PE32 Ransomware is a recently discovered malware strain that encrypts your files and asks for payment to unlock them. Victims can recognize the files by the sample-specific extension (.pe32), with them becoming inaccessible in normal ways. This malware caught researchers’ eye particularly for using Telegram as a platform for ransom payment negotiations, which is unusual for such malware.
PE32 Ransomware Overview
Cybersecurity researchers have discovered and investigated a new ransomware-type threat. PE32 Ransomware encrypts victims’ files and demands payment for decryption while threatening to leak stolen data. Unlike more infamous ransomware families like LockBit or Conti, which we have separate posts about, PE32 is marked by its immature design and poor security practices. And nonetheless, it remains a significant threat, as it is still able to encrypt the files and disrupt system operations.
It targets both individual users and corporate environments, with ransom demands ranging from $700 to $7,000 for individual machines or servers and $10,000 to 2 Bitcoin (BTC) for corporate targets. Its most distinctive feature is its reliance on the Telegram Bot API for command and control (C2) communication, a departure from the covert HTTP or DNS methods used by traditional ransomware. This choice, combined with its chaotic behavior, makes PE32 a truly unique case study in the evolving ransomware landscape.
Detailed PE32 Ransomware Analysis
PE32 Ransomware operates in a manner that is both non-obvious and confusing, often defying the logical patterns seen in more refined malware. Its behavior is described as noisy and chaotic, making it easier to detect but challenging to analyze due to its erratic execution. The ransomware encrypts files indiscriminately, targeting everything in its path, including files with little to no value, such as Chrome language files, GIFs, or CSS files. This lack of selectivity underscores its poorly designed logic, as it wastes resources on data that offers no leverage for extortion.
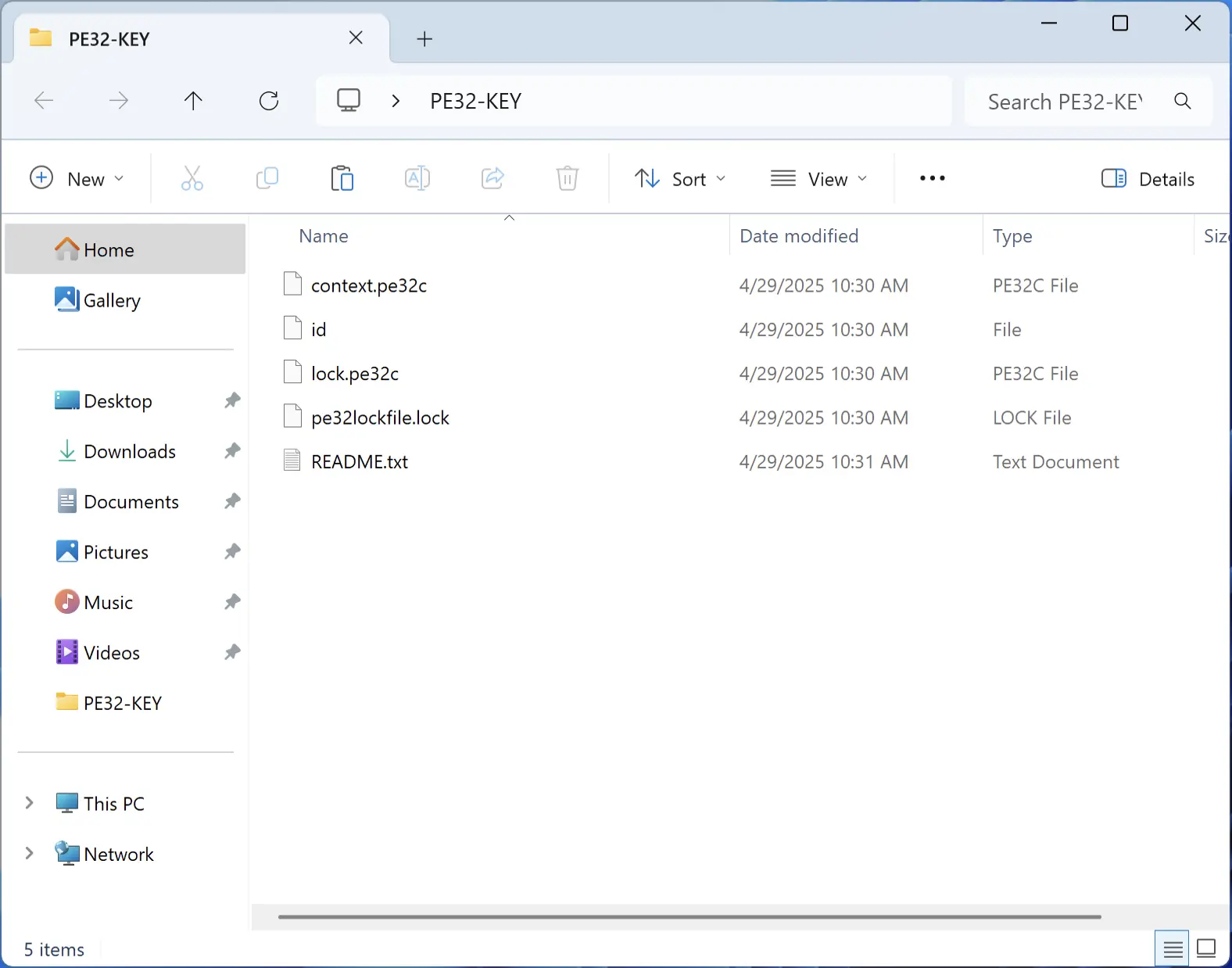
The ransomware’s execution begins with a simple prompt, after which it rapidly encrypts files, focusing on visible folders like the Desktop. It creates a directory named “C:\PE32-KEY” containing files such as “context.pe32c,” “lock.pe32,” “pe32lockfile.lock,” “ID,” and “README.txt”. Encrypted files are appended with the “.pe32s” extension, marking them as inaccessible. PE32 also drops marker files like “pe32lockfile.lock” in every encrypted folder, to indicate completion, but this triggers false positives in detection systems, complicating analysis. Additionally, it initiates disk repair processes by triggering chkdsk.exe via “C:\bootTel.dat,” which can destabilize the system further.
From a technical perspective, PE32 relies on standard Windows libraries, including ntdll.dll, kernel32.dll, crypt32.dll, bcrypt.dll, and schannel.dll, to handle operations like TLS/SSL communication for its Telegram-based C2 channel. Its encryption process is fast, with reported cycles labeled as UltraFast, Fast, and Slow, and it collects system information such as the computer’s GUID, hostname, software policy settings, and supported languages.
This data collection is likely used to avoid infecting systems in specific regions, however, this contradicts the general logic of the ransomware operation, or rather its absence. Also, some functions within the malware appear to serve no practical purpose, contributing to its illogical behavior. For instance, certain code segments suggest conditional logic, but they do not meaningfully alter the ransomware’s operation, just adding to its confusing nature.
Command and Control Communication
PE32 Ransomware’s command and control (C2) communication is a standout feature, relying entirely on the Telegram Bot API. Unlike traditional ransomware, which uses encrypted HTTP, DNS, or custom servers to communicate covertly, PE32 sends all commands and data through Telegram, with no DNS or HTTP requests involved.
The bot token, a critical component for accessing the Telegram API, is hardcoded into the malware’s code, exposing a significant vulnerability. Just imagine the faces of ransomware operators after Telegram blocks their bot. Moreover, this lack of obfuscation means that anyone who extracts the token can interact with the bot, potentially spamming it, issuing commands, or disrupting its operations.
The use of Telegram as a C2 channel has several implications. On one hand, it simplifies deployment for attackers, as they do not need to maintain a dedicated server infrastructure. On the other hand, it introduces significant risks. Security researchers or malicious actors can use tools like Matkap (Matkap Tool) to abuse the exposed bot token, leading to potential denial-of-service attacks or unauthorized access.
Additionally, Telegram’s infrastructure is more traceable than Darknet-based C2 servers, making it easier for law enforcement or security teams to monitor communications. This “unhidden” approach contrasts sharply with the stealth typically employed by ransomware.
Ransom Note Overview
The ransom note is located in the “C:\PE32-KEY\README.txt” file and is notably unconventional. Unlike traditional ransomware, which often directs victims to darknet sites or encrypted communication platforms, PE32 instructs victims to contact the attackers via Telegram, with a backup Gmail address provided.
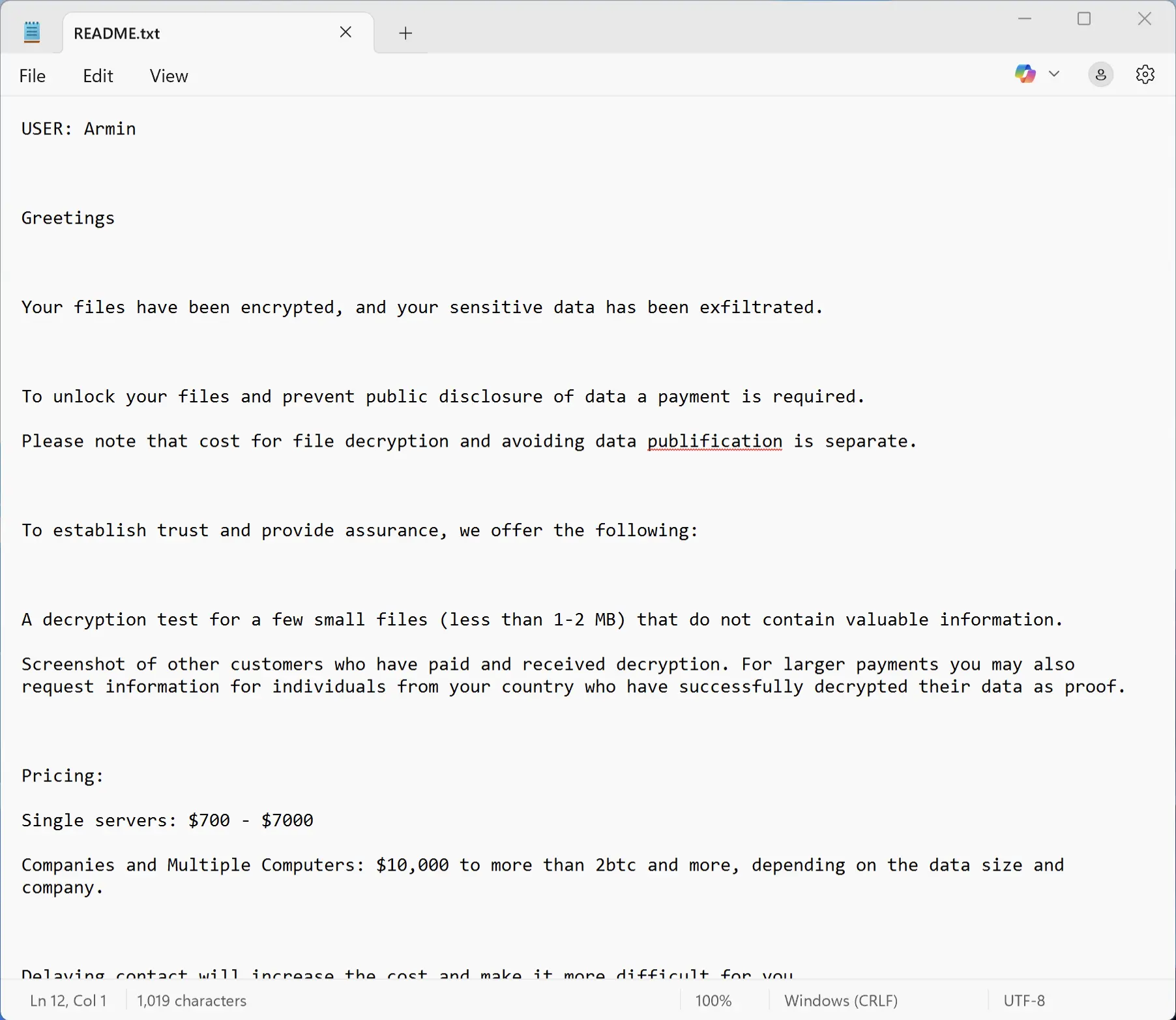
This approach is out of the box, as it leverages public, widely accessible platforms rather than obscure channels. The note typically outlines the ransom demands, emphasizing the dual threat of file encryption and potential data leakage if payment is not made.
The use of Telegram and Gmail makes the ransom process more accessible for attackers, as they can easily monitor communications. However, it also increases their exposure, as these platforms can be monitored or blocked by security teams.
How to Remove PE32 Ransomware?
Although PE32 Ransomware cannot be called very careful in terms of its operation, it nevertheless fulfills its main function. So, removing PE32 Ransomware requires careful action to prevent further damage. Reputable anti-malware software, such as GridinSoft Anti-Malware, is recommended for detecting and eliminating the ransomware. Next, you need to reboot the device into Safe Mode with networking and run the anti-malware solution. It will update its databases and perform a scan, thereby finding and removing all threats.
Manual removal is strongly discouraged due to the complexity of ransomware and the risk of incomplete removal, which could allow the malware to persist or reinfect the system. Before restoring any backups or accessing encrypted files, it is critical to ensure the ransomware is fully removed to avoid encrypting recovered data. After removal, users should scan their systems thoroughly to confirm the absence of residual threats.
Can I Recover Files?
Unfortunately, recovering files encrypted by PE32 Ransomware is challenging without the attackers’ decryption key. As for now, no known decryption tools are currently available for PE32. Paying the ransom is not advisable, as there first is no guarantee that attackers will provide the decryption key, and it may encourage further demands.
The most effective recovery method is restoring files from backups. If backups were maintained and stored in separate locations, such as remote servers or unplugged storage devices, users can recover their data after removing the ransomware. In the absence of backups, third-party data recovery tools may offer limited assistance if encrypted files were partially overwritten, but success is not guaranteed.