Trend Micro, a Japanese IT security company, has published a thorough comparison of behaviors of two major ransomware groups: Conti and LockBit 2.0. Here you can read a shorter summary of what they found out.
Conti and LockBit 2.0 are outstanding operators regarding how many targets they managed to attack. The period analyzed is from November 2019 to March 2022. Within that timespan, Conti went offensive on 805 companies while LockBit 2.0 reached the ominous 666. These two ransomware operators are responsible for almost 45% of all the extortion attacks worldwide within the named period. And that is considering that LockBit reached its current activity level only in July 2021. Taking into account the rumors about the Conti group end, LockBit 2.0 might beat Conti in numbers of successful attacks even sooner than in August 2022, which was the earlier assessment.
Victim Companies Locations
Location-wise, the strategies of the two gangs show significant differences. Although North American and Western European companies lead by the number of enterprises targeted by both racketeering groups, that’s where the similarities end and differences begin. Conti’s much more focused on North America: more than two-thirds of this operator’s victims are there. The second position goes to Europe, and the rest, which is 7%, are all other regions.
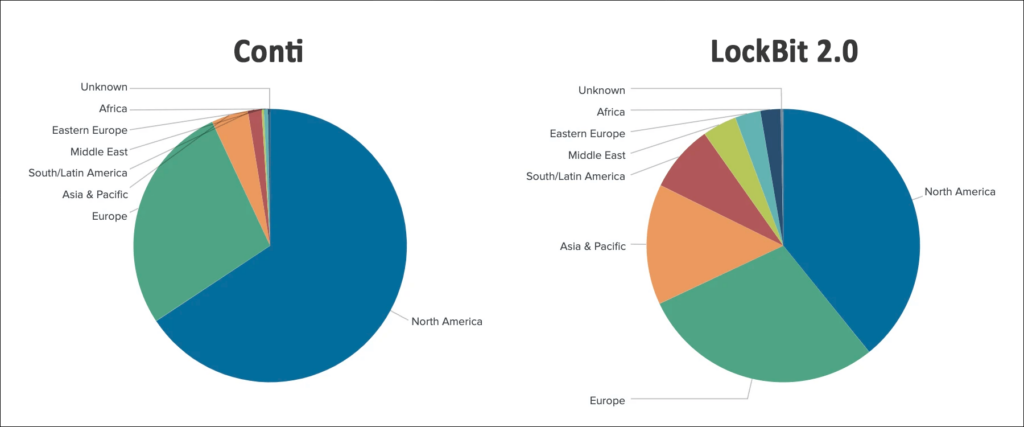
As for LockBit 2.0, everything’s different. Both Western Europe and North America occupy roughly four-sixths of targets on LockBit’s victim list; America takes a larger part, of course. But unlike in the Conti case, the remaining number of victims (more than Western Europe, around 20% of the total) is distributed in favor of Asia and the Pacific, another considerable part goes to South America, and the remaining targets are in the Middle East, Eastern Europe, and Africa.
The distribution of targets in the case of LockBit is much closer to the distribution of the gross domestic product worldwide. Except for the Asian region. China‘s economy obviously dominates there, and China’s GDP is the world’s highest. However, this country is seemingly “spared” by ransomware actors in question. In the Asia and Pacific region, Conti makes a clear accent on victimizing English-speaking countries: Australia, New Zealand, Singapore, and India. We will reflect on the reasons for that in the conclusions to this item.
Industries and Company Sizes
Victimized industries are mostly the same for both operators, and no specific sphere is targeted purposefully by either ransomware group. The top most attacked industries are the same for LockBit and Conti: financial, IT, manufacturing, materials, professional services, and construction.
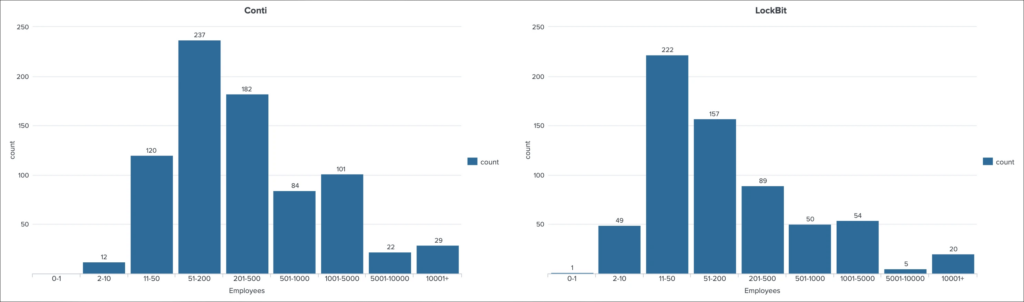
What is more curious is the difference between the size of attacked companies. Conti concentrates on enterprises with a relatively large number of employees. For instance, 237 attack cases (the highest number, considering Trend Micro’s selection of company sizes) fall under enterprises with 51-200 employees. LockBit’s maximum (222 attacks) is directed against companies employing 11-50 people. As for larger entities (201-500 employees), Conti’s haul here is 182 attacks and LockBit’s – 89. One of LockBit’s victims, according to Trend Micro, is a company consisting of one person.
Conclusions
The fact that Hong Kong is an alleged location of the LockBit gang leader might explain the group’s discretion in attacking China. An official investigation might critically jeopardize the group’s commander, his haven, and further operations.
In the case of Conti, everything is different. This ransomware group declared its support of Russia in the context of Russia’s invasion of Ukraine. Therefore, Conti attacks Russia’s opponents, mainly the USA, and holds its hand from victimizing Russia’s allies, such as China and most of the former Soviet Republics.
The distribution of LockBit’s victims and companies arguably proves the group’s claims to be out of politics and only financially motivated. Earlier, LockBit 2.0 even made a media performance promising to disclose data stolen from Mandiant, a cyber security giant, at the full tilt of the RSA cybersecurity conference. What preceded this prank was Mandiant report on LockBit’s connection with the Russian ransomware gang Evil Corp, which LockBit strictly denied.