In recent years ransomware1 has become a constant threat to numerous enterprises and individuals. Some ransomware variants even developed into the whole business model — RaaS. This particular malware grows largely thanks to the whole business steadily moving online and a large portion of employees working remotely. In this article, we will look at what Maze ransomware is, how it works, and how to deal with it.
The new variants of malware2 are being developed and some of those already existing are getting regular updates. The ransomware operators constantly make the news by targeting enterprises, even threatening the national security of countries.
What is Maze Ransomware?
A sophisticated strain of Windows ransomware that was initially developed as a variant of ChaCha ransomware. First-time cyber security specialists discovered it in May 2019. The malware targets organizations worldwide across numerous industries.
NOTE: Ransomware – one of the most dangerous types of malware. Knowing how to protect your system from attack is important no matter who you are.
The same as with other forms of ransomware it demands money for the restoration of encrypted data. If the victim of an attack refuses to pay they threaten to leak the beforehand stolen data. The general behavior of the malware is similar to JSWorm/Nemty/Nefilim, Clop, REvil/Sodinokibi, and others.
Maze Ransomware Algorithms
The first time the Maze cybercriminals conducted an attack was in May 2019. Initially, criminals distributed it via exploit kits and spam email but now they have developed new and more stealthy procedures, techniques, and tactics. Sometimes they even hire other threat actors to research their new victims.
The malicious emails Maze ransomware actors sent with the “Your AT& T wireless bill is ready to view” and “Missed package delivery” titles in the subject line.
Once threat actors find a security gap in the network they try to obtain an elevated privilege, then conduct lateral movement to finally deploy file encryption across all drives; all this before carefully stealing data.
How Does Maze Ransomware Work?
For encryption, Maze ransomware uses RSA and ChaCha20 algorithms. After the encryption is done the malware changes the desktop image to the ransom note.
With the notice displayed the victim now has the option to decide whether to pay the ransom or not. Usually, the Maze cybercriminals will ask for $500 in Bitcoins to pay via a specified BTC wallet address. The ransom gets doubled unless the payment is not made in time.
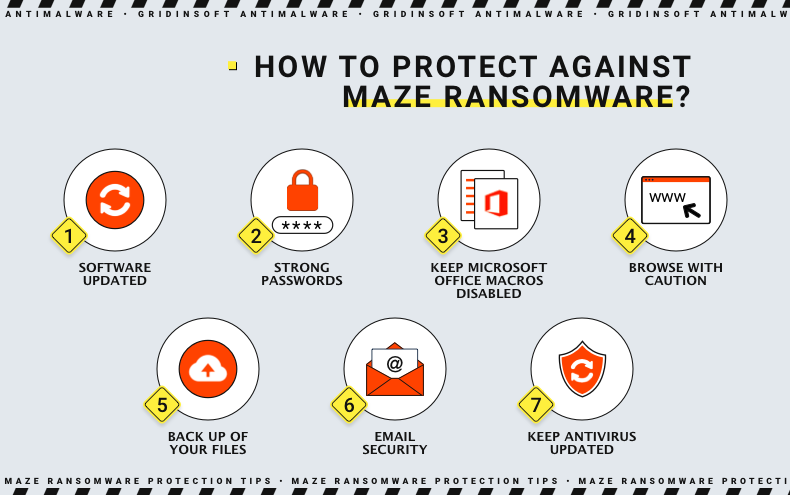
How to Protect Against Maze Ransomware
Alas, there’s no decryption tool available for the Maze ransomware strain so the only solution will be following some security measures to at least prevent the likelihood of getting infected with this malware:
- Keep your software and OS regularly updated. It’s a common security rule not only against ransomware but also against any cybersecurity threat present out there in the world. Cybercriminals will have less chance to succeed if there are fewer vulnerabilities to exploit.
- Set the management of your accounts. Here comes setting complex passwords, changing them frequently, and enabling multi-factor authentication mechanisms. Generally, you should avoid browsing or opening documents if you are logged in as an administrator.
- Keep Microsoft Office macros disabled. These little programs that do useful tasks should not be enabled once you open the Excel or Word document. Remember that Maze ransomware particularly exploited the thing making it its modus operandi back in a day.
- Browse with caution. Try to develop a secure browsing habit. Regularly update your browser, don’t install suspicious extensions, and set a setting to block any pop-up ads. Check if the website you’re visiting is secure by looking at its address bar in a browser. It should be HTTPS to guarantee you the safety and security of your doings on the website. On the contrary, the connection with just HTTP doesn’t offer enough of that.
- Make the backup of your files. It can be an online or offline backup but it definitely should be in place. Using it you protect your valuable data not only from some ransomware attacks but also other cyber attacks of different kinds. In addition, don’t forget to protect the backup itself with strong, complex passwords.
- Don’t forget about email security. Never open attachments or go after links that came from unknown, unexpected, or unwanted sources. Enable multi-factor authentication and set the passwords’ expiration date. Just be extra cautious with all the correspondence you receive.
- Keep your antivirus solution regularly updated. In case the infection is there in your system your antivirus solution will be able to effectively detect it and remove it.
Examples of Maze Ransomware Attacks
In a ransom note, a victim also receives detailed instructions on how to make payment. In addition, cybercriminals offer proof of their having the decryption keys/tools; victims can send them for the free decryption of up to three files to get the proof. The most famous victims on the Maze ransomware list are:
The LG Electronics Attack
In the case of this company, the gang didn’t execute the encryption on the compromised network but instead, they chose to only steal the sensitive data. The reason for such a peculiar move was explained by the gang themselves to the ZDNet reporters when the journalists contacted them on their leak site.
INTERESTIONG FACT: Some examples of ransomware may threaten victims to delete their files or publish some of their sensitive data unless they pay a ransom.
“We decided not to execute Maze ransomware because their clients are socially significant and we do not want to disrupt their operations, so we only have exfiltrated the data,” the gang responded to the reporters. In the attack, hackers stole 50.2 GB from LG’s internal network and published it online.
The Cognizant Attack
Cognizant, one of the largest IT services providers and companies from the Fortune 500 firm list suffered the Maze attack in April 2020. The attack resulted in widespread service outages.
Both the internal and external work of the company got paralyzed when the employees and sales teams lost communications. Due to the attack, the IT provider suffered significant financial losses. It was estimated that losses made up from $50 to $70 million in lost revenue.
The Xerox Attack
In July 2021 the giant printing company also suffered an attack from the Maze ransomware. The gang stole more than 100 GB from Xerox. Among the stolen data were various databases and financial documents and as specialists noted it seems that the encryption process started on June 24.
The Allied Universal Attack
In November 2019 a security staffing firm suffered an attack from Maze ransomware as well. The gang leaked about 700 MB of data after the company surpassed the deadline for a ransom payment. As usual in such cases, the criminals warned that they leaked only ten percent of what was stolen.
Other Similar Ransomware Attacks
You can say it’s true that ransomware has become number one in the Evil Corporation these days because the next malware variants have also made the name by hitting the big fish:
Locker Ransomware
Recently the FBI issued an alert that the gang has infected at least 52 critical infrastructure organizations across America. The systems that have been attacked include those in information technology sectors, government, financial services, energy, and critical manufacturing.
Avaddon Ransomware
The infamous avaddon ransomware gang used not double but triple extortion techniques threatening its victims with DDoS attacks until the ransom is paid. The group doesn’t operate anymore, at least not under this name after the attack on Australian-based telecom provider Schepisi Communication.
VoidCrypt Ransomware
VoidCrypt ransomware is hard to get rid of unless there’s direct involvement of the criminals behind it. It means you can restore your encrypted files without them but unfortunately, there’s less chance you will restore them with the criminal’s help you only suffer financial and data loss.
IMPORTANT: The Help virus belongs to the VoidCrypt ransomware family and encrypts all data on your PC. A scientifically accurate name for the help would be “VoidCrypt family ransomware-type infection”.
Snatch Ransomware
Let’s talk Snatch ransomware attack. In one organization’s network, the gang managed to infect 200 machines or roughly 5% of the company’s computers. Another target on the gang’s list was Volvo Cars. Even though the Snatch team took responsibility for the attack the company had not confirmed their involvement. In addition, the group has also harassed for a long time the employees of the Canadian airport posting little by little the stolen info.
Conclusion
But how fierce the ransomware can be, you can also find a good antivirus software product that can help you with protection and security. Try Gridinsoft Anti-Malware to stand against any future cyber threats. It offers an easy-to-navigate interface and efficient work.





