
SQL Injection (SQLi)
SQL is a structured query programming language (SQL, Structured Query Language) that is used as an efficient way to save data, find parts of it, update it, retrieve it from the database and delete it. It allows programmers to communicate with large databases in an almost simple English language. It also allows you to access and manipulate data stored in tables on the server. In the case of websites, the tables can store confidential data, such as logins, passwords, credit card numbers, etc.
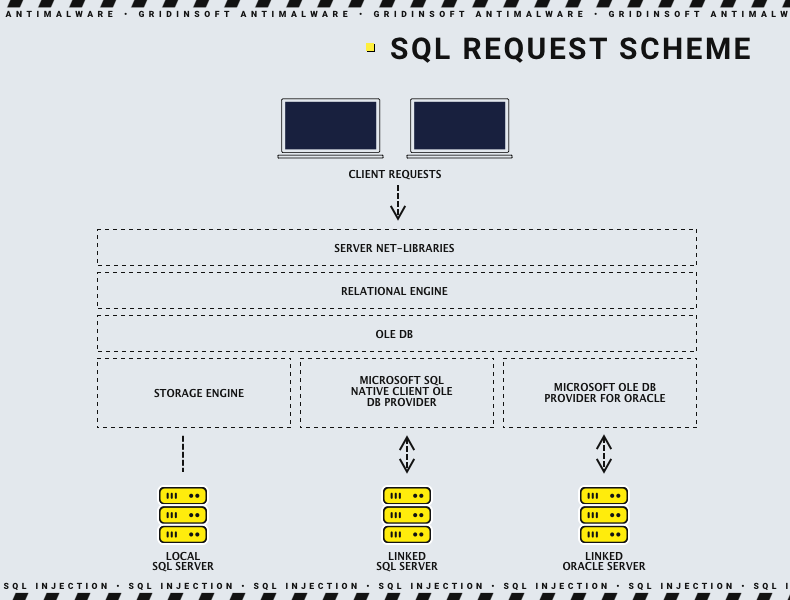
If proper precautions are not taken, sites can easily be tricked into running malicious SQL queries. This attack is called SQL injection, and today we will look at how it works and how to protect your site from it.
What Is a SQL Injection Attack and How Does It Work?
Most large websites or web applications usually have at least one interactive area where content can change depending on the user's entrance. Usually, those are:
- Sites that ask for username and password;
- Online stores that offer products based on a search query;
- Review sites where users are allowed to post content.
When the server receives input data (e.g., a product search), the server translates it into a simple SQL query and then receives and displays the desired data. Or it can create a query to verify the data entered by data from a table (such as username and password) or when adding data to a table for storage (such as a new user's review of a product).
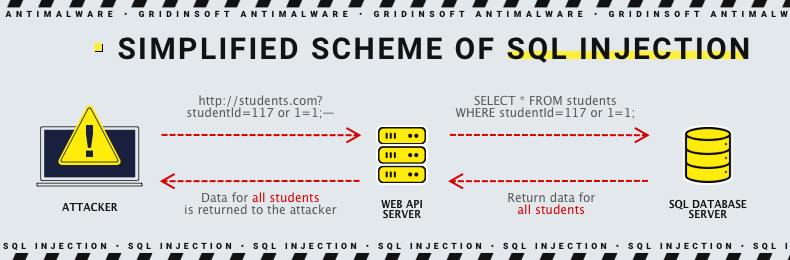
If a site lacks proper protection, hackers can change the data entered, thus creating malicious requests that can lead to unpredictable consequences. They can add partial SQL query elements to the username field to trick the database into displaying, allowing manipulation or deleting critical data only administrators should have access to. For example, adding a single quote in the input field could end the query the database is trying to create. That allows the hacker to use the UNION function to add a new query to it. If nothing prevents the hacker, he can do it in just a few simple steps:
- Check the base for this vulnerability;
- Find out the names of the database's various tables of data;
- In a table, find the names of individual data columns (username, password, credit card number);
- Delete, modify, or display that private data.
SQLi attacks have been well-known in the cybersecurity industry for more than ten years. To detect them, large web companies put in a lot of effort. With each new version, companies like WordPress (which accounts for 30% of the entire Internet) fix the vulnerabilities. Although recently, such attacks have become less prosperous, database managers and site owners are urged to take the necessary measures for web security.
Types of SQL Injections
There are several different forms of such an attack. The following are the most important to be aware of:
In-band SQL Injection
The most common and simple type of attack is almost no different from the above examples. Hackers can see the results of their built queries on the same screen as their input during in-band assaults. For example, that may take place on a product search page. They can use various messages or even error reports to extract useful information.
Blind SQL Injection
But it's not just websites displaying data returned from the database that is vulnerable. In blind SQL injection, the hacker may not see the results of queries executed through his inputs. Sometimes he only needs information about response times, idle pages, and other subtle pieces of data that appear over several queries to gather more useful information slowly.
Using this type of attack, an attacker can uncover the following:
- The presence of this vulnerability in the system;
- The version of MySQL used in the database;
- And other useful information;
- In some cases, this information is enough to build a malicious query.
Out-of-band SQL Injection
In the case of the inability to read blind SQLi results, the attacker can make the database issue a DNS request to his website. Passing a DNS request at the other end (at the hacker's site, which allows him to track requests and activity) provides more information about potential vulnerabilities, which the hacker can use for further attacks.
How to Prevent SQL Injection Attacks?
Using modern technology to keep the site safe, such as WordPress and the like, is essential. It is just as important to update the platform site on time to patch vulnerabilities and use plug-ins and add-ons only from reliable sources. No matter how strong the protection is, even a minor vulnerability in a third-party WordPress plugin can bypass its built-in protection.
Even if your task is to create something individually or you are interested in the subtleties of Web site security, below are some valuable tips to help prevent SQL injections:
Don't neglect updates
Whatever platform or content management system you use, keep it up to date. Hackers love breaches, also known as software vulnerabilities. They could use SQLi to reveal your possible violations, or even to commit the cyberattack. Software updates often contain vulnerability fixes. Software updates give many benefits besides fixing security vulnerabilities. Adapting to recent changes in operating systems, improving the bugs, or introducing new features - ain't that pleasant? This also applies to versions of PHP, MySQL, and other connected elements of your database.
Restrict & Sanitize Inputs
Set restrictions on the entered data. The query will not be executed if the entered data does not meet the requirements. For example, the username should contain only letters and numbers, without special characters, and the phone number should contain only numbers. You can also add a custom input option so that any dangerous characters (e.g., quotation marks) can be recognized and commented out, thus becoming harmless.
Keep sensitive data encrypted
Under no circumstances should such information as passwords in the plain text be stored in the database. Instead, hash the passwords or convert them to a complex string of numbers and letters and use complex algorithms. They should also include a random string of characters that will be added to each password before hashing and other forms of encryption if possible.
Users should not see specific error messages.
Specific Error Messages should not be displayed to the user. Any detailed information displayed when someone fails to act may help hackers find a weak spot in your database. Try to be as general as possible to inform the user about errors without going into details or saying the type or nature of the error. Also, set up a server-side logging function for errors and failed requests. Later, in the event of an attack, this will help you learn more about these actions.
Use a special Scanner to Detect SQL Vulnerabilities
Today, we have many free and paid tools to scan your site or application for vulnerabilities. With their help, you can test your site for various vulnerabilities from SQL injection attacks. Knowing the potential problem and preventing it is better than it will be too late. If you comply with all the above points, the chance of becoming a victim of SQLi in 2026 will be minimal.
