Usually, hackers hack for monetary gain. However, there are less apparent reasons lurking beneath the surface. But knowledge of technology is not enough to be a successful hacker. You also need to know how to monetize your hacking skills without getting caught. It would help if you had a hacking motivation. But why would a talented person with extensive knowledge of information technology and financial channels take the risk of hacking? What are the reasons? We’re about to find out.
Why do hackers do what they do?
Financial benefits
This is perhaps the most obvious motivation for a hacker. Money has always been the main driver for different crimes, and cybercrimes are no exception. The 2020 Data Breach Investigation Report (DBIR) states that 86% of the data breaches analyzed were financially motivated. Hackers who profit financially by hacking others usually fall into the black hat hacker category. However, they can also make money legally. Therefore, they are called white hat hackers (ethical hackers). We will talk about them closer to the end of the article.
Misusing Data
Hackers can steal victims’ financial or personal information through various tactics, such as malware, phishing, and brute force attacks. They can then use this data to commit financial fraud by making fraudulent purchases or transferring money to their bank or cryptocurrency account.
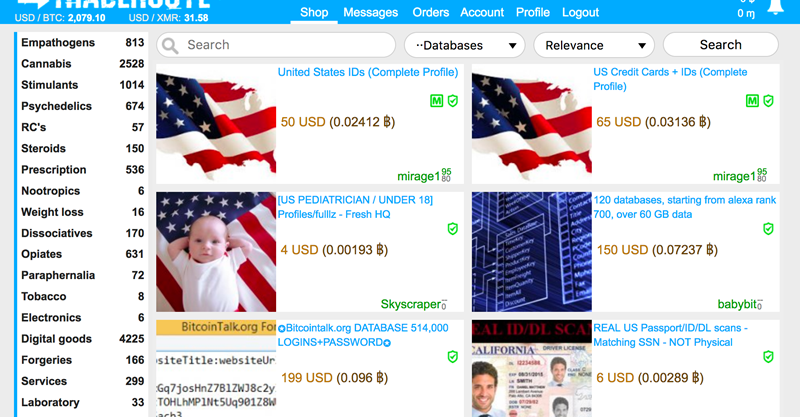
Selling Data on the Dark Web
Some hackers sell stolen data on the Darknet. Other shop floor co-workers buy this data to commit financial fraud and other PII-related crimes. Even unscrupulous online advertisers and marketers may be interested in such data. In addition, they may use it for their own dirty business, such as creating targeted ads or sending spam emails. Nothing good will come if your information is compromised due to this hacker’s motivation.
Blackmailing Victims
Blackmail is powerful leverage in the arsenal of any cybercriminal, including hackers. For example, they can steal sensitive data, intercept personal photos, videos, etc., and demand money not to publish information. They can also encrypt sensitive data or block users’ access to their devices and demand a ransom in exchange for access.
Hackers use particular malware, such as ransomware and spyware, to steal data and block hacked devices. Sometimes they compromise the databases of companies or government agencies to gain access to their data. Then, crooks demand money for not revealing trade secrets or publishing other sensitive information.
Hackers are Taking Personal Revenge
Some hackers use their skills to retaliate against a person or company for an actual or perceived injustice. They can annoy their enemies in various ways, such as locking the victim’s device and encrypting or deleting their data. Also, they can publish personal media files to the public (known as doxxing). Sometimes it comes down to hacking their social media profiles and posting false or inappropriate content.
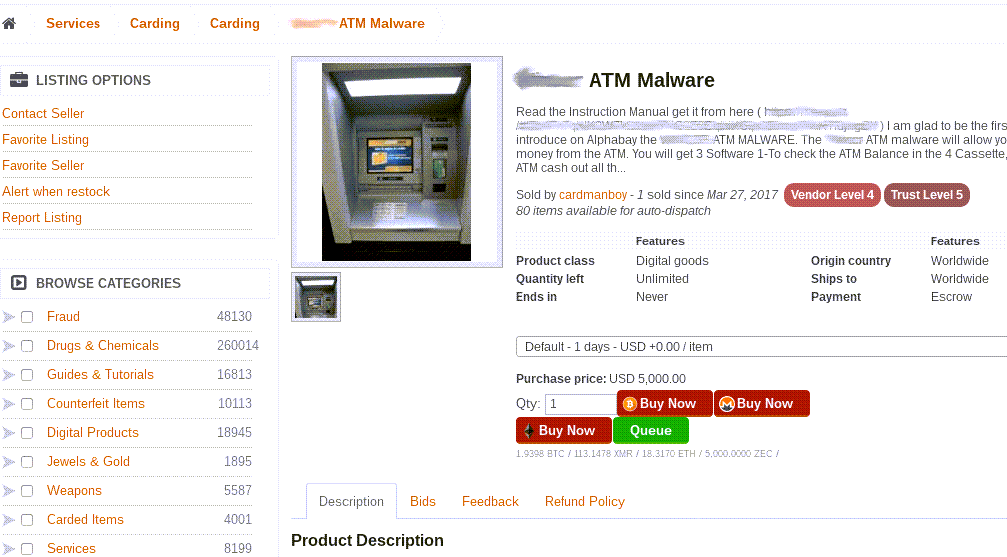
Selling Malware
Some hackers are just programmers who write code for different types of malware, including worms, trojans, viruses, malware, rootkits, etc. They might not even use the malware but sell it to other cybercriminals. Darknet is full of offers for a contract from such craftsmen, who are ready to create a unique malware that will not be detected by signatures for a reasonable price.
Using Psychological Manipulation
Sometimes cybercriminals can manipulate their victims into sending money to the wrong place by posing as someone trustworthy. In some cases, it takes the form of emotional manipulation – helping a friend or family member in an accident, an accident victim, or asking for a charitable donation. There are also situations when the methods are so sophisticated that they trick a victim into transferring corporate funds without proper authorization or make them pay for unnecessary services or fake products. These are just a tiny fraction of hackers’ methods to make money. As you can see, they include lying, manipulating, threatening, and blackmailing victims and other targets without regret.
Carrying Out Political Agendas
Some governments hire hackers for political espionage. In these cases, they become known as nation-state actors. They are assigned responsibilities such as:
- Theft of sensitive, confidential data (research, trade secrets, or even personal information about specific targets).
- Manipulation or other interference with an election.
- Theft or leakage of government or military documents.
- Interference in the economy.
- Influence on relations or treaties with other countries.
Such governments often publish compromised or hacked data to the public to cause distrust of authority or political unrest in an enemy country. In addition, hackers took cyberattacks, such as DDoS attacks, on government websites and servers in a rival county to cause functional or operational failures. Such attacks are also known as state-sponsored cyberattacks. Countries such as Russia, Iran, China, and North Korea are notorious for using such tactics.

Hackers in Corporate Espionage
Sometimes companies hire hackers to steal confidential information from competitor firms. In such cases, they are tasked with finding leaky or vulnerable databases or launching attacks on the target organization’s servers or Web sites. They can attack in several ways, including brute force, cross-site scripting, injecton of the malicious database requests, and DDoS attacks. Target data can be almost anything. Most often, however, it is trade secrets, key customers, suppliers, vendors, pricing information, insider information about future financial planning, technical schemes, or confidential product information. In addition, some companies hire hackers to slow down or disrupt a competitor’s Web site by deploying DDoS attacks. This attack severely overloads an organization’s Web servers, making them inaccessible to customers. They may also leak sensitive customer data to tarnish a competitor’s reputation.
Proving a Point (Hacktivist)
However, for not all hackers, profit is the primary goal. Instead, they hack to prove their social, ethical, religious, or political views or to impose their beliefs on others.
To demonstrate their protest and anger over the death of the late Iranian Major General Qassim Suleimani, Iranian hackers in January 2020 attacked the U.S. Federal Depository Library Program website to display an image of President Donald Trump on a map of the Middle East.
In July 2015, hacktivists called themselves “Impact Team” hacked the Ashley Madison online fraud website. As a result, the personal information of 32 million participants was released to the public. They did this to teach participants a lesson and force the owner to shut down the site.
Fame
Some hackers just like the sense of power and achievement they get from defacing hundreds of websites. They want to gain popularity and create fear around their names, so people take them seriously. For example, most people in the cybersecurity industry are familiar with terms such as Shiny Hunters, Chaos Computer Club (CCC), Lizard Squad, Lazarus Group, Anonymous, and Tarh Andishan.
Hackers Causing Harm for Personal Enjoyment
Some black hackers engage in breaking to create havoc or cause harm. Their actions have no purpose; they simply enjoy destroying a person’s or company’s reputation, disrupting government operations, or destroying essential data. They can be addicted to hacking and feel satisfied when they hack or cheat someone.
Mitigating Cyber Threats
Unlike all of the above, these guys work for the good of society, you could say. So yes, sometimes hackers do it not to hurt but to help or to prevent other hackers from doing bad things. These guys usually fall into the white or red hat category. White hat hackers crack into websites, servers, and databases to prevent black hats who want to harm. They use almost the same hacking techniques as black hat hackers. However, they do so with the system owner’s permission and by following legitimate methods. Typically, companies and government agencies hire them as information security analysts, cybersecurity researchers, security specialists, penetration testers, etc. In addition, they may work as independent consultants or as freelancers. The intentions of white hackers are usually as follows:
- Finding and fixing vulnerabilities in a system before black hat actors exploit them.
- Developing security software that detects and removes threats.
- Educating users about cyber threats and how to avoid them.
- Mapping out a contingency plan in the event of a cyber attack.
- Strengthening the overall security of software and hardware components.
But there is another type of hacker who likes to attack the bad guys: These are the red hat hackers. Red hats are similar to black ones because they usually do not follow legitimate methods in their attacks and hack without permission. However, they attack other hackers instead of targeting businesses and other legitimate users.
Other Motivations for Hackers
Of course, we have not yet mentioned other motives. Two of the most important are human curiosity and the desire to learn. Some of them are beginners and have no experience. They want to expand their knowledge and skills or “play with their muscles”. We now know that not all cybercriminals have evil motives. The security professionals who protect our data and systems are also called hackers. However, they are white hackers with good intentions.




