Ever spotted “AggregatorHost.exe” lurking in your Task Manager and wondered what the heck it is? You’re not alone. This sneaky little process pops in and out of your Task Manager like that friend who only shows up when they need something. Let’s demystify what it’s really doing in your system.
What is AggregatorHost.exe Actually Doing on Your PC?
In short, AggregatorHost.exe is Microsoft’s digital spy – but the legal kind. It’s their telemetry aggregator that collects data about how you use Windows and sends it back to Microsoft HQ. Originally created for the Windows Insider Program, it helps the folks in Redmond test features before they unleash them on the general public.
The process is controlled by something called “Connected User Experience and Telemetry” in your services. If you ever joined Windows Insider or downloaded insider content, you probably clicked “I agree” to a terms of service that gave Microsoft permission to collect this data. Surprise – this is how they do it!
Beyond just snooping on your usage habits, AggregatorHost also handles some UI elements. It’s responsible for those fancy live tiles in your Start menu and drawing thumbnails when you hover over taskbar apps. Not just a spy, but a part-time artist too.
Should You Be Worried About It?
The real AggregatorHost is completely harmless – it’s just Microsoft keeping tabs on you with your permission. The problem? Malware creators aren’t very original and love to disguise their nasty programs using the names of legitimate Windows processes. It’s the digital equivalent of wearing a name tag that says “definitely not a criminal.”
If you’re suspicious about your AggregatorHost, there’s an easy way to check if it’s legit. A genuine AggregatorHost always lives in C:\Windows\System32 and nowhere else. If yours is hanging out somewhere different, that’s a major red flag.
How to Tell If Your AggregatorHost Is the Real Deal
Verifying AggregatorHost is like checking ID at a club – it’s all about the credentials. Right-click on AggregatorHost.exe in Task Manager and select “Open file location.” If it takes you anywhere other than System32, you’ve got an imposter.
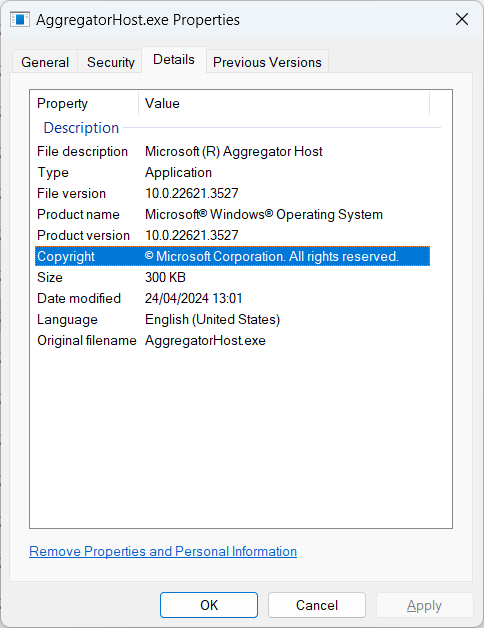
Want to get fancy with your verification? Check the digital signature by right-clicking the file, selecting Properties, then the Details tab. It should be signed by Microsoft Corporation – not “Totally Legit Software Inc.” or any other sketchy alternative.
For the tech-savvy crowd, you can run this PowerShell command to verify the signature:
Get-AuthenticodeSignature -FilePath C:\Windows\System32\AggregatorHost.exe | Format-List
The results should show Microsoft Windows Production as the issuer and have a Valid status. Anything else means you should probably be concerned.
An interesting tidbit that Microsoft doesn’t advertise: AggregatorHost.exe contains debugging information that reveals its source code paths. Lines like “onecore\base\telemetry\utc\aggregation\aggregatorhost\exe\main.cpp” can be found if you dig deep enough. So yes, it’s primarily about telemetry.
Resource Hog or Well-Behaved Process?
A legitimate AggregatorHost is like a good houseguest – it shouldn’t eat all your food or make a mess. In Task Manager, it should use minimal CPU and memory resources. If yours is chugging resources like a college student at an open bar, something’s wrong.
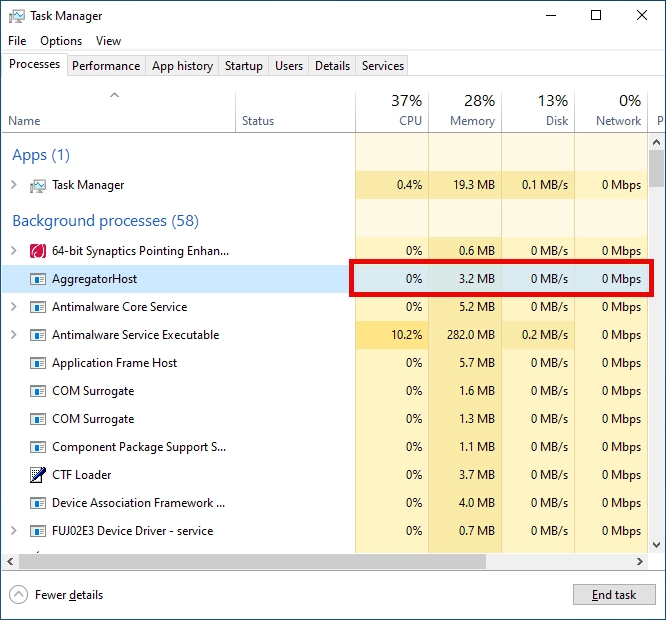
High CPU or GPU usage from AggregatorHost is particularly suspicious. Cryptominers love to disguise themselves as system processes while stealing your computing power to mine Bitcoin. It’s like someone breaking into your car just to drive for Uber.
Can You Just Delete It and Be Done?
Thinking about showing AggregatorHost the door? Not so fast. Since it’s a legitimate Windows component, removing it is like taking a bolt out of your car’s engine – technically possible, but not a great idea.
If it’s causing issues, try updating Windows first – Microsoft may have already fixed the problem. Your second option is running System File Checker by opening Command Prompt as administrator and typing sfc /scannow. This built-in tool will replace corrupted system files with fresh copies.
If you’re really concerned about privacy, you can limit telemetry in Windows settings instead of trying to remove the process. It’s like putting a blindfold on the spy rather than attempting to kick them out entirely.
How to Stop AggregatorHost from Spying on You
Not comfortable with Microsoft’s digital spies collecting your data? You can actually disable the telemetry services without breaking your system. Think of it as giving your nosy neighbor the silent treatment – they’re still there, but they can’t report back about your activities.
The most effective way to reign in AggregatorHost is to disable the task that feeds it data. Here’s how to muzzle this chatty process:
- Click Start, type “Task Scheduler” in the search box, and press Enter (no special secret handshake required).
- In the Task Scheduler window, navigate to this path: Task Scheduler Library → Microsoft → Windows → Application Experience.
- Find the task called “Microsoft Compatibility Appraiser” – that’s the main data collector feeding AggregatorHost.
- Right-click on it, select “Disable,” and confirm the action. Congratulations, you’ve just put a gag on Microsoft’s telemetry reporter!
After disabling this task, you should notice AggregatorHost appearing less frequently in your Task Manager. The process itself will still exist in your system, but it won’t be actively collecting and sending data. It’s like having a spy who forgot to file their reports.
Keep in mind that Microsoft claims telemetry helps improve Windows by identifying bugs and issues. But hey, it’s your computer – you get to decide how much you want to share with the mothership in Redmond.
When All Else Fails: Scan for Imposters
Still suspicious that your AggregatorHost isn’t what it claims to be? A thorough malware scan is your best bet. Malware disguised as system processes is a common trick – it’s the digital equivalent of hiding in plain sight.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Remember, even the most cautious of us can end up with unwanted passengers on our systems. There’s no shame in doing a periodic scan just to be sure everything is as legitimate as it claims to be.
The Bottom Line
AggregatorHost.exe is just Microsoft’s way of collecting telemetry data that you probably agreed to share at some point. It’s not harmful on its own, but it’s a favorite disguise for malware. Knowing how to verify the real thing from imposters is an essential skill for any Windows user.
And hey, now you can impress your friends with random Windows process knowledge at parties. Though I can’t guarantee that will make you more popular – some mysteries are beyond even tech bloggers’ abilities to solve.