Securonix researchers have noticed an interesting malware campaign that distributes a malware called GO#WEBBFUSCATOR written in Go. Hackers use phishing emails, malicious documents, and images from the James Webb telescope to spread it.
Let me remind you that we also talked that MyKingz botnet uses Taylor Swift photo to infect target machines, and also that Hackers hide MageCart skimmers in social media buttons.
Typically, infection starts with a phishing email with a malicious document Geos-Rates.docx attached, which downloads a template file. This file, in turn, contains an obfuscated VBS macro that runs automatically if macros are enabled in Office.
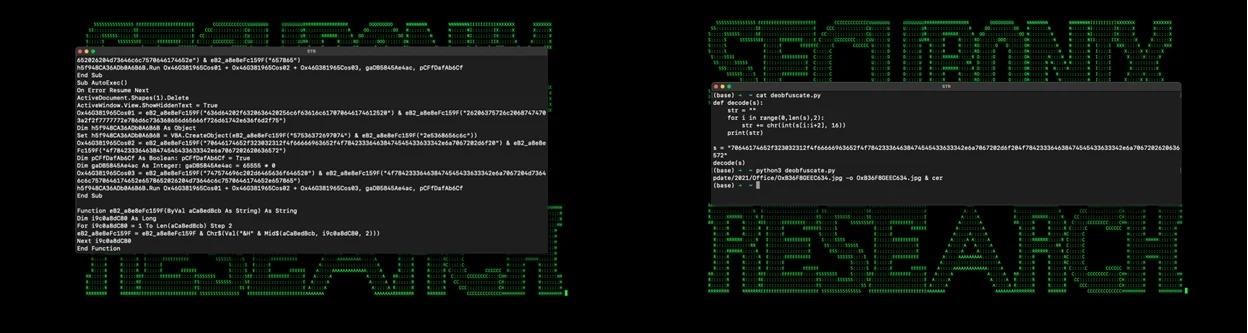
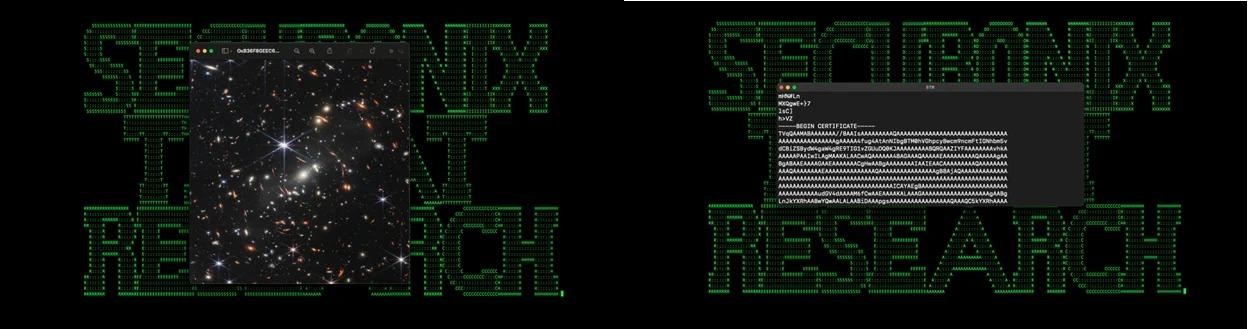
Then, an image in JPG format (OxB36F8GEEC634.jpg) is downloaded from a remote resource controlled by the attackers (xmlschemeformat[.]com). The picture is decoded into an executable file (msdllupdate.exe) using certutil.exe, after which the file is launched.
Interestingly, if you simply open this malicious .JPG, you can see the galaxy cluster SMACS 0723, taken by the James Webb Telescope and published by NASA in July 2022. If you open the file in a text editor, you can find additional content, namely the payload encrypted with Base64, which eventually turns into a malicious executable file.
Dynamic analysis of the malware showed that the executable file provides the malware with a stable presence in the system by copying itself to “%%localappdata%%\microsoft\vault\” and creating a new registry key. Once launched, the malware establishes a DNS connection with the command and control server and sends encrypted requests to it.
The command and control server can respond to malware by setting time intervals between connection requests, changing the nslookup timeout, or sending commands to be executed using cmd.exe. Thus, Securonix experts observed how the attackers ran arbitrary enumeration commands on test systems, that is, they carried out initial reconnaissance on infected machines.
The researchers note that the domains used in this campaign were registered recently, the oldest of which is dated May 29, 2022.

