Information is one of our most valuable assets in today’s digital world, making it a prime target for cybercriminals. These threat actors use specialized infostealer malware to extract sensitive data stored on your devices, putting your personal and financial information at serious risk. Cybersecurity experts have reported an alarming 103% increase in infostealer attacks during 2023-2024, with this upward trend showing no signs of slowing down. This comprehensive guide explains what infostealers are, how they work, and most importantly, how to protect yourself from these dangerous threats.
- What is an Infostealer?
- Major Infostealer Families: Technical Analysis
- How Infostealers Spread: Common Infection Vectors
- Technical Methods Used by Infostealers to Extract Data
- How to Protect Your System from Infostealers
- How to Detect and Remove Infostealers
- Frequently Asked Questions About Infostealers
- Conclusion
What is an Infostealer?
An infostealer is malicious software specifically designed to collect sensitive information from an infected device and transmit it to attackers. These sophisticated programs target high-value data including:
- Saved browser credentials (usernames and passwords)
- Banking information and credit card details
- Cryptocurrency wallet data and private keys
- Browser cookies and session data
- Email account credentials
- Personal documents and identity information
- Cached form data containing personal information
- System information and installed software details
The attack cycle typically follows a standard pattern: after infection, the infostealer silently collects data and stores it in a designated directory. Once collection is complete, it packages this information and sends it to command-and-control (C2) servers operated by threat actors. The most valuable targets for attackers are financial credentials, cryptocurrency wallet information, and authentication data that can be either monetized directly or sold on dark web markets.
Source: Darknet market research data, compiled February 2023
Since 2020, infostealers have experienced unprecedented growth in both sophistication and popularity among cybercriminals. This surge has established three clear market leaders: Raccoon, Vidar, and RedLine Stealer. These threats are continually evolving, with security researchers recently documenting their use in compromising over 100,000 ChatGPT accounts and targeting other high-value platforms.
Major Infostealer Families: Technical Analysis
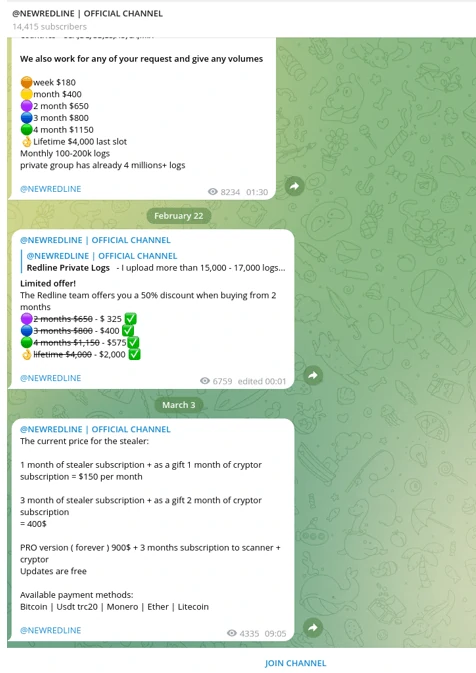
RedLine Stealer
RedLine emerged on Russian cybercrime forums in March 2020 and quickly became the most profitable credential-stealing malware in the logs marketplace. This sophisticated infostealer is specifically engineered to extract sensitive information from web browsers, including:
- Saved login credentials across all major browsers
- Autocomplete form data containing personal information
- Stored credit card information and payment details
- Cryptocurrency wallet credentials and access information
Upon infection, RedLine conducts a comprehensive system inventory, collecting usernames, geographic location data, hardware configurations, and installed security software. This information helps attackers profile victims and evade detection. Distribution occurs through multiple vectors, including malicious advertisements, cracked software, phishing campaigns, and compromised application downloads.
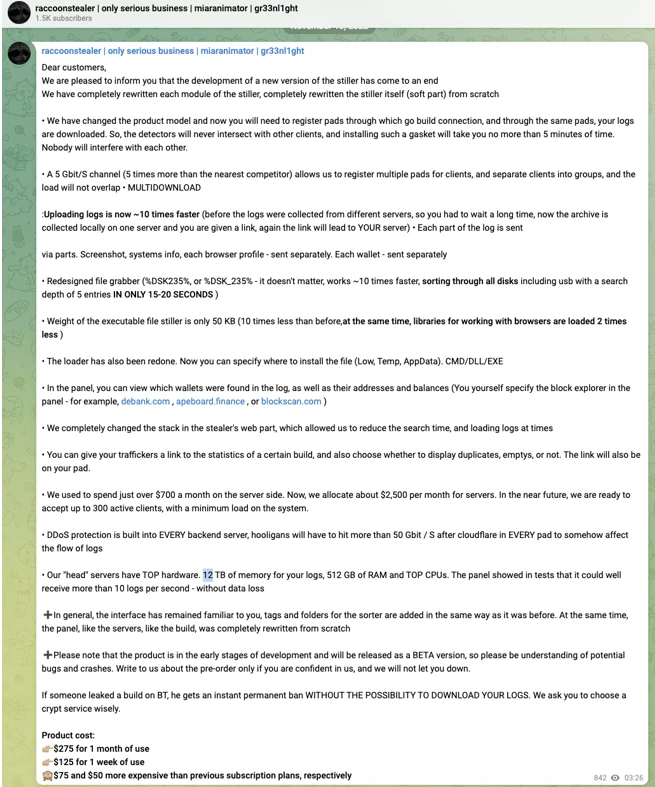
Raccoon Stealer
First appearing in 2019, Raccoon Stealer pioneered the malware-as-a-service (MaaS) model for infostealers, initially marketed on underground forums before transitioning to Telegram distribution channels. The malware received a significant update in 2022 that enhanced its detection evasion capabilities and expanded its functionality.
What makes Raccoon particularly dangerous is its ability to steal data from:
- More than 60 different web browsers
- Cryptocurrency browser extensions
- Cryptocurrency desktop wallets
- Authentication cookies enabling session hijacking
- Discord tokens and Telegram session data
Interestingly, Raccoon has a controversial reputation within hacker communities, with many users claiming its operators intercept the most valuable stolen logs before providing them to customers. Despite these allegations, Raccoon remains one of the most widely used infostealers, with its data appearing in numerous credential harvesting operations and follow-up attacks.
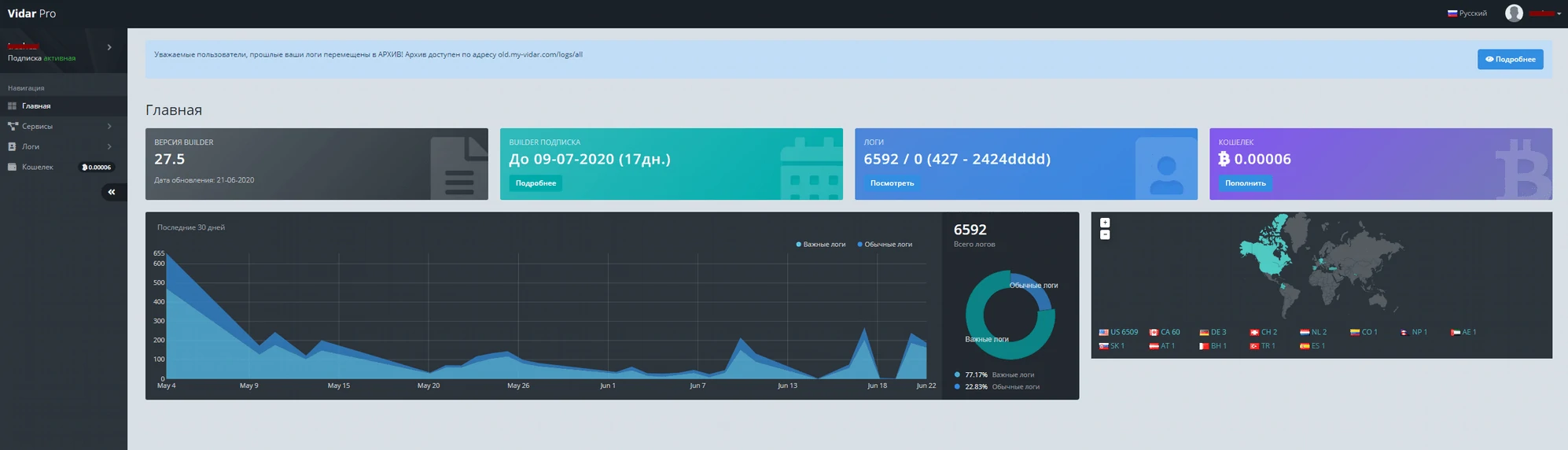
Vidar Stealer
Vidar represents the “hit-and-run” category of infostealers, designed for maximum data extraction with minimal footprint. First detected in 2019 during a malvertising campaign, Vidar was distributed alongside GandCrab ransomware using the Fallout exploit kit.
Built using C++ and derived from the earlier Arkei stealer, Vidar is commercially available on underground forums and Telegram channels. Its distinguishing feature is a comprehensive admin panel that allows customers to configure targeting parameters and monitor their botnet of infected systems.
Vidar’s data harvesting capabilities include:
- Browser artifacts (history, cookies, saved passwords)
- Cryptocurrency wallet files and credentials
- PayPal and banking service information
- Two-factor authentication backup codes
- Session tokens for various online services
- Screenshots of the victim’s desktop and active windows
After completing data collection, Vidar executes a “meltdown” procedure, effectively removing itself from the infected system to avoid detection and forensic analysis. This self-deletion capability makes Vidar particularly challenging to detect and analyze after an attack has occurred.
How Infostealers Spread: Common Infection Vectors
Cybercriminals employ various sophisticated distribution methods to deploy infostealers on target systems. Understanding these attack vectors is crucial for effective prevention:
-
Pirated Software and Cracked Applications
Threat actors frequently bundle infostealers with pirated software downloads. These modified applications appear to function normally while silently installing malware in the background. The increased sophistication of modern infostealers makes them particularly difficult to detect in compromised software packages.
-
Malvertising Campaigns
Exploit kits deployed through malicious online advertisements remain one of the most prevalent distribution methods. When users click on these ads, they may unknowingly trigger an infostealer download, or be redirected to phishing sites that deploy the malware. In advanced attacks, even simply viewing the advertisement can initiate a drive-by download through browser exploits.
-
System Compromises and Supply Chain Attacks
Once attackers gain initial access to a system through other means, they often deploy infostealers as secondary payloads. This approach is particularly common in supply chain attacks where legitimate software update mechanisms are compromised to distribute malware to thousands of systems simultaneously.
-
Phishing and Social Engineering
Sophisticated phishing campaigns remain highly effective at delivering infostealers. Attackers impersonate legitimate organizations in emails containing malicious attachments or links to compromised websites. These communications may be sent to large groups (mass phishing) or carefully tailored for specific individuals or organizations (spear phishing).
Technical Methods Used by Infostealers to Extract Data
Modern infostealers employ several sophisticated techniques to extract sensitive information from infected systems:
-
Browser Database Extraction
Infostealers specifically target browser data storage files such as
Login Data,Web Data, andCookiesin Chrome-based browsers, orlogins.jsonandcookies.sqlitein Firefox. These files contain encrypted credentials that the malware decrypts using built-in browser functions or by extracting encryption keys from the system. -
Memory Scraping
Advanced infostealers scan process memory for patterns matching passwords, credit card numbers, and other sensitive data. This technique captures information that might only exist temporarily in memory during browser sessions, bypassing disk encryption and other security measures.
-
Form Grabbing and Web Injection
By hooking into browser processes, infostealers can intercept data as it’s being entered into web forms before encryption or transmission. This approach captures credentials even when they aren’t stored locally, making it effective against security-conscious users who disable password saving features.
-
API Hooking and DLL Hijacking
Infostealers often modify system functions through API hooking or DLL hijacking to intercept cryptographic operations, redirect network traffic, or capture authentication data as it’s processed by the operating system.
How to Protect Your System from Infostealers
Implementing these essential security practices will significantly reduce your risk of infostealer infections:
-
Keep Software Updated
Infostealers frequently exploit known browser vulnerabilities and security flaws in operating systems. Install updates for your OS, browsers, and applications immediately when available to patch these vulnerabilities before they can be exploited.
-
Practice Safe Browsing Habits
Exercise caution when opening email attachments or clicking links, especially from unknown sources. Infostealers commonly spread through malicious email attachments and compromised websites. Be particularly suspicious of emails that don’t address you by name or contain generic urgency messages. Always verify URLs before clicking and ensure you’re visiting legitimate websites.
-
Implement Multi-Factor Authentication
Multi-factor authentication (MFA) provides critical protection against credential theft. Even if an infostealer successfully captures your passwords, MFA requires an additional verification method, significantly reducing the risk of account compromise. Whenever possible, use hardware security keys or authenticator apps rather than SMS-based verification.
-
Avoid Pirated Software
Pirated software frequently contains malware, providing a revenue stream for the cracking groups distributing them. Use only legitimate applications from official sources. Today’s software ecosystem offers numerous free, freemium, and open-source alternatives for most applications, eliminating the need to risk using pirated software.
-
Use Dedicated Security Software
Deploy comprehensive anti-malware protection that includes real-time monitoring and behavioral detection capabilities. GridinSoft Anti-Malware provides specialized detection for infostealers and other advanced threats, offering protection against even the newest variants through its heuristic analysis engine.
How to Detect and Remove Infostealers
If you suspect your system may be infected with an infostealer, look for these warning signs:
- Unexpected browser performance issues or crashes
- Modified browser settings or homepage changes
- Unusual network activity, particularly during idle periods
- Unexpected authentication prompts from websites you’ve previously logged into
- Unauthorized account activity or transaction notifications
- New, unfamiliar processes in Task Manager
Automatic Removal with GridinSoft Anti-Malware
For effective detection and removal of infostealers, we recommend using specialized anti-malware software. GridinSoft Anti-Malware is specifically designed to identify and eliminate sophisticated threats that traditional antivirus programs might miss.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Post-Infection Security Measures
After removing an infostealer, take these additional steps to secure your digital identity:
- Change all passwords from a different, clean device
- Enable multi-factor authentication on all important accounts
- Monitor financial statements for unauthorized transactions
- Check login activity logs for your important online accounts
- Consider credit monitoring services if financial information may have been compromised
Frequently Asked Questions About Infostealers
How do I know if my computer is infected with an infostealer?
Common signs of infostealer infection include unexpected browser behavior, modified settings, unusual network activity, repeated authentication requests from websites, unauthorized account activities, and new unknown processes in Task Manager. However, modern infostealers are designed to operate discreetly, so regular security scans are recommended even without obvious symptoms.
What types of information do infostealers typically target?
Infostealers primarily target high-value data including saved browser passwords, banking credentials, credit card details, cryptocurrency wallet information, authentication cookies, email account credentials, personal documents, and system information. The most valuable targets are financial credentials and cryptocurrency wallets that can be immediately monetized.
Can antivirus software detect and remove infostealers?
While traditional antivirus programs can detect known infostealer signatures, modern variants use advanced evasion techniques that may bypass conventional security. Specialized anti-malware software like GridinSoft Anti-Malware employs behavioral analysis and heuristic detection to identify even new or modified infostealer variants that signature-based detection might miss.
What should I do if my passwords were stolen by an infostealer?
If you suspect your passwords have been compromised by an infostealer, immediately change all passwords using a different, clean device. Prioritize financial accounts, email, and other high-value services. Enable multi-factor authentication wherever possible, monitor account activity for unauthorized access, and consider using a password manager with strong encryption for future password management.
How do infostealers extract passwords from browsers?
Infostealers extract browser passwords through several methods: accessing browser database files where credentials are stored (like Chrome’s Login Data or Firefox’s logins.json), utilizing the browser’s built-in decryption functions to decrypt saved passwords, implementing memory scraping to capture credentials as they’re being processed, and using form grabbing techniques to intercept data before it’s encrypted and sent.
Conclusion
Infostealers represent one of the most significant threats to personal and financial security in today’s digital landscape. Their sophisticated data extraction capabilities and continuous evolution make them challenging adversaries. By understanding how these threats operate and implementing the recommended security practices, you can significantly reduce your risk of infection and data compromise.
Remember that security is an ongoing process, not a one-time implementation. Regular software updates, cautious online behavior, and periodic security scans are essential components of an effective defense strategy against infostealers and other digital threats.





