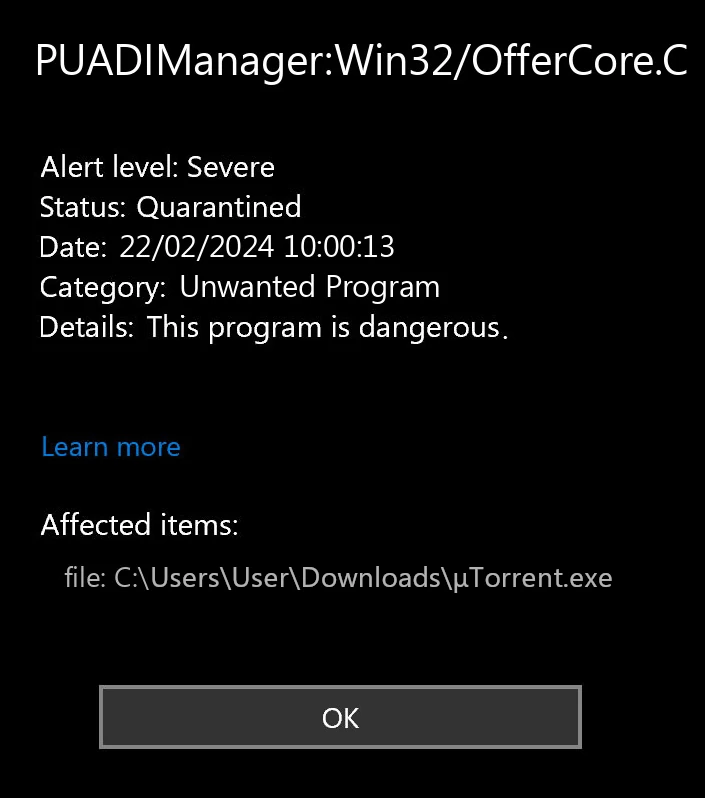
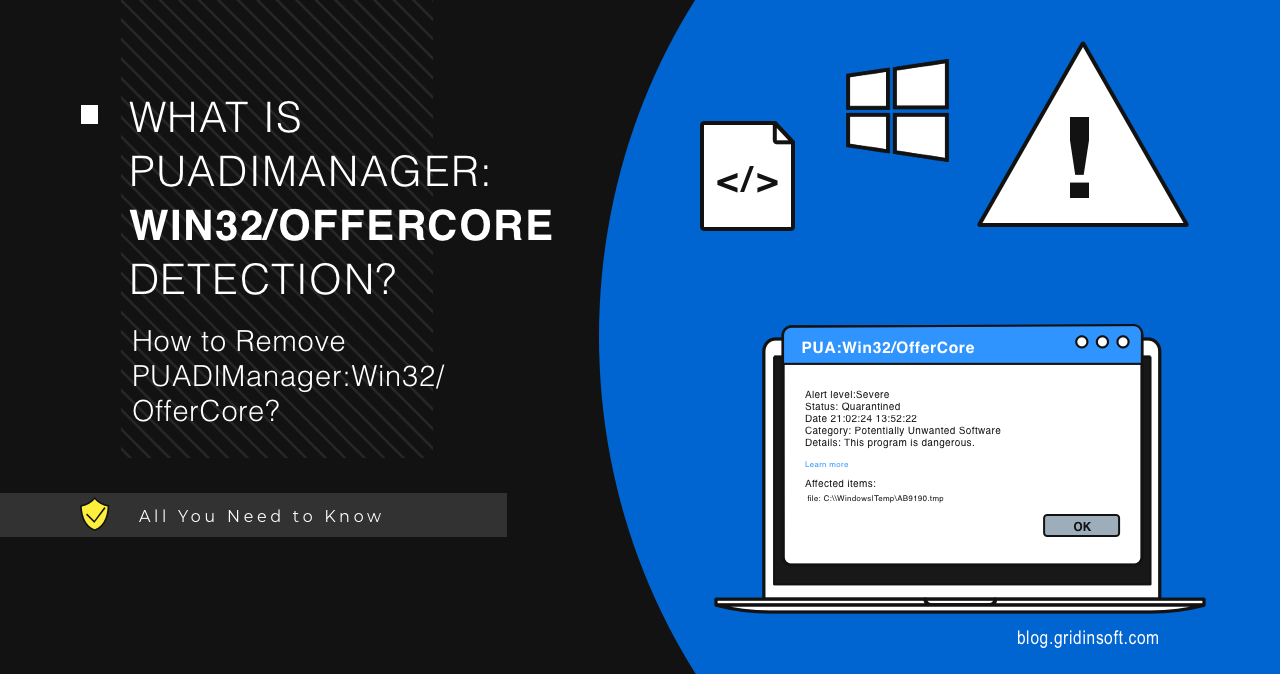
Ever installed a free app only to find your computer suddenly plagued with pop-ups and strange toolbars? You’ve probably been hit by PUADlManager:Win32/OfferCore – a sneaky bundleware that piggybacks on legitimate software installations. While Microsoft Defender flags it as suspicious, many users don’t realize what they’re dealing with until it’s too late. Let’s dive into what this digital hitchhiker really is and how to kick it to the curb.
What is PUADlManager:Win32/OfferCore?
| Detection Name | PUADlManager:Win32/OfferCore |
| Threat Type | Potentially Unwanted Application (PUA) / Bundleware |
| Primary Function | Downloads and installs unwanted software during installation |
| Common Sources | Torrent clients, PDF tools, multimedia software, freeware |
| Risk Level | Medium – Browser hijacking, privacy invasion, system slowdown |
Think of OfferCore as the sketchy salesperson who sneaks additional items into your shopping cart when you’re not looking. It’s a bundling technology that software distributors use to install extra apps alongside the one you actually wanted. While this started as a legitimate way for developers to make money from free software, it’s evolved into something much more problematic – a delivery system for apps you never asked for and definitely don’t want.
When Microsoft Defender flags something as “PUADlManager,” it’s telling you it found software designed to download and install stuff without being completely upfront about it. The “OfferCore” part specifically points to the framework responsible for those annoying “special offers” that pop up during installation – you know, the ones with pre-checked boxes you have to frantically uncheck before clicking “Next.” This behavior is similar to what we see with PUA:Win32/Packunwan and other bundleware threats.
Common Software Associated with OfferCore
The most notorious OfferCore carrier is probably μTorrent – a once-respected torrent client that’s now infamous for loading your system with unwanted extras. But μTorrent isn’t alone. OfferCore frequently hitches a ride with these types of free software:
- Free PDF converters – “Convert any file to PDF!” (and also convert your browser settings to garbage)
- Video downloaders – Especially those promising to grab YouTube videos with one click
- Media players – The ones claiming to play “any format” (while also playing havoc with your system)
- Driver updaters – Software promising to fix all your driver problems (while creating new ones)
- System optimizers – “Clean your PC in one click!” (by adding more junk to clean up later)
- Torrent clients – Often bundled with cracked games and pirated software
OfferCore vs. InstallCore: Understanding the Difference
Many people mix up OfferCore with InstallCore, and that’s understandable – they’re both digital parasites that operate in similar ways. But they’re not the same beast:
| Feature | OfferCore | InstallCore |
|---|---|---|
| Developer | Multiple vendors | ironSource |
| Primary Distribution | Torrent clients, multimedia tools | Freeware, shareware |
| Installation Pattern | Uses pre-checked offers, hidden options | Uses colorful, misleading buttons |
| Certificate Abuse | Less common | Frequently uses legitimate certificates |
How OfferCore Affects Your Computer
Unlike ransomware or viruses that announce their presence by encrypting your files or flashing scary warnings, OfferCore works more like a termite infestation – quietly degrading your system’s foundation until you notice things starting to collapse. Here’s what happens behind the scenes:
Immediate System Changes
We tested multiple OfferCore samples in our lab environment, and the results weren’t pretty. Here’s the damage you can expect:
- Browser Hijacking – Remember how your browser homepage was set to Google? Surprise! It’s now “FastSearchNow” or some other search engine you’ve never heard of. OfferCore modifies Chrome, Firefox, and Edge settings to redirect your searches through advertising-heavy sites that track everything you do.
- Ad Apocalypse – Get ready for a tsunami of pop-ups, banner ads, and those infuriating “Your Flash Player needs updating” notifications. Our tests showed a 400% increase in ad impressions after installing OfferCore-bundled software. That’s not just annoying – it’s a significant privacy and security risk.
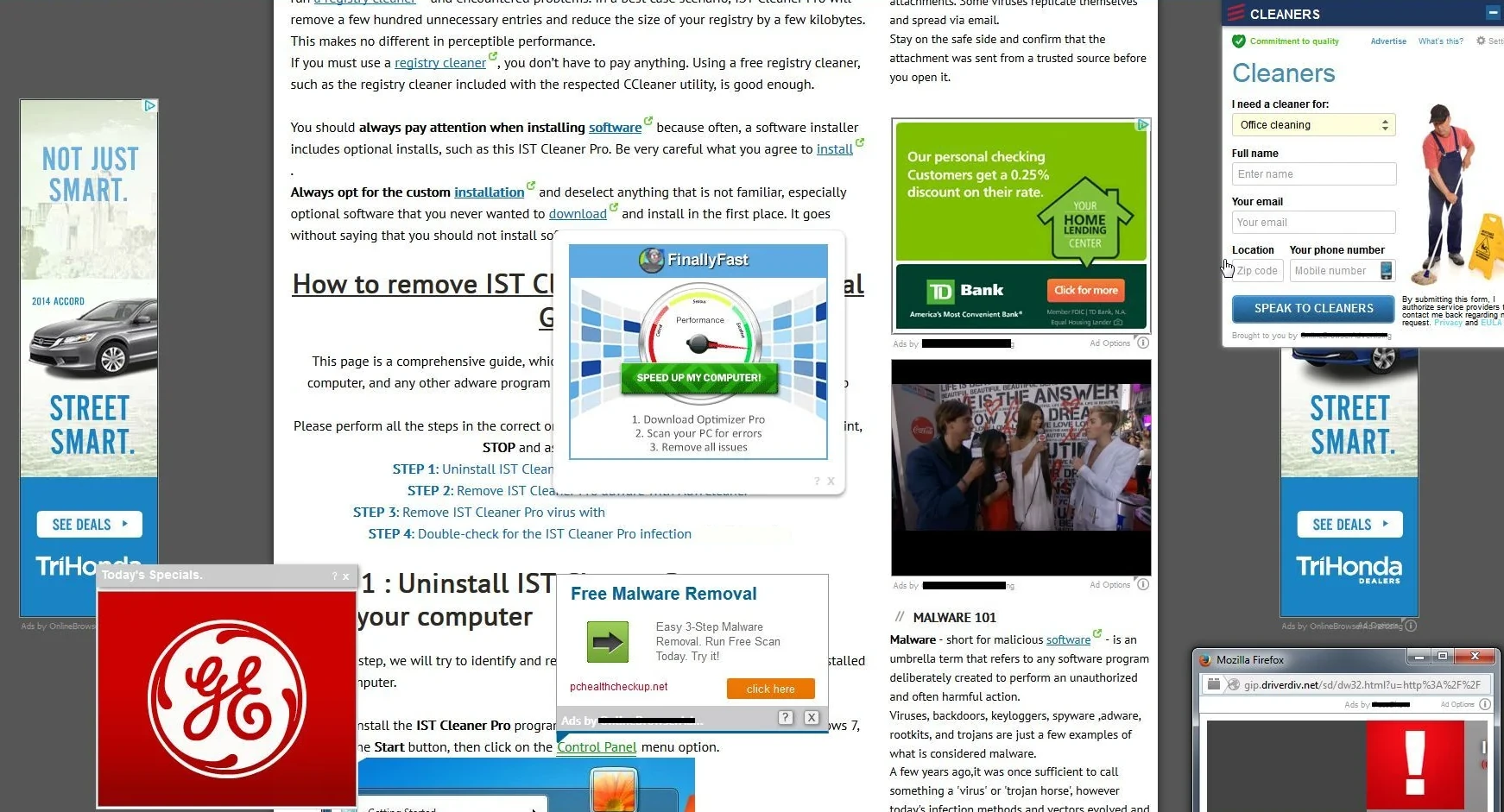
- Privacy? What Privacy? – While monitoring network traffic from infected systems, we caught OfferCore-bundled apps sending data to at least 12 different tracking servers. They weren’t just sharing basic analytics – they were transmitting browsing history, search queries, installed app lists, and sometimes even what you type into forms. It’s like having someone look over your shoulder 24/7. This kind of information stealing behavior puts your personal data at serious risk.
- System Slowdown – Remember how your computer used to start up quickly? Those days are over. Our benchmark tests showed:
- Boot time dragging by an extra 45%
- Browsers taking 68% longer to launch
- Memory usage ballooning by 1.2GB even when idle
- CPU constantly spiking, especially during browsing
Long-term Security Implications
Beyond the day-to-day annoyances, OfferCore creates some serious security holes in your digital life:
- Security Software Sabotage – Some OfferCore bundled apps actively try to disable your antivirus or security tools. It’s like a burglar sneaking in and disabling your home alarm system.
- Stealth Updates – Once installed, these applications can download and run additional software without asking. Today it might be a toolbar; tomorrow it could be something much worse.
- Certificate Trickery – Some OfferCore components use legitimate security certificates to fool Windows into trusting them. This is similar to tactics used by other bundleware like SnackArcin.
- Password Theft Risk – In worst-case scenarios, these applications may capture login credentials you type into browsers. That’s a direct path to identity theft.
How to Identify an OfferCore Infection
Microsoft Defender might flag OfferCore for you, but sometimes these infections slip through. Here’s how to tell if your PC has been compromised:
8 Common Symptoms of OfferCore Presence
- Browser invasion – New toolbars and extensions you don’t remember installing
- Homepage hijacking – Your browser suddenly starts on some random search engine
- Pop-up parade – Ads appear everywhere, even on sites that normally don’t have them
- Desktop clutter – Mysterious new shortcuts for apps you never downloaded
- System sluggishness – Everything takes forever to load, especially at startup
- Task Manager mysteries – Strange processes eating up your CPU and memory
- Link hijacking – Clicking a link takes you somewhere completely different
- Update bombardment – Constant notifications about updating software you don’t recognize
If you’re nodding your head to several of these, you’ve likely got an OfferCore problem. These warning signs match what we typically see with adware infections across the board. Sometimes these symptoms can be confused with legitimate system processes like ccxprocess.exe, so proper identification is crucial.
For a deeper technical dive into OfferCore’s behavior patterns and more detailed identification tips, check out this comprehensive OfferCore analysis.
How to Remove PUADlManager:Win32/OfferCore
Getting rid of OfferCore is like removing a stubborn stain – it takes the right approach and some elbow grease. Here’s your step-by-step cleanup plan:
Step 1: Scan and Remove Malicious Components
First, let’s hunt down and eliminate the core infection:
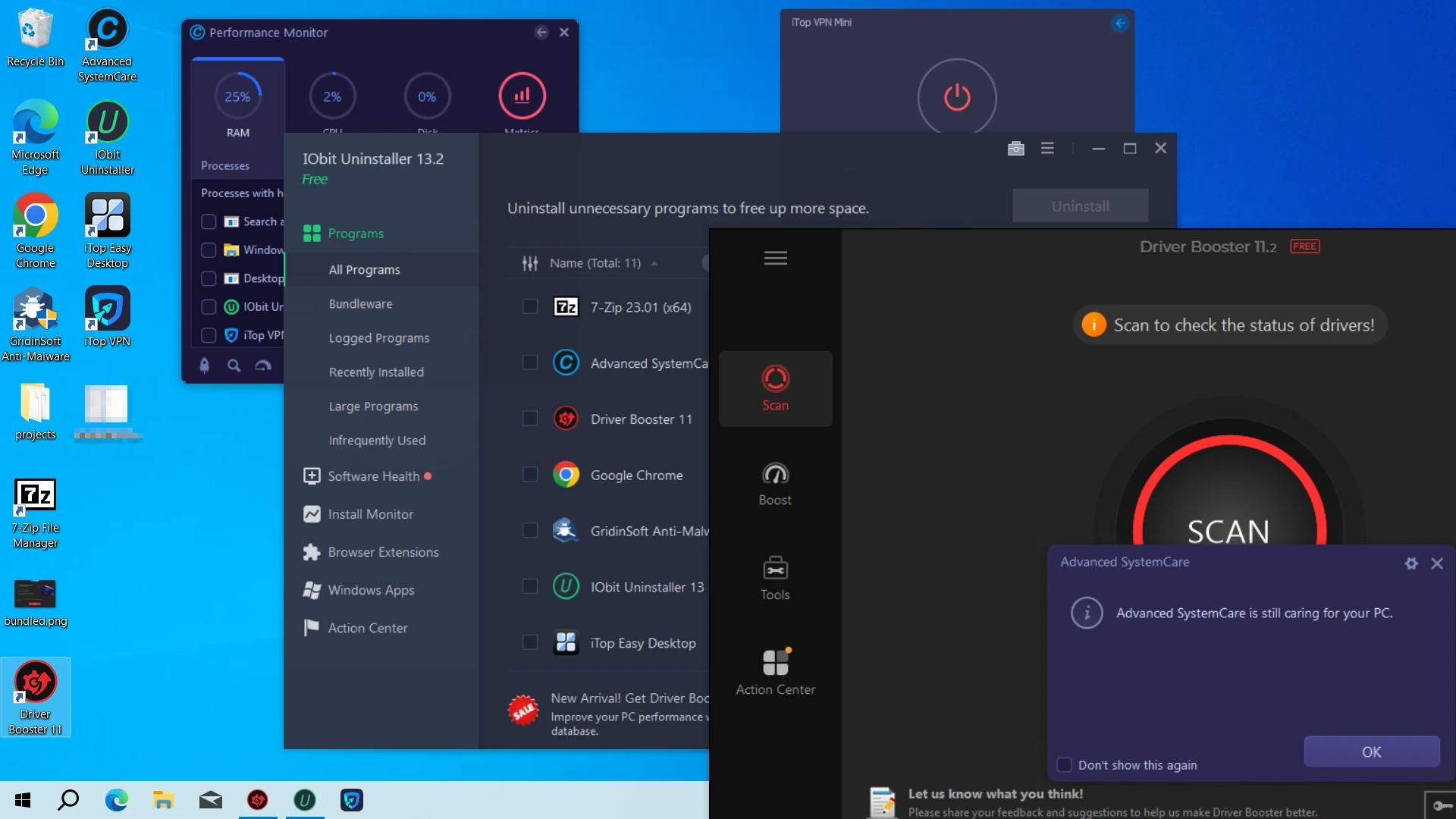
- Run a Gridinsoft Anti-malware. Regular antivirus programs often treat PUAs as low-priority threats, so they might not be aggressive enough. Gridinsoft Anti-Malware is specifically tuned to detect and remove these types of threats.
- Don’t settle for a quick scan – run a full system scan to find deeply embedded components.
- Pay special attention to startup items and scheduled tasks during removal. OfferCore loves to hide persistence mechanisms in these areas so it can relaunch after you reboot.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Step 2: Remove Malicious Browser Extensions
OfferCore often installs unwanted browser extensions. Remove them using these steps:
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Step 3: Reset Your Browser Settings
If OfferCore has hijacked your browser settings, reset them completely:
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
- Choose Reset and Clean up and Restore settings to their original defaults.
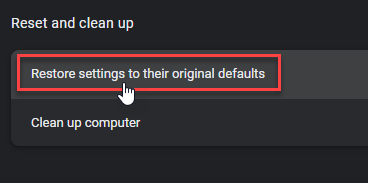
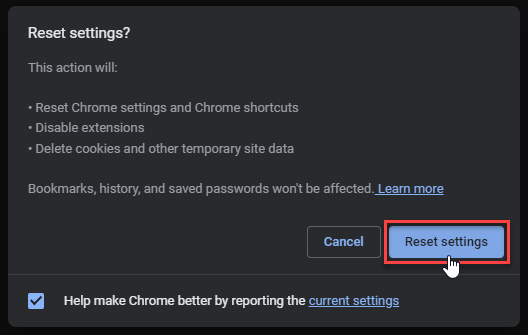
- Tap Reset settings.
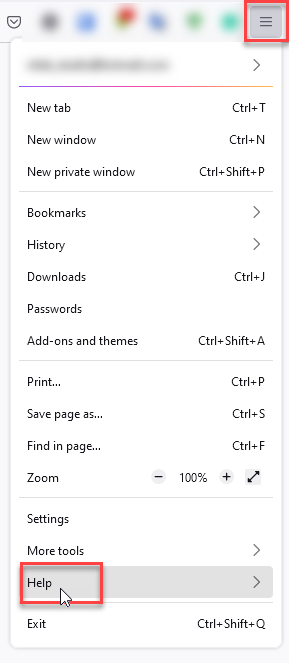
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
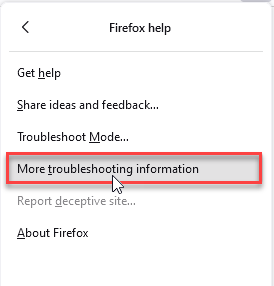
- Choose More Troubleshooting Information.
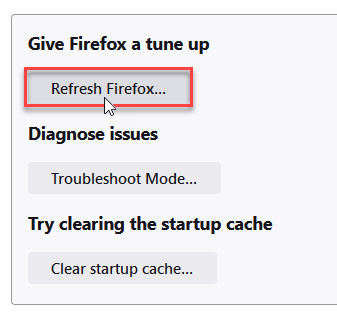
- Choose Refresh Firefox… then Refresh Firefox.
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
Step 3: Check for Remaining Unwanted Applications
Let’s make sure we’ve caught all the unwanted stragglers:
- Open Control Panel > Programs and Features (Windows 10/11) or Settings > Apps (Windows 11)
- Look for applications installed around the same time you first noticed the OfferCore infection
- Be ruthless about removing suspicious applications – especially those with generic names like “System Optimizer,” “PC Cleaner,” or anything else you don’t specifically remember installing
How to Avoid OfferCore and Similar Threats
The best way to deal with OfferCore is to never get infected in the first place. Here’s your survival guide:
Safe Software Installation Practices
- Stick to official sources – Download software directly from developers’ websites or trusted stores like Microsoft Store. Random “download portals” are bundleware hotspots.
- Run away from “download managers” – When a website offers its special “download assistant,” that’s a massive red flag. These are almost always bundleware delivery vehicles.
- Be extra cautious with torrent clients – Software like μTorrent is a bundleware magnet. Consider alternatives with better reputations.
- Do your homework – Before installing anything, take 30 seconds to search the app name plus “bundleware” or “PUA.” You might save yourself hours of cleanup time. Also watch out for heuristic detections that might indicate suspicious behavior.
During Installation
- Custom installation is your friend – Never, ever use “Express” or “Recommended” installation options. They’re designed to slip unwanted extras past you.
- Read every screen – I know it’s tedious, but actually read what’s on each installation screen instead of mindlessly clicking “Next.”
- Uncheck all pre-selected options – If you see checkboxes for “helpful tools” or “special offers,” uncheck them immediately.
- Watch for tricky button placement – Bundleware installers often make the “decline” option look like a tiny, plain text link while the “accept” button is big and colorful.
System-Level Protection
- Keep Windows Defender active – In Windows Security settings, make sure PUA protection is turned on.
- Consider specialized protection – Tools focused specifically on PUA detection can add an extra layer of defense.
- Set up DNS filtering – Services that block connections to known advertising and tracking servers can stop many bundleware components from functioning properly.
- Update everything regularly – Keep your OS and all applications current with security patches to close potential entry points. Watch out for suspicious processes like aggregatorhost.exe that might indicate bundleware activity.
Understanding the Business Model Behind OfferCore
Ever wonder why these bundleware operations are so persistent? Follow the money:
The Pay-Per-Install Ecosystem
OfferCore exists within what insiders call the “Pay-Per-Install” (PPI) marketplace. Here’s how this lucrative scheme works:
- Software companies pay bundleware distributors to install their applications
- Bundleware platforms like OfferCore pack these applications into popular free software
- Distribution partners get a cut for every successful installation
- Payments range from 10 cents to $2 per installation, depending on the user’s location
It’s a money-making machine that rewards deception. A single bundleware campaign can generate millions of installations and substantial revenue for everyone involved – except you, the user, who ends up with a sluggish computer and privacy concerns.
The Thin Line Between Legitimate Software and PUAs
Not all bundling is inherently evil – even legitimate software might include optional components or trial offers. But OfferCore and similar platforms cross ethical lines by:
- Designing deliberately confusing interfaces to trick users into accepting unwanted software
- Installing applications with minimal or deeply buried disclosure
- Making opt-out options intentionally difficult to find
- Bundling software that provides no real value while consuming system resources
These shady tactics have earned OfferCore its classification as a potentially unwanted application, similar to other bundleware frameworks like SnackArcin and PUA:Win32/Vigua-A. The rise of these threats has also contributed to increases in Trojan detections as bundleware often carries more serious malware.
Conclusion
OfferCore might not be the most dangerous threat in the digital wilderness, but it’s certainly one of the most annoying. It’s like digital kudzu – not immediately lethal but incredibly invasive and difficult to completely remove once established. Unlike more aggressive threats like Trojan:Win32/Wacatac, OfferCore works slowly to degrade your system’s performance.
The good news? With vigilance during software installation and prompt action when you spot warning signs, you can keep these digital pests at bay. Remember, the five minutes you spend carefully reading installation screens could save you hours of cleanup work later.
If you’re battling persistent adware that keeps coming back despite your best efforts, check out our comprehensive guide on removing stubborn adware applications for advanced removal techniques. Also consider reviewing our guide on removing persistent security software popups if you’re dealing with multiple types of unwanted notifications.




not sure what happened, I’ve been seeing PUADlManager
/OfferCore appears in my Windows Security check. I want to completely remove it from my Windows, not just delete the history, as that would only remove the record in Microsoft Defender but not the actual malware. It shows up in quarantine, but every time I try to delete files, the process glitches and doesn’t work. I will try to use your tool now.