Recent research from the CheckPoint Research team revealed a new ransomware sample that can potentially beat all samples currently present on the market. They coined it Rorschach, and already say that its unique properties can make it dominant ransomware pretty quickly. We told about this malware in a recent news post, and now it’s time for a more detailed analysis.
Rorschach Ransomware Uses DLL Sideloading
One of the most unusual properties of a new ransomware sample is the way it hooks up in the infected system. On a test system, malware used a DLL sideloading technique to load its own libraries. This approach is also called DLL search order hijacking, as it exploits the mechanism used in Windows to allocate the libraries needed to solve the dependencies. In the case of Rorschach, malware calls for the copy of a genuine winutils.dll library using the Palo Alto Network’s Cortex XDR Dump Service Tool. Using it does not trigger anti-malware engines, as it already belongs to one. Attempting to stay as low as possible is not new for hackers, but this method is groundbreaking.
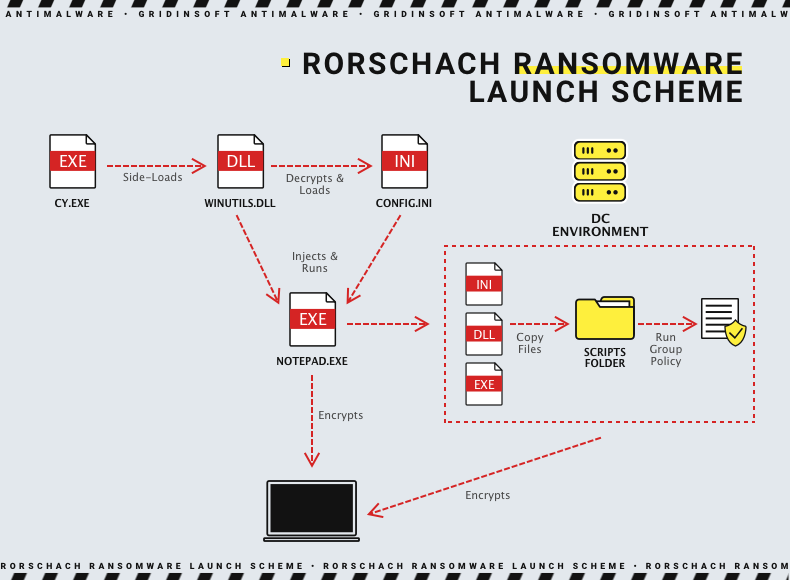
Using the cy.exe (the process of the mentioned Dump Service Tool), malware loads a spoofed instance of winutils.dll, that actually contains the payload. The library is getting unpacked and spawns the config.ini file. Then, the latter is used together with the part of the previous .dll file to create the exact ransomware process. Researchers witnessed the name notepad.exe, however, it is obvious that all the names may change from one attack to another.
Detection evasion
As any other advanced malware sample, Rorschach uses a line of anti-detection tricks. Aside from exploiting the legit tool to call for a library, it spawns processes in a suspended mode. To make the analysis even harder, it gives the processes falsified arguments – rows of number “1”. Each row corresponds to a specific command, which is parsed on run, resulting in normal execution. Commonly for malware from ex-USSR countries, Rorschach will refuse to run in a system that contains specific system languages.
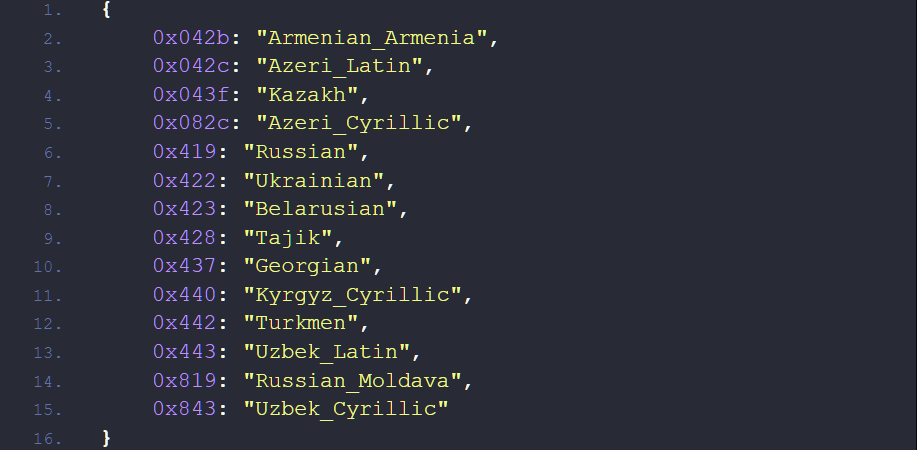
To make any post-factum analysis harder or even impossible, malware wipes all the event journals by sending the corresponding command to wevutil.exe. Additionally, it gets rid of Volume Shadow Copies – the default Windows backup method that copies system volume. To ensure that nothing will stop malware from execution, it stops a list of services from running using net.exe stop command. All these things, however, are not new: most other ransomware samples do the same trick to make any recovery or investigation more complicated.
List of suspended processes and services
| Processes | ||
|---|---|---|
| sql.exe | wrapper.exe | dbsrv12.exe |
| oracle.exe | WinSAT.exe | encsvc.exe |
| ocssd.exe | mydesktopservice.exe | firefox.exe |
| dbsnmp.exe | ocautoupds.exe | tbirdconfig.exe |
| synctime.exe | mydesktopqos.exe | dbeng50.exe |
| agntsvc.exe | ocomm.exe | sqbcoreservice.exe |
| isqlplussvc.exe | steam.exe | thebat.exe |
| xfssvccon.exe | powerpnt.exe | infopath.exe |
| winword.exe | excel.exe | outlook.exe |
| wordpad.exe | msaccess.exe | mspub.exe |
| visio.exe | onenote.exe | thunderbird.exe |
| Services | ||
|---|---|---|
| stc_raw_agent | RTVscan | QBCFMonitorService |
| sql | QBFCService | zhudongfangyu |
| svc$ | QBIDPService | YooBackup |
| memtas | Intuit.QuickBooks.FCS | VSNAPVSS |
| mepocs | vss | PDVFSService |
| sophos | VeeamTransportSvc | BackupExecVSSProvider |
| backup | VeeamDeploymentService | AcrSch2Svc |
| GxCIMgr | VeeamNFSSvc | BackupExecAgentAccelerator |
| DefWatch | BackupExecAgentBrowser | BackupExecDiveciMediaService |
| ccEvtMgr | BackupExecJobEngine | BackupExecRPCService |
| ccSetMgr | BackupExecManagementService | AcronisAgent |
| SavRoam | CASAD2DWebSvc | CAARCUpdateSvc |
Self-spreading approach
Here things are back to strange and unusual. Rorschach malware is able to take advantage of infecting the Domain Controller – the key component of any network. If this ransomware detects itself running on a DC, it prepares the environment for spreading itself to other devices by adding its files to the script folder. Then, malware creates a Group Policy that allows malware to copy itself to the %Public% folder of all machines in the network. Finally, it uses taskkill.exe utility to stop the processes we mentioned above on the subordinary machines as well. After that, Rorschach creates another group policy that makes it run on the user logon.
Still, something similar was already detected in LockBit 2.0 samples. An infamous ransomware gang uses pretty much the same trick to infect the network after breaching the DC. Same as LockBit gang’s brainchild, Rorschach performs self-destruction after finishing the encryption process. That makes investigating the attack even harder. However, there is one thing Rorschach overwhelmed LockBit in – encryption speed.
Encryption Methods
Usually, ransomware applies RSA-1024/2048, AES-256 and their derivatives – pretty standard symmetrical cryptography. These algorithms are good and reliable, but require significant computational power. Otherwise, it will take a pretty long time to cipher a large array of files – a typical situation during ransomware attacks. Some samples rely on multi-threading to increase the encryption speed, but the most advanced gangs switch to elliptic-curve cryptography (ECC) and decrease the file portion to encrypt.
Rorschach is among them, using a combination of hc-128 and curve25519. The former, actually, is not elliptic, but that adds even more problems to attempts of deciphering it. Moreover, 128-bit encryption is faster to implement. The resulting cipher is applied only to a small part of the file – which makes the process even faster. As a result, Rorschach is able to cipher the sample of 220 thousand files in 4.5 minutes. Even LockBit 3.0, which boasted of extreme encryption speed, spends around 7 minutes for the same purpose.
Relation to other ransomware gangs
At this point, there is no information about the use of Rorschach ransomware by any threat actors or cybercrime gangs. Yet for sure, it may change soon – considering its advancements over other ransomware samples. Despite no clear relations, the ransomware still shares several elements with samples present on the market.
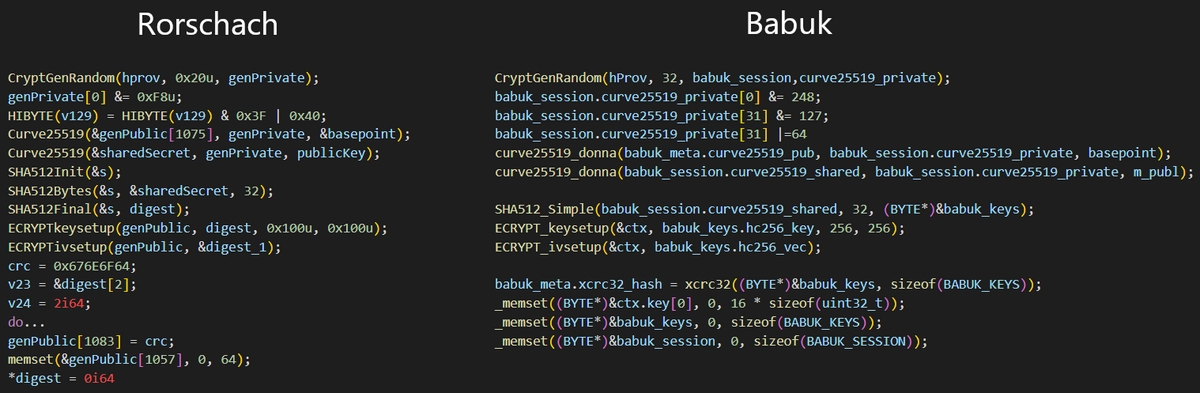
First and foremost, its codebase has common elements with Babuk ransomware. It is not the first case when it is used, as the source code of this ransomware was leaked back in July 2021. The way malware manages itself through the processor threads and code responsible for weeding out launches in ex-USSR was definitely borrowed from LockBit 2.0. Meanwhile, ransom note shares some sections with DarkSide and Yanluowang ransomware.
How dangerous is Rorschach?
Most definitely, it may become a new favourite on the market. Currently, the most successful ransomware group is LockBit – because of the efficiency of the software they use in attacks. It can not only cipher the files extremely fast, but also extract them to the external storage in order to perform double extortion. Rorschach already beats LockBit 3.0 in ciphering speed; create a faster data extraction way, and you’d get an absolute dominator.
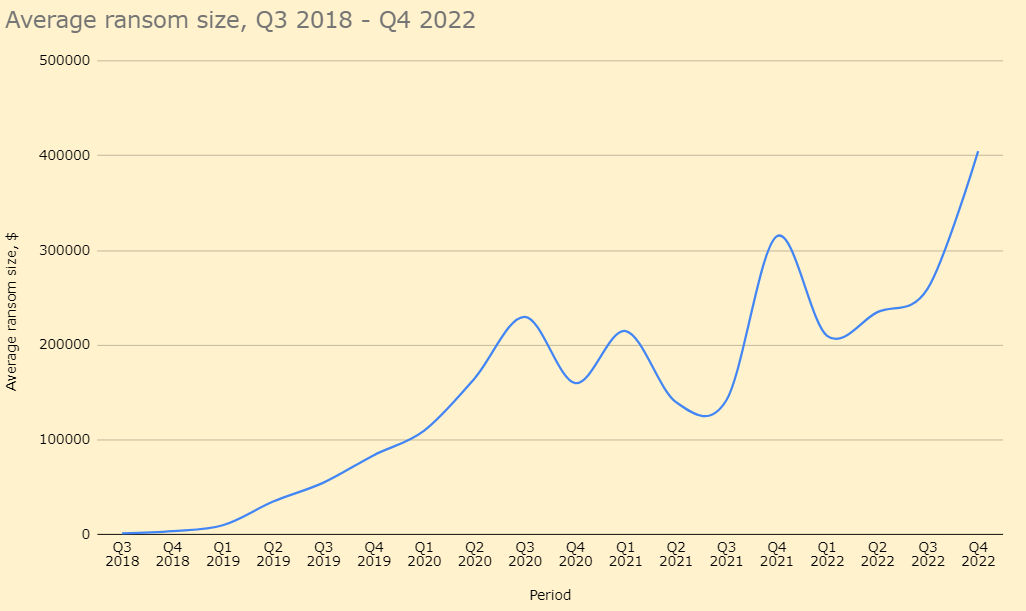
Ransomware attacks remain a №1 threat for companies. Average ransom sizes peaked at $400,000 and are unlikely to go down, especially considering that more and more victims avoid paying ransom. Hackers will ask for more and more money to compensate quantity with quality – a common tactic of theirs. Data may be restored in this or another way, but no one will prevent it from getting published in the Darknet or elsewhere. The only way to avoid all these problems is to protect your organisation from attacks of all kinds.
How to protect against ransomware?
Use a security solution that features a zero-trust policy. Only a zero-trust approach towards scanning, and all other features that are meant under zero-trust policy can effectively repel exploitation hazards, like the one we mentioned above. Moreover, it will additionally protect from zero-day vulnerabilities – considering that they’re pretty hard to counter in any other way.
Protect the internal network. Any malware cannot work properly without a callback to the C2 server. Giving it no chance to do that, in addition to making it troublesome to at least introduce one to your network will work out pretty well. Network Detection and Response solutions will not only secure your network connections, but also provide all the information needed to examine each attack (or its attempt).
Update your software as often as possible. I mentioned using zero-trust anti-malware programs as a remedy, but it is better to not give malware a chance at all. Software vendors release minor updates with bug fixes and vulnerability patches pretty often, so consider installing them. Currently, most breaches that happened with the use of vulnerability exploitation happen because of the use of an outdated program version. Don’t be the enemy for yourself!
Be careful with files that come from the Internet. Most often, people consider files from email inbox safe – and that is the key mistake. A huge amount of attacks were carried out through infected email attachments – and this sad statistics are going only up with time. Files downloaded from third-party websites are not safe as well, and should be scanned before launching.




