Conti operators shut down the remnants of the public infrastructure. Two servers on the Tor network that were used to publish victims’ data and negotiate ransoms are down. The Conti News website’s admin panel and the stolen information storage were closed a month ago, and the list of non-payers has not been updated all this time.
The departure of the last Conti servers offline was noticed on Wednesday, June 22, by the participants of the DarkFeed project (ransomware monitoring). On Friday, according to BleepingComputer, they were still unavailable.
Conti completed the shutdown
In the second half of May, the group behind Conti began to wind down operations related to this ransomware. The servers used for communications and data storage were taken out of service, the service for negotiating with victims was disabled, and information about successful attacks was not uploaded to the site.
The organized crime group put up a smoke screen to hide these works from outsiders. A single participant was still active on the site. He continued to publish some stolen data (in fact, the results of previous attacks) and teased one of the latest victims – the government of Costa Rica. A massive Conti attack on government agencies in Costa Rica occurred in April. Attackers managed to steal 672 GB of data from 27 organizations and stop several vital services. As a result, a state of emergency was declared in the country.
The decision to abolish the Conti brand is overdue, primarily due to increased attention from the cybersecurity community and law enforcement agencies. Attacks of malefactors became too bold and loud. The recent leakage of internal data of organized crime groups pushed some Twitter users to collect dossiers on criminals. The US authorities, for their part, announced a reward of up to $10 million for the heads of the crime syndicate leaders.
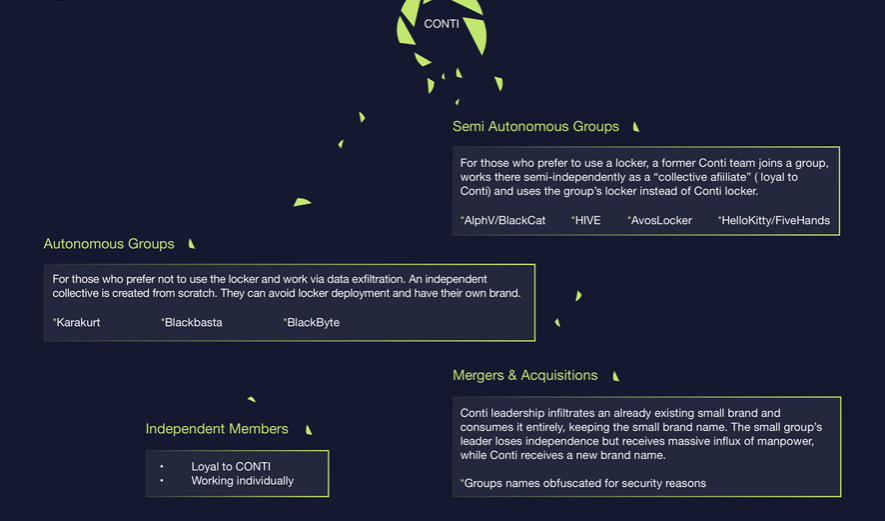
Conti operators have actively established partnerships and willingly taken less fortunate colleagues under their wing, they can now afford to work under other brands. They might join smaller groups and keep friendly relations with their leaders and specialists – testers, developers, and programmers. Anyway, the decision to kill the Conti brand was right – to avoid repeating the fate of REvil group.
About Conti group
Conti ransomware group was one of the first “reborn” of an older ransomware group. Ryuk ransomware, which appeared in summer 2018, decided to stop roughly after two years of a successful activity that brought the group over 400 BTC. However, they were not aiming for a retirement – instead, they chose to rebrand. After a 3-month vacation in autumn 2020, they appeared under the name of the Conti group.
During the next 19 months of activity, Conti quickly reached the highest positions in ransomware ratings. Its competitors were very big names, such as REvil, LockBit, BlackMatter and DarkSide. Some of them are shut down at the moment. Some did the rebranding and are acting under a different name. However, they all never reached the same market share – at one moment, Conti accounted for almost 50% of all ransomware attacks against corporations.
Good start, bad final
It is obvious that such a great cybercriminal success is an object of interest for executive authorities. The latter was glad to meet any possible weakness, which happened at the beginning of the Russia-Ukraine war. Apparently, the group consisted of both Ukrainians and Russians – and after the war began, the group chiefs (likely Russians) claimed their full support of a “special military operation in Ukraine”. The Ukrainian part of the group decided to make grand mischief – by leaking the source codes of ransomware. That made it possible to use it not only for attacking russian companies – NB65 ransomware did it almost instantly after the leak, but also to trace the group’s chiefs. To avoid further deanonymization and capture, they decided to shut down their activity. And in the last few days, they removed the rest of their infrastructure from the Darknet page.
Will they come back? No one knows, but I am sure analysts will quickly uncover such a comeback. Conti had several unique features that make it possible to trace their software without a mistake. The rest of the group is located in Russia, and after the cease any cooperation with the USA in the cybersecurity space, this country is likely the safest place for cybercriminals. Unless they criticize Putin, of course. Still, there is an unanswered question – what can the victims do if they did not contact the crooks before they went offline? Other groups usually release the keys after claiming the shutdown. This one did not say a word.





I have been victim of ramsonware (in 2017) I get all my personal and work computer files encripted , all them with an added alfanumeric extension, probably the CRIPT ransomware. I have not find a decription service up to now to restore them. I have all those files stored and some of the also with the non-cripted version (obtained from a pen-drive not connected then). Please can you advice me how to obtain help ?