
LockBit Ransomware
Each discipline has its own favorites, losers, and average representatives. Ransomware market has them, too - some of the groups appear only to shut down in half a year, others keep going for several years, but have minimal market share. And only the best of the best ransomware is able to keep being a nightmare for people even after 5 years of activity.
LockBit group cannot boast of a pretty long lifespan. The first case of this ransomware was detected in 2019. This gang has all chances to be with us for a very long time - at least not less than Xorist or HiddenTear already do. LockBit developers repeat constantly about the fact that they value their reputation, and always give up the decryption keys when the ransom is paid. Hackers constantly update their ransomware and auxiliary toolkit to match the current realities. Moreover, the developers deny even to talk about the types of data they got from the infected corporations:
“We know the value of reputation, so I refuse to tell this information to you. All data has been deleted from our storages right after the ransom sum is paid.” ━ LockBit developer in the interview.
Uniqueness of LockBit family: what do you need to know
Loud claims about the possibility of the long life of this gang must be proved. LockBit ransomware is known not only by its reputation as a group of “ethical hackers” (later about this), but also for the unique design of their malware. Generally, this ransomware has its own alteration of AES+ECC algorithm. It makes use of multi-threading and ciphers only the first 4 KB of each file. That makes this virus extremely fast: if it was injected successfully, the chances for stopping it before it ciphers something valuable are minimal.
But is the encryption of the first 4KB enough to prevent the decryption? Yes, if you use a very tough ciphering algorithm. And the AES+ECC joint is just one which fits perfectly for this purpose. ECC-like algos are chosen by the U.S. government for encryption of top secret documents that must not be accessed in the case of data leak. And be sure, the U.S. The Department of Defence would not choose a thing with questionable efficiency.
Besides using the unique encryption mechanism, LockBit ransomware also offers a specific stealer for downloading the data of infected companies. Just like with the encryption, it is known for its speed: a lot of cybersecurity analysts say that it outpaces almost all other stealers that are packed inside of the other ransomware.
Any trivial stuff?
Sure, it is hard to be unique in everything. Searching for the unique injection methods becomes useless when you see the amount of companies that ignore the basic rules of data protection. They leave their vulnerable RDP ports open, use the unsecure VPN network, and their employees are opening each email they get. And RDP/VPN breaches together with email spamming hold almost 90% of all ransomware distribution. So why do you need to reinvent the bicycle?
Vulnerabilities of RDP is a real scourge for data security. Since a lot of companies now have the vast majority of their employees working from home, RDP turned into one of the most demanded things. In fact, this solution from Microsoft is pretty good for its purpose. People need access to their workstations in offices, and the remote desktop protocol gives them this access without any complex setups. The unsecure ports that are set by users because of their low skills turn into a huge breach, since those ports allow anyone to connect to the corporate network and start brute force attacks.
Ransomware injection through the unsecure VPN is a relatively new thing. Fraudsters started using it only in 2021, and this injection method is not very widespread. Fortunately, setting up the VPN (and choosing the VPN provider) is usually done by qualified staff - system administrators, for example. But in some cases even a well-designed VPN connection which, however, uses an outdated version of the basic utility can be fatal. CVE-2018-13379, which was used during the attack on multiple European companies, is just that case.
Ethical hacking: what hides behind this term?
Crooks are always crooks, regardless of the mottos they hold in their hands. LockBit group tries to create an image of a 100% honest ransomware group that always does what they promise. However, that is not a single element of the ethical hacking, which they try to follow.
Not so long ago, in June 2021, a lot of ransomware developers agreed about the list of sectors that must not be touched by ransomware. Previously, ransomware developers implemented such ideas as their own initiative, so the majority of groups were not restricted at all. Nonetheless, such a “meeting” gave a large boost to the spreading of ethical hacking.
Ransomware developers from all over the world agreed to avoid attacking governmental and healthcare institutions, schools, universities, and other educational establishments. A lot of groups also agreed to evade the infrastructure companies (likely because of the noise after the attack on Colonial Pipeline). Is it any good? Sure. Does it justify the ransomware developers and distributors? Doubtlessly, not.
Known LockBit variants and victims
One of the latest well-known attacks performed by LockBit is its breaking into Accenture, an Irish-based IT-consulting company. Ransomware group decided to repeat the success of previous loud hacking case - cyberattack on Acer Corporation, which ended up paying the $50 million ransom after the ransomware attack in March, 2021. Accenture was asked for the same $50 million, and it is much bigger than an average ransom asked by LockBit group ($85,000).
In total, LockBit has the achievement list of 61 companies (including Accenture). Among them you can also see Bangkok Airlines (one of the largest air transport companies in the Asian region), Royal Porcelain and Beardow Adams. The list of all extensions used by LockBit is quite short:
- .abcd
- .lockbit
- .lock2bits
- .luckyday
It seems that its developers want everyone to know the exact name of the group which attacked them. Nice practice, especially when we remember that they are very proud of the actions they do. They did not even implement any changes in their extensions after applying the 2.0 version, which has significant changes compared to the first version.
LockBit 2.0
LockBit 2.0, released in August 2021, has the same core features - AES+ECC cipher, only 4KB of each file are encrypted, and a spyware module - but has the operations speed significantly buffed. As an exfiltration toolkit, hackers opted for Stealbit and rclone - tools that allow to extract and upload data to the cloud storage. There is no clear reason for such improvements - LockBit 1.0 was far faster (twin- or even triplefold) than any of its counterparts. Another thing that was changed in 2.0 version is the list of possible locations for stolen data storage. In the first version, fraudsters were forced to specify the cloud storage, which is not the best solution: cloud hosting can easily ban the crooks’ account after the request of the attacked company. Now, they are free to choose between cloud storage and their own disks, despite having rclone as a recommended option.a
Comparison of LockBit 2.0 operations speed with counterparts
| Ransomware | Encryption speed | Time needed to encrypt 100GB of files | File downloading speed | Time needed to download 10GB of stolen data |
| LockBit 2.0 | 373 MB/s | 4m28s | 83.46 MB/s | 1m59s |
| LockBit | 266 MB/s | 6m16s | 83.46 MB/s | 1m59s |
| Cuba | 185 MB/s | 9m | 4.82 MB/s | 5h45m46s |
| BlackMatter | 185 MB/s | 9m | 4.82 MB/s | 5h45m46s |
| Babuk | 166 MB/s | 10m | 4.82 MB/s | 5h45m46s |
| Sodinokibi | 151 MB/s | 11m | 4.38 MB/s | 6h20m31s |
| Ragnar | 151 MB/s | 11m | 4.82 MB/s | 5h45m46s |
As you can see, even the old variant of LockBit ransomware outpaces all other ransomware groups. Moreover, even though LockBit 1.0 was using cloud storages to keep the data stolen from corporations, the downloading speed was pretty high. Low downloading speed of counterparts is explained by the usage of free cloud storages, which does not provide a high-speed connection.
Though, LockBit is the fastest ransomware only among massively-used ones. A sample of ransomware, dubbed Rorschach, is at least twice as fast as Lockbit 3.0. It uses a combination of stream and elliptic-curve cryptography keys, which allows it to be even faster, retaining the proper reliability of the cipher. Fortunately, this beast is more likely to be a technology demonstrator prototype, rather than a ready-to-use ransomware. As we described above, to make ransomware really effective, a lot of additional software and infrastructure is needed. However, nothing stops LockBit from adopting the techniques implemented in Rorschach for their good.
LockBit 3.0
Constant introduction of technical advancements is a signature element of the LockBit gang, and we mentioned it above. And LockBit 3.0, also known as LockBit Black, contains plenty of them. New versions of ransomware became slightly faster – obviously, making things faster is their forte – and brought a pack of architecture changes, as well as new options for post-penetration activities.
In 3.0, the main payload may be customised on the stage of compilation by multiple parameters that drastically alter the malware behaviour upon injection. Among them are the ability to switch the system to Safe Mode – a popular way to circumvent anti-malware software – and password protected execution conjoined with sample ciphering. The last two elements are a pretty novice anti-analysis approach. Without having a password, which is available in the affiliate’s panel, it is impossible to decrypt the sample and make it run. Still, there is the ability to create a “passwordless” sample, but it requires higher privileges.
The ability to encrypt the sample with different algorithms, together with the use of a unique sample for each attack, makes LockBit a pretty tough nut when it comes to static detection. In fact, such methods almost nail any database-backed detection, as all new samples will be different from already existing and present in databases. Only advanced security software will be helpful – ones that feature heuristic detection based on in-system actions and network activity.
Another significant element of the 3.0 version is the introduction of the Bug Bounty program. For the ransomware world, it is definitely an innovation. Never before hackers were offering outsiders to test their software for bugs and issues for pay. This is probably one more attempt of the LockBit gang to be “transparent and honest” – at least to the extent that cybercriminals can be described as honest.

Shortly before the 3.0 release, the ransomware gang faced a counteraction from the company they hacked. Entrust, the provider of hardware and software solutions for electronic identification, launched a DDoS attack to mischief the gang which started publishing the data they stole from the corporate network. As a result, the onion site where crooks were publishing the leaks was not accessible. After dealing with the attack, LockBit decided to introduce yet another way to press on their victims – by launching a DDoS attack on the servers. Some say it is a new variant of triple extortion, but crooks do not ask about additional ransom for stopping the attack – they just force victims to pay in that manner.
Takedown, Member Detainment and Identity Reveal
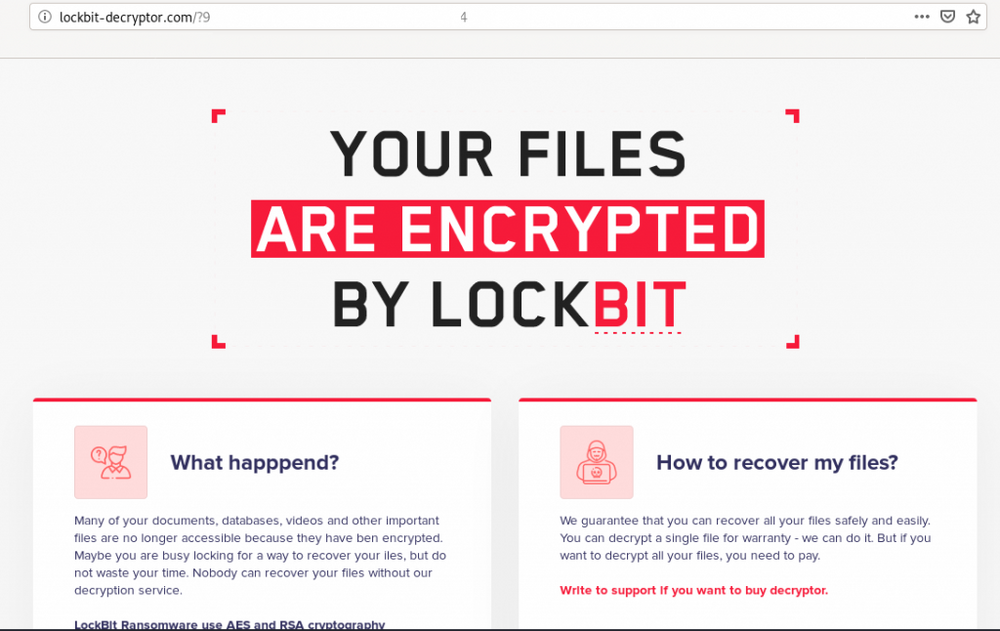
On February 19, 2024, a selection of Darknet sites that belong to LockBit started displaying a law enforcement takeover banner. The main role in the takeover was assigned to Europol and UK NCA in particular. The following day, they made the page look like before, but instead of the listings of hacked companies, it was displaying a bunch of news releases and data leaked from the hacked network infrastructure of LockBit.
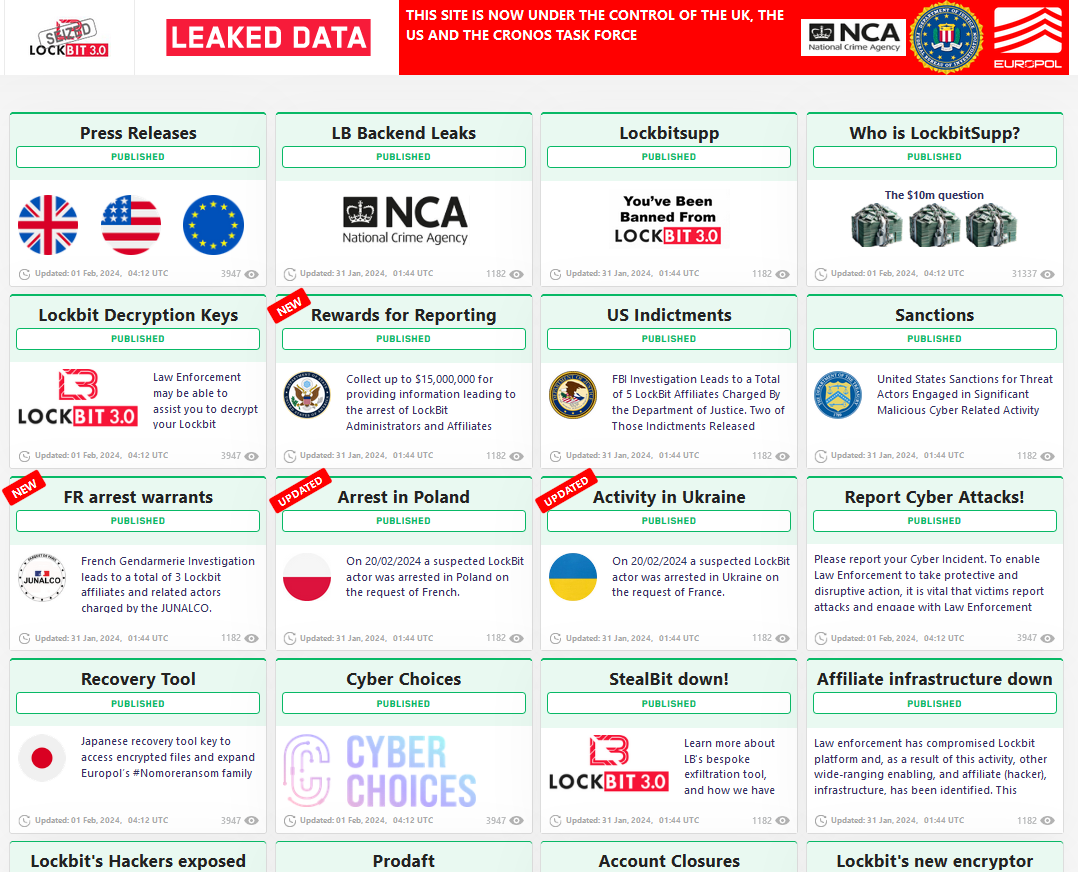
Among the interesting things are the screenshots of the ransomware admin panel, network assets architecture and stolen data/decryption keys of ransomware victims. Law enforcements even managed to get the identity of an infamous LockBitSupp – one of the group chiefs, who used to offer $10 million in reward for anyone who reveals his identity. Well, it looks like the man behind this nickname was not only a good gambler, but a skillful negotiator: the day when law enforcement promised to publish his info a post saying he engaged with them appeared. At what cost – this only participating parties know.
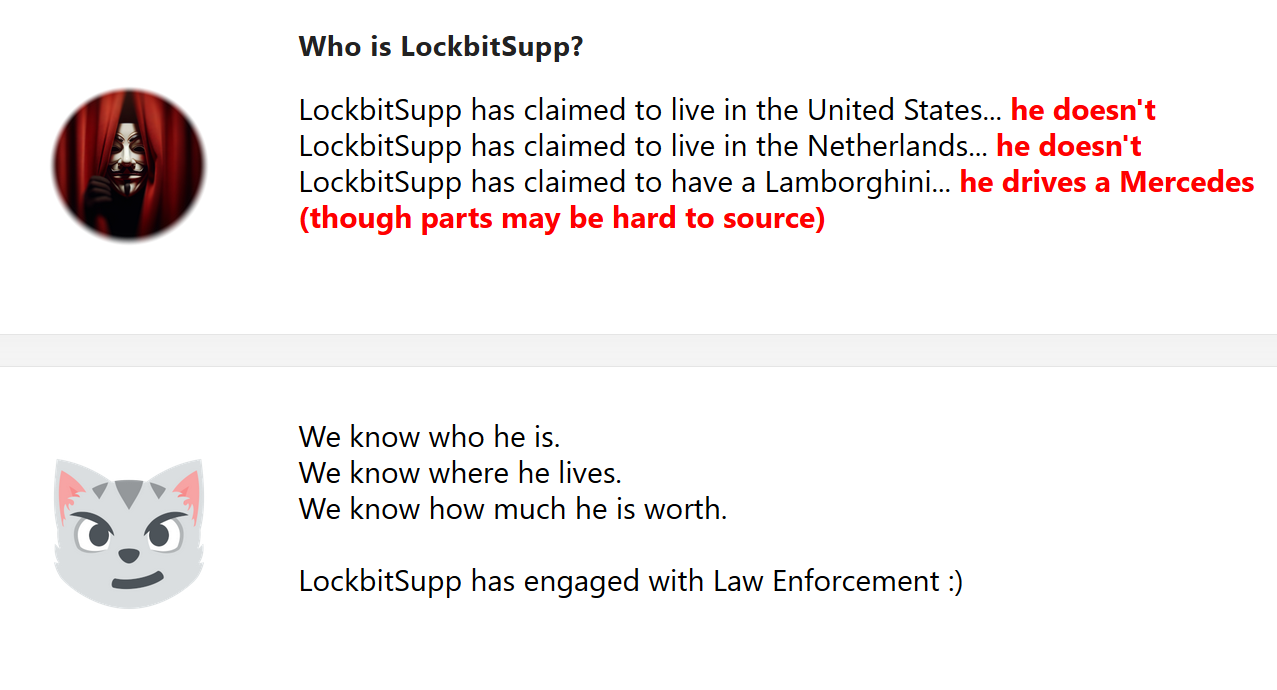
Will this be the end of LockBit? The total disruption and takeover of the network infrastructure is a serious blow not only to the operations, but also to the image of the group. They faced attacks of different kinds before, but emerged victorious. This will not be the case this time, even though they claim having their reserve servers saved from the attack. Even if we see the LockBit comeback, that will not be that LockBit, of 3.0 times, with interviews to threat analysts and daring, if not daredevil attacks.
Die Another Day
Four days following the takedown, LockBit ransomware… managed to get back into business. The comeback was announced with a PGP signed message published by LockBitSupp, where the latter was explaining the situation from his point of view. In particular, he named the PHP vulnerability that was supposedly used to hack into the system. But overall, the hacker claims that the situation was possible “because he has become lazy”.
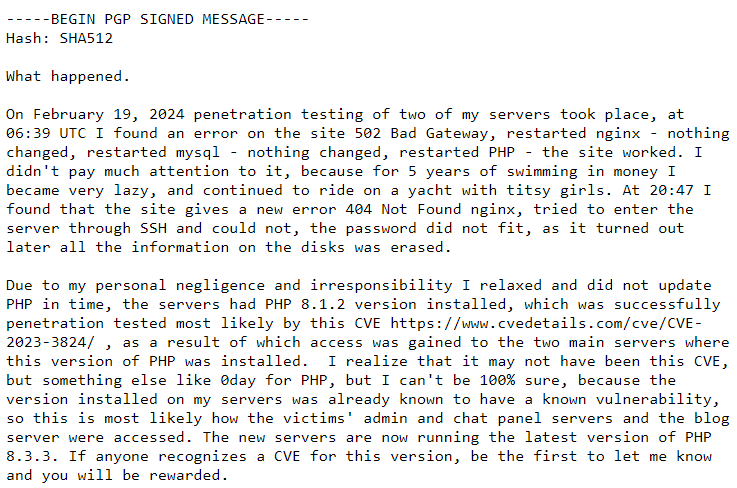
Aside from the reasoning, LockBitSupp also supposes that law enforcement agencies had access to the system for quite some time. The reason why they started the action is the publication of a large data package leaked from Fulton County. Inside, there were some quite interesting info regarding Donald Trump’s court cases – a thing that in hacker’s opinion is a valid reason for the FBI to shut down a threat actor. Not multi-million ransoms and attacks on colleges and entire counties, but some bureaucracy around the ex-president.
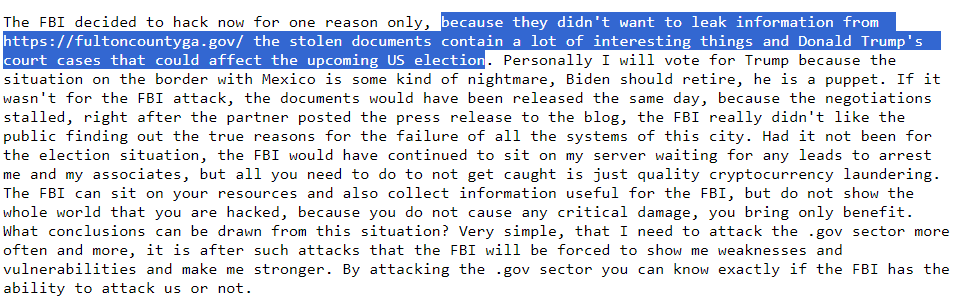
The persons detained under Operation Cronos appear to be really related to LockBit, though their role is in doubt. Both visual clues and claims from LockBitSupp indicate that these men are either involved in money laundering or server infrastructure admins, not affiliates. Another clue for the latter is the fact that the attacks kept on rolling at the same rate – at least the new leak site was filled up rather quickly.
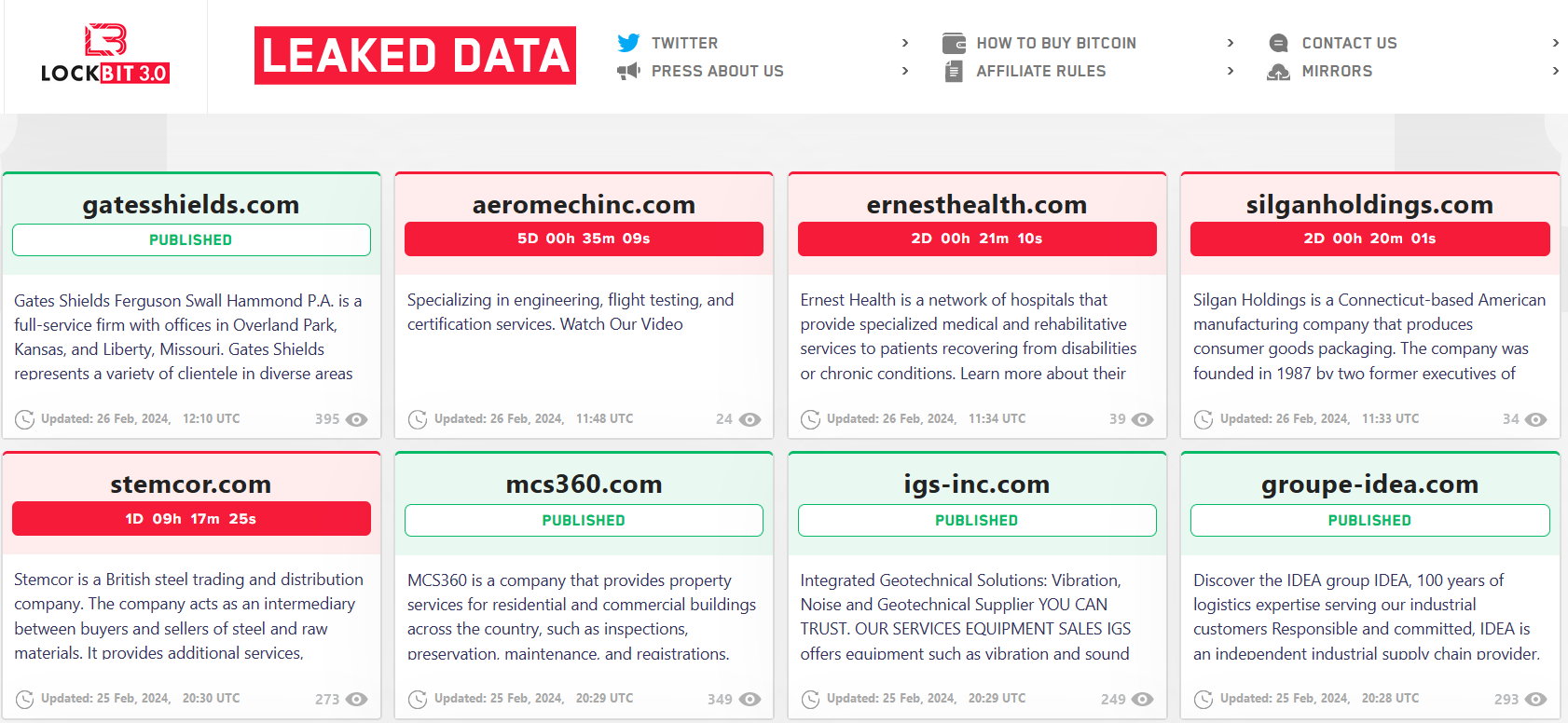
It is still unclear how strong the impact of captured decryption keys, builders and other elements of the infrastructure. The hackers, obviously, claim that no large companies’ keys were leaked, and all that agencies boast of are the decryptors to the attacks with miserable ransoms; they also name the estimated amount of leaked keys at 2,000 out of 40,000 total victims. Law enforcement agencies, on the other hand, do not uncover what these keys are about, just offering every company who suffered the hack to contact them for the decryptor.
