The LockBit ransomware group released the LockBit 3.0 malware, at the same time introduced its own bug bounty ransomware program, and also announced that it would accept ransoms in the Zcash cryptocurrency.
Bleeping Computer recalls that LockBit appeared in 2019 and has since become one of the most active threats, accounting for about 40% of all ransomware attacks in May 2022.
You might also be interested in: Conti vs. LockBit 2.0 – a Trend Micro Research in Brief.
Journalists say that over the weekend, the group released an updated version of its RaaS malware (LockBit 3.0), which hackers have been beta testing for the past few months. At the same time, it is noted that the new version of the malware has already been used in attacks.
Also, along with the release of a new version of the ransomware, the hackers also introduced their own bug bounty program.
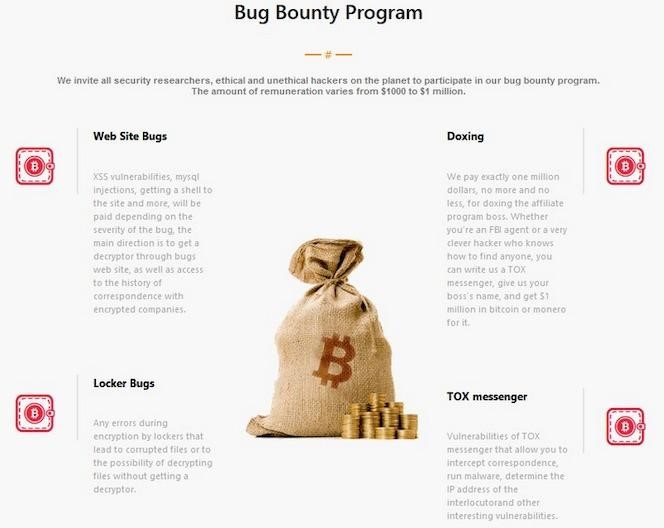
It is easy to guess how exactly the hackers intend to use the vulnerabilities acquired in this way. In addition, the group offers rewards not only for bugs, but also for “brilliant ideas” to improve the work of their ransomware, as well as for doxing the head of their own affiliate program. The Hackers website lists the following categories of awards.
- Site errors: XSS vulnerabilities, MySQL injections, shells and more will be charged based on the severity of the error. The main vector is getting a decoder through bugs on the site, as well as gaining access to the history of correspondence with encrypted companies.
- Locker Errors: Any encryption errors resulting in file corruption or the ability to decrypt files without a decryptor.
- Brilliant Ideas: We pay for ideas. Please write how we can improve our website and software, the best ideas will be rewarded. What is interesting about our competitors that we do not have?
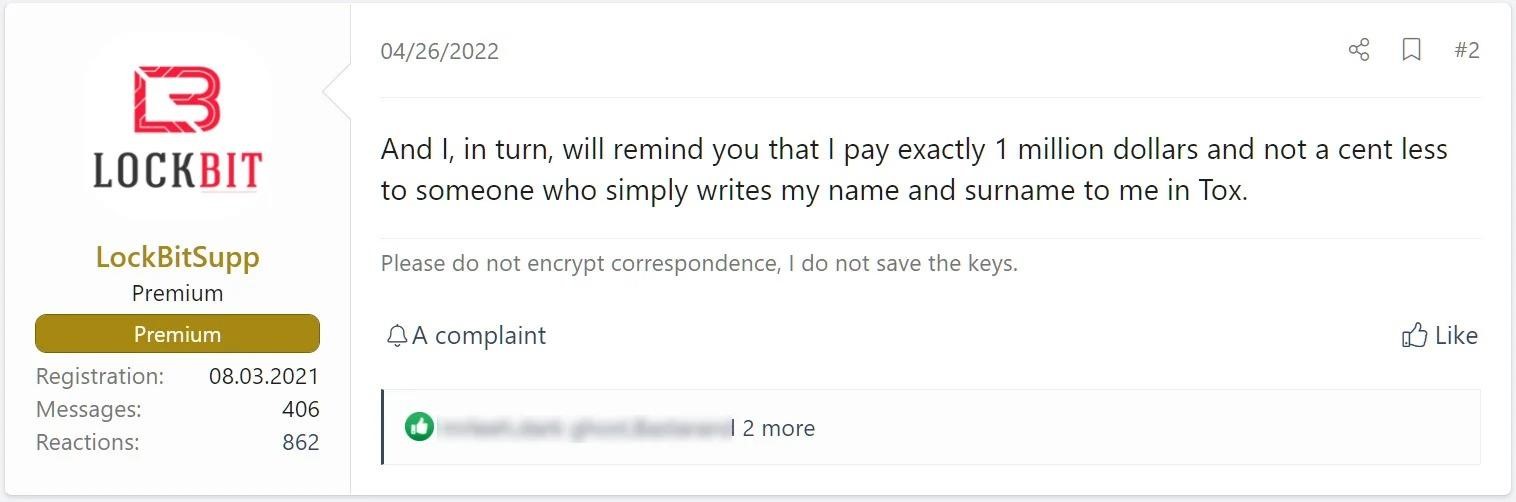
- Doxing: We will pay exactly one million dollars, no more and no less, for doxing the affiliate boss. It doesn’t matter if you are an FBI agent or a very smart hacker who knows how to find anyone, you can write to us on TOX messenger, tell us the name of the boss and get a million dollars in Bitcoin or Monero for it.
- Messenger TOX: vulnerabilities in the TOX messenger that allow intercepting correspondence, launching malware, determining the IP address of the interlocutor, and other interesting vulnerabilities.
- Tor network: any vulnerabilities that help get the IP address of the server where the onion site is installed, as well as gain root access to our servers and onion domains, followed by a database dump.
It should be noted that the proposal to dox the head of the LockBit affiliate program, known under the nickname LockBitSupp, as an experiment, appears not for the first time. For example, in April of this year, the group offered a million dollars to anyone on the XSS hacker forum who could recognize at least the first and last name of LockBitSupp.
Journalists also note that now on the site of the hack group, visitors are greeted by a gif with animated icons of the Monero and Bitcoin cryptocurrencies, which were previously accepted for paying ransoms. But now the logo of the Zcash cryptocurrency, which is known for its increased privacy, joined them.

Another innovation: a new ransomware model that will allow attackers to buy data stolen during attacks from LockBit. It has been noticed that one of the JavaScript files on the updated grouping site contains a modal dialog that will allow purchasing stolen data. Apparently, the data will be offered for purchase and download either through a torrent or directly through the site.
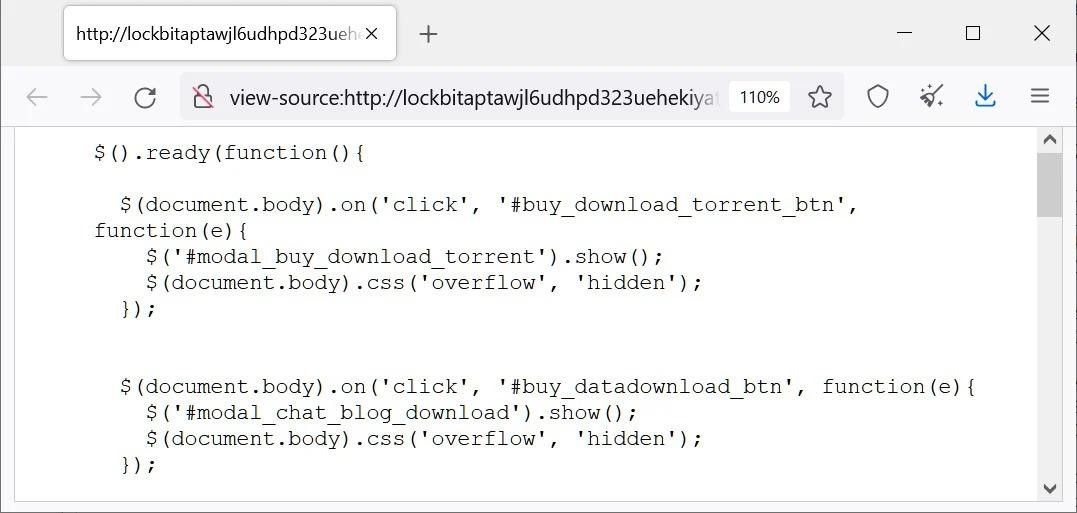
Since the LockBit 3.0 website has yet to release the details of the victims, it is not still clear how this innovation will work and whether it will be enabled anytime soon.




