Pretexting is a type of social engineering in which an attacker gains access to information, a system, or a service by deception. In doing so, the attacker provides a false script or pretext to gain the victim’s trust. For example, he may pose as an experienced investor, human resources representative, IT specialist, or another seemingly legitimate source. This attack is not limited to online – it can take place through other forms of communication, including in person.
How does pretexting work?
During pretexting attacks, attackers may ask victims for specific information, claiming it is needed to confirm the victim’s identity. In reality, the attacker steals this information to use later for secondary attacks or identity theft. In addition, some attacks are so sophisticated that they can trick victims into performing an action that exploits an organization’s physical or digital weaknesses. For example, a fraudster might pose as an outside IT services auditor and convince the organization’s physical security team to allow the attacker into the building.
Many attackers using this type of attack, disguise themselves as employees of the organization or human resources in the finance department. This allows them to target senior executives or other employees with extensive privileges, as they are the ones who are of great value to the attackers. While phishing attacks use urgency and fear to exploit victims, pretexting attacks create a false sense of trust in the target victim. To do this, attackers must develop a credible legend that will not make victims suspicious.
Pretexting methods
Scammers do not stand still and use various methods to gain their victims’ trust and convince them to pass on valuable information. So, let’s break down these methods in more detail:
Impersonation
The scammer presents himself as a confidant, such as a colleague or a friend. This involves maintaining trust by spoofing prominent institutions’ or individuals’ phone numbers or email addresses. A classic example of impersonation is the SIM card spoofing scam, which exploits vulnerabilities in two-step verification processes, including SMS or phone verification, to capture target accounts. For example, the scammer may introduce himself as the victim and claim to have lost his phone, convincing the service provider to switch the phone number to a new SIM card. This way, all the one-time passwords are sent to the attacker and not the victim.
One successful social engineering attack using impersonation was on Ubiquiti Networks in 2015. At the time, employees received messages from scammers posing as the company’s top executives and demanding that funds be transferred to the attackers’ bank accounts. Such an oversight cost the company $46.7 million.
Baiting
As you can understand from the name, it is an attempt to trap the victim through the bait. The goal of this attack is to spread malware or steal sensitive information. Fraudsters may use malware-infected thumb drives as bait, often adding something to make them look authentic, such as a company label. Such decoys are placed in high-traffic locations, such as lobbies or bus stops, so victims will notice them and be incentivized to insert them into work or personal devices. Malware is then deployed to the device. Baiting can also be online. It can usually include enticing advertisements that lead victims to a malicious website or encourage them to download a malware-infected app.
Phishing
Phishing is impersonating a trusted person in messages (e-mails or text messages) to obtain confidential information. This can be payment card details and passwords. Phishing is different from pretexting, but Fraudsters can combine the two. Pretexting dramatically increases the chances of a phishing attempt succeeding. For example, when talking to a phishing scammer, targeted employees can be sure they are talking to an employer or contractor. Fraudsters can also use compromised employee accounts for further pretexting attacks targeting individuals with targeted phishing.
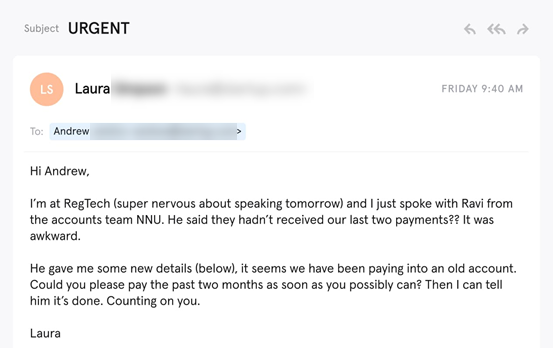
Thus McEwan University in Canada fell victim to a phishing attack in 2017 that cost the university about $9 million. At the time, targeted employees changed payment details, believing that the scammer was a contractor.
Vishing and Smishing
Vishing (voice phishing) is a social engineering technique that uses phone calls to trick victims into stealing confidential information or to give attackers remote access to the victim’s computer. This scheme often involves an attacker who calls victims pretending to be an IRS employee, who often threatens or tries to intimidate the victim into providing monetary compensation or personal information. Although such schemes usually target the elderly, anyone can still be duped by a vishing scam.
Smishing (SMS phishing) is a form of social engineering, very similar to vishing and phishing, but uses SMS or text messages.
Scareware
Scareware annoys victims with bogus threats and false alarms. First, the victim is tricked into thinking their system is infected with malware. The scammers then offer the victim to install software that is positioned as applicable but is, in fact, another malware. For example, a typical malware attack might include banners popping up in the victim’s browser while surfing the Web, which looks legitimate. However, such banners may contain something like, “Your computer may be infected with malware spyware. This is followed by an offer to install a specific tool (usually infected with malware) or direct the victim to a malicious Web site. Scareware can also spread through spam messages containing false warnings or offers to buy useless services.
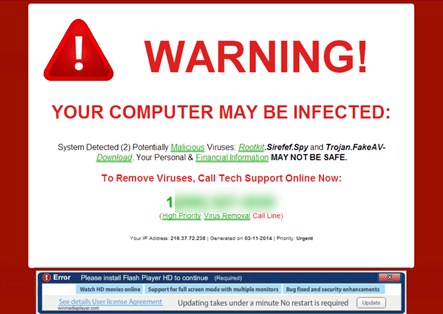
Pretexting and the Law
Pretexting is illegal in the United States. For financial institutions regulated by the Gramm-Leach-Bliley Act of 1999 (GLBA) (nearly all financial institutions), any attempt by an individual to obtain or cause an employee to disclose customer information through deception or false information is illegal. Also, GLBA-regulated institutions must enforce standards for training their employees to detect attempted pretexting. In 2006, Congress passed the Telephone Records and Privacy Protection Act of 2006, which extends protections to records kept by telecommunications companies. Unfortunately, in other industries, it needs to be clarified whether pretexting is illegal. In future court cases, prosecutors will have to decide which laws to use to bring charges since many were created without this scenario.
How to Prevent Pretexting
The most effective way to protect your organization from fraud is to avoid interacting with messages from suspicious and unknown senders. Scammers aim to get people to click on links or download infected attachments at all costs. Therefore, any statement that asks you to do any of these things should be taken cautiously. Here are a few methods companies use to protect themselves from pretexting:
DMARC
Since pretexting involves impersonation, the email must look as authentic as possible to be successful. This requires email spoofing. Domain-based authentication, reporting, and message matching (DMARC) is the most common form of email spoofing protection. However, it requires constant and complex maintenance, which makes it very limited. Moreover, although DMARC stops accurate domain spoofing, it does not stop name spoofing or related domain spoofing, which are much more common in targeted phishing attacks. However, attackers use these more sophisticated techniques mainly because of the effectiveness of DMARC.
AI-based email analysis
Modern problems require modern solutions. To reduce risk, enterprises must strive for a more advanced detection method than DMARC. Next-generation anti-target phishing technology uses artificial intelligence (AI) to learn user behavior and detect signs of pretexting. It can also detect email addresses and traffic anomalies, such as display name spoofing and related domains. Natural Language Processing (NLP), part of AI, examines language and can decipher phrases and words common to phishing and pretexting.
Educate users
The most effective solution is to train your users to spot pretexting. To do this, you should share real pretexting examples with them. Unfortunately, often the success of targeted phishing and pretexting is that users have yet to learn what it looks like and do not notice anything unusual in the requests they receive. Therefore, you should educate your users about all sorts of different types of spoofing and teach them how to analyze their emails for signs of display name spoofing and related domains. In addition, you should establish rules for financial transactions, such as confirming requests in person or by phone.
Report a phishing email
Unfortunately, users cannot prevent phishing attempts. However, they can be vigilant and report phishing emails when they spot them, thus protecting themselves and their organizations. To be a good Internet citizen and do your part, report phishing at [email protected].




