A team of researchers from the University of Michigan, the University of Pennsylvania, and NASA have detailed a TTEthernet (Time-Triggered Ethernet) PCspoF attack that could disable the Orion spacecraft.
Experts say vulnerabilities in this network technology, which is widely used in the space and aviation industries, could have catastrophic consequences for critical systems, including the disruption of NASA missions.
Let me remind you that we also wrote that NASA has faced 6000 cyberattacks in the past four years, and also that Malware Hides in Images from the James Webb Telescope.
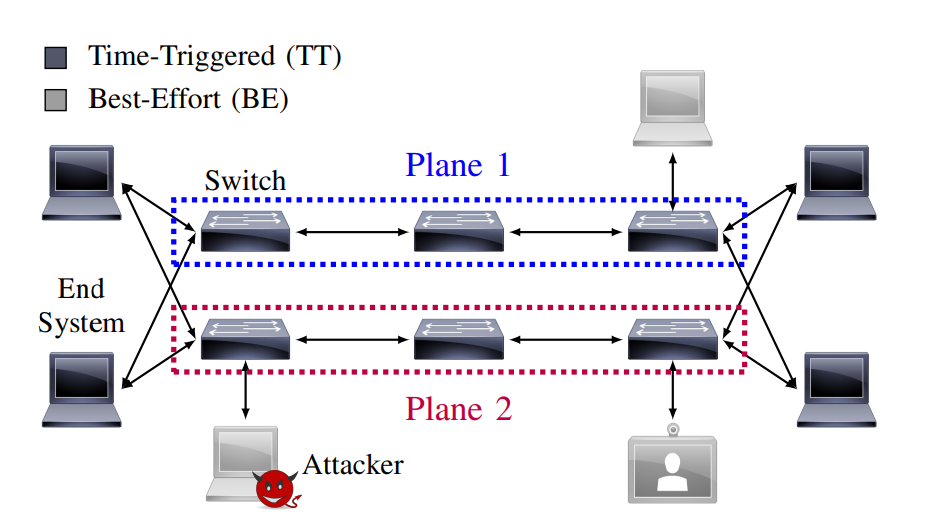
TTEthernet turns ordinary Ethernet into a deterministic network with certain transfer times between nodes and significantly expands the use of the classic Ethernet standard. In such a mixed-criticality network, traffic with different timing and fault tolerance requirements can coexist.
In fact, TTEthernet allows time-critical traffic (from devices that send highly synchronized, scheduled messages according to a predetermined schedule) to use the same switches that handle non-critical traffic, such as passenger Wi-Fi on airplanes.
In addition, TTEthernet is compatible with the standard Ethernet used in conventional systems. TTEthernet isolates time-triggered traffic from so-called best-effort traffic, i.e., non-critical systems, by forwarding their messages around more important time-triggered traffic.
This allows to combine different devices in one network, mission-critical systems can work on cheaper network equipment, and the two types of traffic do not overlap.
The creators of PCspooF say that TTEthernet is essentially the “backbone of the network” in spacecraft, including NASA’s Orion spacecraft, the Lunar Gateway space station, and the Ariane 6 launch vehicle. contender” to replace the Controller Area Network bus and the FlexRay protocol.
According to the researchers, the PCspooF attack is the first attack in history that broke the isolation of different types of traffic from each other. The essence of the problem lies in the fact that PCspooF violates the synchronization system, called the Protocol control frame (PCF), whose messages cause devices to work on schedule and ensure their fast communication.
So, the researchers found that non-critical best-effort devices can display private information about the time-triggered part of the network. In addition, these devices can be used to create malicious sync messages. A malicious, non-critical device can violate the isolation guarantee on the TTEthernet network.
The compromised best-effort device can then create EMI in the switch, forcing it to send fake synchronization messages to other TTEthernet devices.
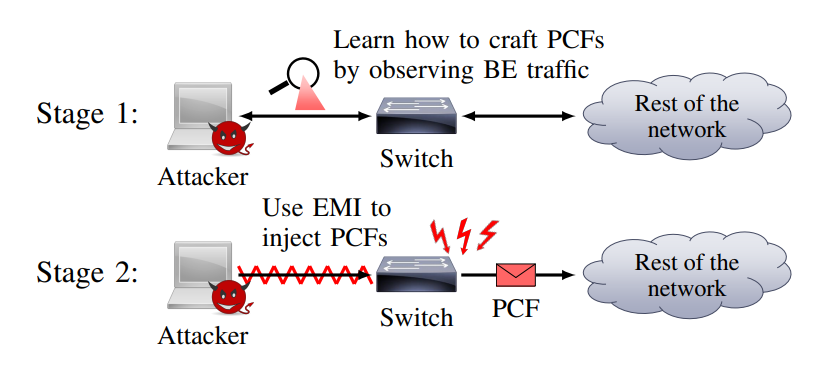
Once such an attack is launched, TTEthernet devices occasionally lose synchronization and reconnect. As a result, they lose synchronization (desynchronization can be up to a second), leading to the inability to send dozens of time-triggered messages and cause critical systems to fail. In the worst case, PCspooF provokes such failures simultaneously for all TTEthernet devices on the network, the researchers explain.
To test PCspooF, experts used NASA hardware and software components to simulate an asteroid redirection mission when Orion had to dock with an automated manned spacecraft. As a result, the PCspooF attack forced Orion to deviate from the course and completely fail the docking.
After successfully testing the attack, researchers reported the issue to organizations using TTEthernet, including NASA, the European Space Agency (ESA), Northrop Grumman Space Systems, and Airbus Defense and Space. Now, based on the data from the researchers, NASA is revising the protocols for onboard experiments and testing its off-the-shelf commercial equipment.
As protection against PCspooF and the consequences of such attacks, experts recommend using optical connectors or voltage stabilizers (to block electromagnetic interference); checking source MAC addresses to make sure they are authentic; hiding key PCF fields, using a link layer authentication protocol such as IEEE 802.1AE; increase the number of sync masters and disable dangerous state transitions.
Space technologies do not guarantee absolute protection: there are examples of authentic attacks. For example, the media wrote that DopplePaymer ransomware operators were hacked by NASA contractor.





