Experts report that the Conti ransomware is going out of business, group ceases operations, its infrastructure is disabled, and the group’s leaders have said the brand already does not exist.

One of the first to notice the change was Elisey Boguslavsky of Advanced Intel, who tweeted that the group’s internal infrastructure had been shut down. According to him, other internal services of the group, such as chat servers, are also being decommissioned.
Let me remind you that we wrote that Leaked Conti ransomware source codes were used to attack Russian authorities, as well as that Experts analyzed the conversations of Conti and Hive ransomware groups.
The publication Bleeping Computer writes that at the same time, the public site for leaks “Conti News”, as well as the site for negotiating ransoms, are still available, but Boguslavsky explained to reporters that the Tor administrative panels used by hackers to negotiate and publish news on the site are already disabled.
Although Conti recently carried out a high-profile attack on Costa Rica, Boguslavsky believes it was done as a distraction while Conti members slowly migrated to other, smaller extortion groups.
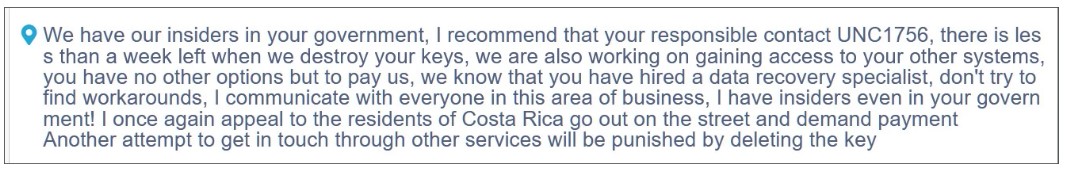
Conti threatens the government of Costa Rica
The secret purpose of the attack on Costa Rica, which was proclaimed by the internal leadership of Conti, was publicity, not ransom. Internal correspondence between members of the group indicates that the ransom requested was well under $1 million (despite rumors that the group was asking for a $10 million ransom and Conti’s own claims that the ransom was $20 million).say Advanced Intel experts.
Although the Conti brand no longer exists, experts are confident that this crime syndicate will play an important role in the extortion industry for a long time to come. So, Boguslavsky believes that instead of the traditional rebranding for hack groups (and the subsequent transformation into a new grouping), Conti’s leadership is collaborating with other smaller ransomware groups to carry out attacks.
As part of this “partnership”, small hack groups receive an influx of experienced pentesters, negotiators and operators from among Conti members. And the Conti syndicate, dividing into smaller “cells” controlled by a single leadership, gets mobility and the ability to evade the attention of law enforcement agencies.
According to the researchers, in this way Conti cooperates with groups HelloKitty, AvosLocker, Hive, BlackCat, BlackByte and so on. Also, Advanced Intel believes that members of Conti have created a number of new and autonomous groups that are completely focused on stealing data, not encrypting it. These groups include Karakurt, BlackByte and Bazarcall.