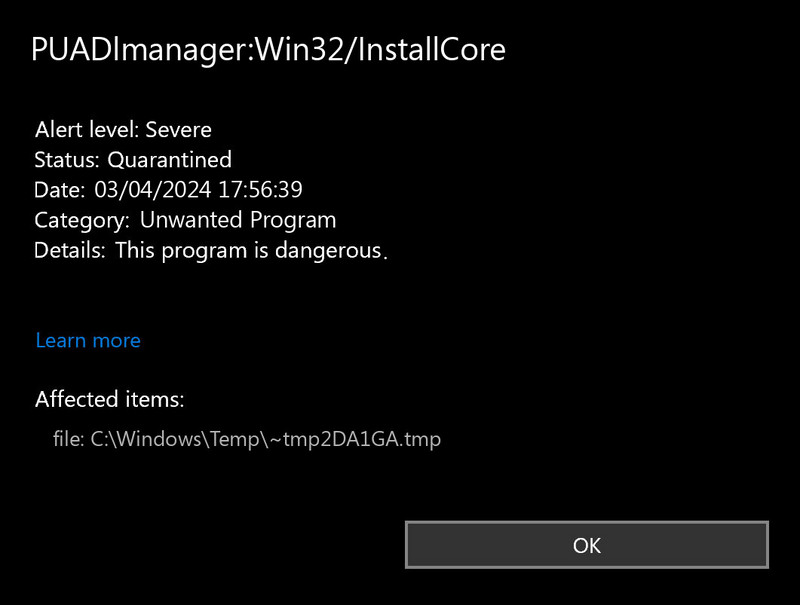
PUADlmanager:Win32/InstallCore is a detection that Windows Defender antivirus uses to identify potentially unwanted applications (PUAs). This problematic software combines the functions of a downloader and installer, automatically distributing numerous unwanted applications and potentially dangerous programs to infected systems. While it may not initially appear as serious as other threats, the cumulative effects of InstallCore’s activities can significantly degrade your system performance, bombard you with unwanted advertisements, and potentially expose your computer to more severe security risks.
What is PUADlmanager:Win32/InstallCore?
PUADlmanager:Win32/InstallCore is not a standalone program but rather a bundling technology integrated into software installers. The “PUADlmanager” prefix (Potentially Unwanted Application Download Manager) clearly indicates its primary function: to download and install additional software without explicit user consent. When you launch an installer infused with InstallCore, it activates in the background, ready to deploy its payload of unwanted applications.
This bundling technique is primarily used as a monetization strategy by software distributors. By partnering with third-party software companies, distributors earn commissions for each successful installation of bundled applications. Unfortunately, these additional applications are typically adware, browser extensions with questionable functionality, system “optimization” tools, or other potentially unwanted programs that provide little value while consuming system resources and compromising user experience.
InstallCore is commonly found embedded in pirated software, freeware download packages, and questionable software distribution platforms like Softonic, Download.com and FileHippo. Its prevalence has made it one of the most frequently detected potentially unwanted applications on Windows systems.
Source: Data compiled from multiple cybersecurity reports, 2024-2025
Is InstallCore a False Positive?
False positive detections of PUADlmanager:Win32/InstallCore can occur in certain scenarios. The boundary between legitimate software bundling and potentially unwanted activity is sometimes blurry, leading to occasional misclassifications by security software. InstallCore generally falls into a “gray” category of software that, while not as dangerous as outright malware, still exhibits behaviors that security researchers consider problematic.
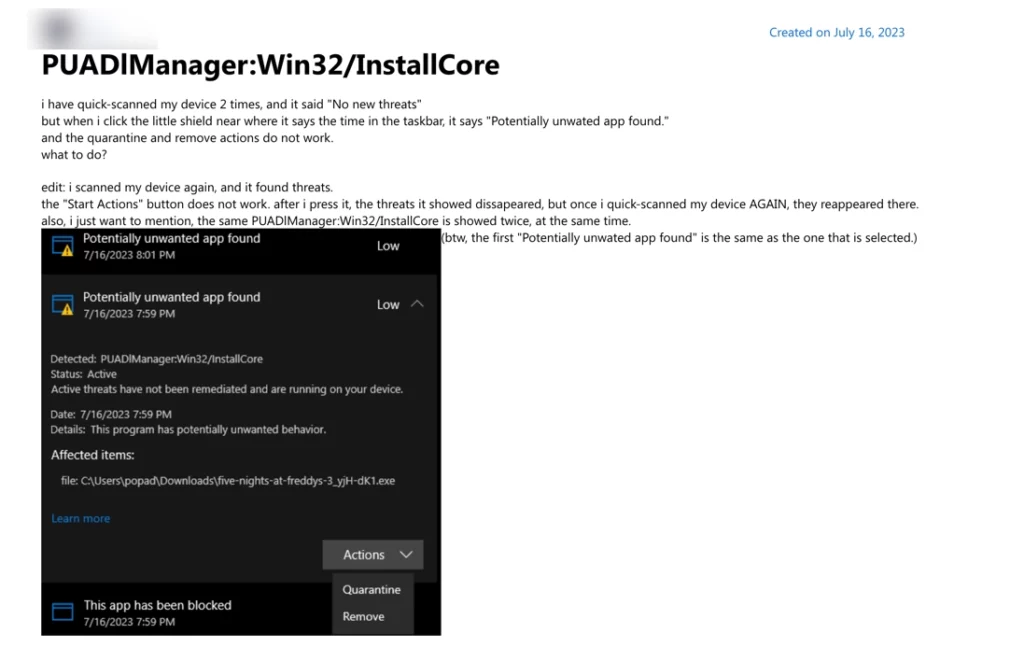
Discussions on the Information Security Stack Exchange forum indicate that false positives can be related to security signature updates or when installing certain third-party software that legitimately uses bundling technologies. Another example was documented on the JDownloader Community forum, where Windows Defender incorrectly flagged JDownloader.exe as malicious. In that case, the JDownloader developers confirmed their software was clean and encouraged users to report the false positive to Microsoft.
There was also a discussion on the Microsoft forum about a false positive detection in the Five Nights at Freddy’s game installer, further illustrating that legitimate software can sometimes trigger InstallCore alerts.
| Characteristic | Legitimate Bundling | Potentially Unwanted (InstallCore) |
|---|---|---|
| User Consent | Clear opt-in checkboxes, transparent disclosure | Hidden options, pre-checked boxes, misleading instructions |
| Installation Process | Additional software clearly identified during installation | Background installations without notification |
| Software Quality | Bundled with relevant, useful applications | Bundled with adware, browser hijackers, “system optimizers” |
| Uninstallation | Clean, straightforward removal process | Difficult to remove completely, leaves registry traces |
| Business Model | Transparent affiliate marketing | Aggressive monetization through intrusive ads and data collection |
It’s important to understand that antivirus programs regularly update their malware signature databases. Sometimes, these updates can temporarily misclassify safe files as malicious. However, many users overlook the additional software that installers offer during installation. If these bundled applications meet the criteria for PUA/PUP classification, Windows Defender will appropriately flag them as potentially unwanted.
How does PUADlmanager:Win32/InstallCore affect my computer?
The primary concern with PUADlmanager:Win32/InstallCore is its ability to download and install numerous unwanted programs without user consent. To better understand its impact, I tested several applications flagged by Windows Defender as containing InstallCore.
System Performance Degradation
In one test case, I encountered an application advertised as a file download manager with special capabilities for torrents. Despite its attractive interface, the application provided no actual functionality – it was merely a shell designed to deliver bundled software. Upon installation, numerous additional programs began installing automatically, including:
- Driver updater utilities with limited functionality
- “Free” VPN services that collect user data
- System optimization tools that often flag normal system files as “problems”
- Browser extensions that modify search results and inject advertisements
The cumulative effect of these unwanted installations was a significant reduction in system performance. The virtual machine used for testing became exceptionally sluggish, with increased CPU usage, memory consumption, and disk activity from multiple unnecessary background processes.
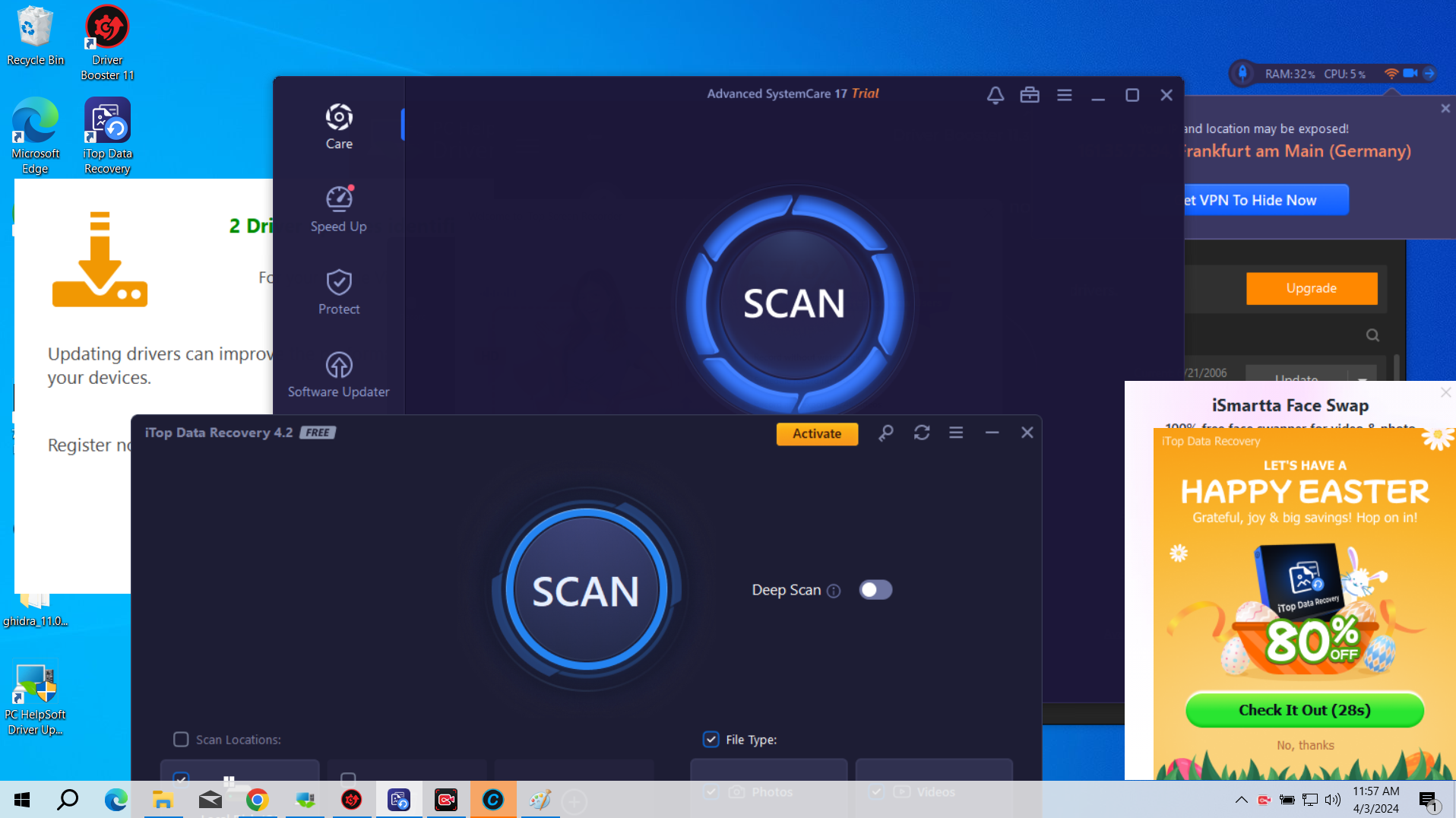
Intrusive Advertisements
Another significant consequence of InstallCore activity is the proliferation of unwanted advertisements. The bundled adware components modify browser settings and inject advertisements into web pages, creating a disruptive browsing experience. These advertisements appeared both within web browsers and as system notifications in the taskbar, continuing until the malicious components were removed.
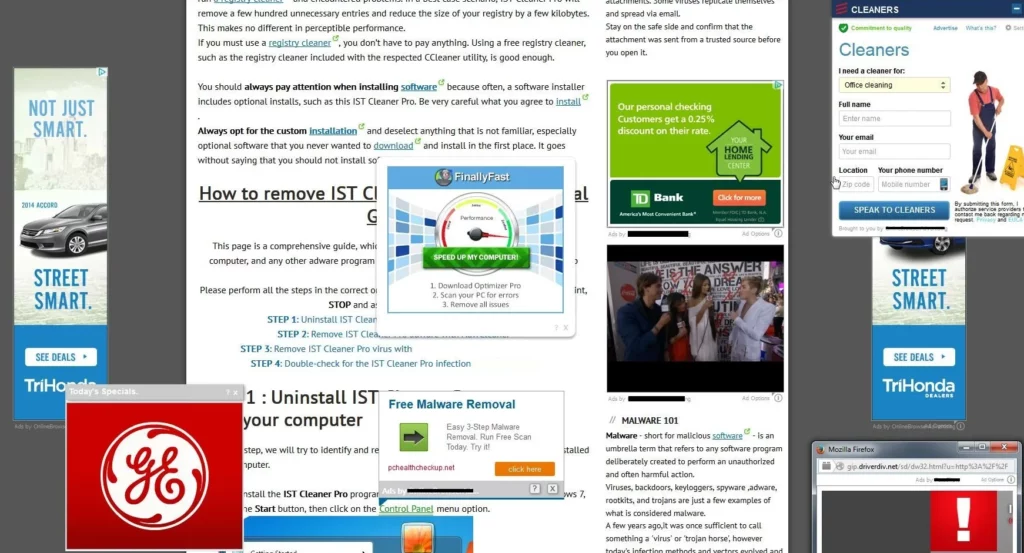
Browser Modifications and Security Risks
InstallCore-bundled software often attempts to modify browser settings and install extensions without clear user consent. During testing, I observed pop-ups promoting questionable browser extensions, including a known browser hijacker called Dragon Angel. While browser extensions might seem relatively harmless, they can pose significant security risks by functioning as information stealers or cryptocurrency hijackers.
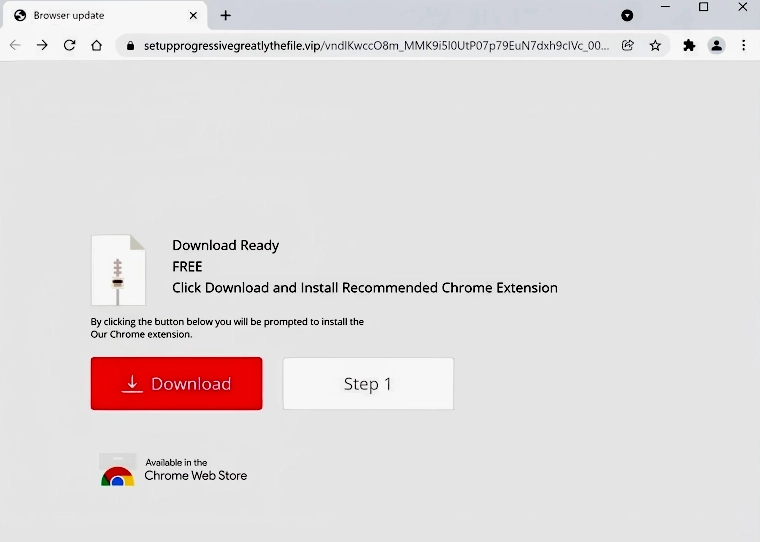
While PUADlmanager:Win32/InstallCore may not be classified as severe malware, its effects significantly degrade system performance and user experience. The unwanted applications it installs consume system resources, bombard users with advertisements, modify browser settings, and potentially create security vulnerabilities that could lead to more serious infections. For these reasons, prompt removal is strongly recommended.
Technical Analysis of InstallCore Behavior
Understanding how InstallCore operates can help users identify and avoid this potentially unwanted application. Let’s examine the technical aspects of its behavior:
Installation and Execution Flow
InstallCore typically follows a multi-stage execution process:
- Initial Execution: When a user launches an installer bundled with InstallCore, the primary executable initiates both the legitimate application installation and the InstallCore component.
- Environment Analysis: InstallCore examines the system environment, checking for security software, virtual machines, or analysis tools that might detect its activity.
- Component Download: If conditions are favorable, InstallCore connects to remote servers to download additional payloads.
- Silent Installation: Using elevated privileges (if granted during the initial installation), InstallCore installs additional software components with minimal or misleading user notifications.
- Cleanup and Concealment: After installation, temporary files may be removed to hide evidence of the bundling process.
System Modifications
InstallCore and its bundled applications typically make several changes to maintain persistence and functionality:
- Registry Modifications: Creates entries in the Windows Registry to ensure applications launch at startup, including:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Browser Extensions: Installs browser add-ons that can intercept web traffic, inject advertisements, or redirect search queries.
- Proxy Settings: May modify system or browser proxy settings to route web traffic through servers that can inject advertisements or collect browsing data.
- Task Scheduling: Creates scheduled tasks to periodically check for updates or download additional components.
Network Communication
InstallCore maintains communication with remote servers for several purposes:
- Command and Control: Receives instructions about which additional software to download and install.
- Telemetry Collection: Sends system information and usage statistics to remote servers.
- Update Mechanisms: Checks for and downloads updates to bundled software or the InstallCore framework itself.
- Advertisement Delivery: Communicates with ad networks to fetch and display advertisements.
This network activity often occurs in the background and may continue long after the initial installation, contributing to ongoing system impact and privacy concerns.
How to Remove PUADlmanager:Win32/InstallCore from PC?
Removing PUADlmanager:Win32/InstallCore requires a thorough approach that addresses both the core components and all bundled software it may have installed. While manual removal is possible, using specialized security software provides the most reliable results.
Automatic Removal with GridinSoft Anti-Malware
For comprehensive detection and removal of InstallCore and all associated unwanted programs, GridinSoft Anti-Malware offers an effective solution. This security software is specifically designed to identify and eliminate potentially unwanted applications and their components, providing thorough system protection.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Manual Removal Approach
If you prefer to manually remove InstallCore and its associated programs, follow these steps carefully. This process requires technical knowledge and can be time-consuming:
- Identify Installed Applications: Open Control Panel > Programs and Features to review recently installed software. Look for applications you don’t recognize or remember installing.
- Uninstall Suspicious Programs: Systematically uninstall all suspicious applications, starting with the most recently installed ones.
- Check Browser Extensions: Open each browser installed on your system and remove any unknown or suspicious extensions. Follow these paths for common browsers:
- Chrome: Menu > More Tools > Extensions
- Firefox: Menu > Add-ons and Themes > Extensions
- Edge: Menu > Extensions
- Reset Browser Settings: Reset your browsers to their default settings to remove any modified search engines, homepage settings, or other changes:
- Chrome: Settings > Advanced > Reset and clean up > Restore settings to their original defaults
- Firefox: Help (?) > Troubleshooting Information > Refresh Firefox
- Edge: Settings > Reset settings > Restore settings to their default values
- Clean Registry Entries: Use Windows Registry Editor (regedit) with caution to remove persistent entries. Look for entries related to the uninstalled applications in:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Remove Scheduled Tasks: Open Task Scheduler and look for tasks created by the unwanted applications.
- Restart Your Computer: After completing all removal steps, restart your system to ensure all changes take effect.
Keep in mind that manual removal may not catch all components, as InstallCore and its associated programs are designed to establish multiple persistence mechanisms. For this reason, using specialized security software is often the more effective approach.
Prevention and Protection Strategies
Preventing InstallCore infections requires vigilance and adherence to safe computing practices. Here are comprehensive strategies to protect your system:
Safe Software Installation Practices
- Download from Official Sources: Always obtain software directly from developers’ official websites or trusted platforms like the Microsoft Store.
- Avoid Third-Party Download Portals: Be especially cautious of sites like Softonic, Download.com, and similar platforms that often bundle additional software with their downloads.
- Skip “Free” Versions of Paid Software: Cracked or pirated software frequently contains malware, including InstallCore and other potentially unwanted applications.
- Read Installation Screens Carefully: During installation, pay close attention to all screens and options. Look for pre-checked boxes that might authorize additional software installation.
- Use Custom or Advanced Installation Options: When available, choose custom or advanced installation options rather than “express” or “recommended” settings, which often include additional bundled software.
System Security Enhancements
- Keep Windows Updated: Regular system updates help patch security vulnerabilities that might be exploited by unwanted software.
- Enable PUA Protection in Windows Security: Ensure Windows Defender’s PUA protection is enabled:
- Open Windows Security > App & browser control > Reputation-based protection settings > Potentially unwanted app blocking (toggle to On)
- Use a Comprehensive Security Solution: Implement reliable security software like GridinSoft Anti-Malware that specifically targets potentially unwanted applications.
- Configure Browser Security Settings: Enable enhanced security features in your browsers to block suspicious downloads and warn about potentially harmful websites.
User Education and Awareness
- Recognize Warning Signs: Be alert to signs of bundled software, such as:
- Installation screens with pre-checked optional software
- Rapidly advancing installation screens
- Vague terms like “recommended offers” or “additional features”
- Research Before Installing: Before downloading new software, research it online to check for reports of bundled unwanted applications.
- Verify Digital Signatures: When possible, verify that software installers have valid digital signatures from trusted publishers.
By implementing these preventive measures, you can significantly reduce the risk of InstallCore and similar potentially unwanted applications affecting your system. Remember that prevention is always more efficient and less disruptive than removal after infection.
Frequently Asked Questions
Is PUADlmanager:Win32/InstallCore dangerous?
PUADlmanager:Win32/InstallCore is not classified as malware in the strictest sense, but it does pose significant risks to your system. While it doesn’t directly damage your computer like ransomware or trojans, it degrades system performance by installing numerous unwanted applications that consume resources. These bundled programs often include adware that bombards you with intrusive advertisements, browser modifications that can compromise your privacy, and potentially more serious security threats. The cumulative effect of these unwanted applications creates a poor user experience and may expose your system to additional security vulnerabilities.
Should I ignore a PUADlmanager:Win32/InstallCore detection?
It’s generally not recommended to ignore a PUADlmanager:Win32/InstallCore detection, even if you believe it might be a false positive. While legitimate software may occasionally trigger this alert, the vast majority of InstallCore detections indicate the presence of software that employs questionable bundling practices. If you’re certain the flagged application is legitimate and obtained from a trusted source, you might consider adding a specific exclusion for that file in your security software. However, in most cases, you should treat the detection seriously and take appropriate removal steps to prevent unwanted software from being installed on your system.
How can I tell if InstallCore has affected my computer?
Signs that InstallCore has affected your computer include unexpected system slowdowns, new programs appearing that you didn’t intentionally install, browser homepage or search engine changes, increased pop-up advertisements both in browsers and as system notifications, new browser extensions or toolbars you don’t recognize, and difficulty removing certain applications. You might also notice unusual network activity, with your computer connecting to servers even when you’re not actively browsing. These symptoms often appear after installing free software, particularly if you rushed through the installation process without carefully reviewing each screen.
Why does legitimate software sometimes include InstallCore?
Legitimate software sometimes includes InstallCore as part of its distribution model for financial reasons. Software developers, particularly those offering free applications, often partner with bundling platforms like InstallCore to generate revenue. These partnerships operate on a pay-per-install basis, where developers earn a commission for each successful installation of bundled third-party applications. This monetization strategy allows developers to offer their primary software at no cost while still generating income. Unfortunately, this practice often comes at the expense of user experience and system performance, which is why security software flags these bundling technologies as potentially unwanted.
Can Windows Defender remove InstallCore completely?
Windows Defender can detect and remove the core components of PUADlmanager:Win32/InstallCore, but it may not completely eliminate all associated software and modifications. While Defender’s PUA protection (when enabled) can block initial installation attempts, dealing with existing InstallCore infections often requires more comprehensive removal. This is because InstallCore typically installs multiple additional applications, each with its own persistence mechanisms and system modifications. For complete removal, you may need to use specialized anti-malware software like GridinSoft Anti-Malware, which is designed to identify and eliminate all components of potentially unwanted applications and their bundled software.