Ransomware is a malicious program which an attacker injects into your device to encrypt your data and hold your digital life hostage. Ryuk ransomware is similar to the typical ransomware but enhanced. It deliberately preys on high-profile targets capable of paying large amounts of money. Today we will learn what Ryuk ransomware is, how it came to be, how it spreads, and what the risks and consequences of encountering it are.
What is Ryuk Ransomware?
Ryuk ransomware is malware that hackers attack their targets with, infecting systems and encrypting data files. Then the malefactors keep the victim’s data inaccessible until a ransom is paid. The malware is named after the famous manga character from the movie Death Note, wherein “Ryuk” was the name of a god of death who killed victims selectively. The Ryuk ransomware virus attacked businesses, governments, and public institutions such as hospitals and schools. Ryuk, like any ransomware, can bring devastating consequences, especially for organizations with critical digital assets. It is especially true for hospitals that rely on electronic files to provide accurate medications or remotely managed energy or water facilities. When it comes to Ryuk attacks, vulnerable targets are never overlooked. Thus, cybercriminals have recently doubled their ruthless attacks.
Read Also: What is Ransom:Win32/Ryuk.AA infection? Ransom:Win32/Ryuk.AA distribution networks.
History of Ryuk Ransomware
Ryuk’s first appearance was in August 2018, when it encrypted files of hundreds of small municipalities, logistics companies, and technology firms worldwide. Although it was the first public appearance of the Ryuk ransomware virus, cybersecurity experts found a link between its code structures and a strain of the Hermes ransomware virus discovered earlier in 2017. Ryuk ransomware threat became especially alarming in 2021. A new variant with Internet-worm-like capabilities, which can spread between computers and systems without human involvement, has emerged. It accelerated the attack chain and made it easier for hackers to bring down entire networks.
Ryuk’s Spread Methods
Ryuk attacks most often begin with phishing emails. In addition, Ryuk attackers often conduct targeted phishing campaigns aiming at people with access to enterprise-level software or systems. They email victims with innocuous letters that have malicious links attached. Although the attachment may look like a Word document, it launches a Trojan malware (such as Trickbot or Emotet) when opened.
Read Also:Ransomware makes headlines almost daily. Important methods hackers use to infect you with ransomware to keep in mind.
Algorithm of Action
However, this initial malware is not ransomware. Instead, it is a tool that allows an attacker to take command and control of your machine so that they can later deploy a payload of ransomware. So, once the victim’s network is compromised, the attackers decide whether, in their opinion, it is worthwhile to further investigate and penetrate the network or not. If the attack is deemed lucrative enough and a large amount of money can be demanded as ransom, they will deploy the Ryuk ransomware. Once deep in the system, hackers stealthily collect administrator credentials and identify domain controllers. This allows a possible Ryuk ransomware to strike as hard as possible, providing maximum attack surface when the ransomware payload is finally released. Ryuk then encrypts computer files, data, and system access, making it impossible to retrieve information or access programs. It also disrupts the Windows system recovery function, forcing victims to choose between losing data or paying a ransom. This attack is so sudden and devastating that, in most cases, the victim prefers to expend, making this one of the most significant computer threats in recent memory. With Ryuk being a human-driven attack, the crooks behind it use manual hacking techniques to gain access and spread the pest across networks. This attack chain pattern was observed in 2018, 2019, and 2020.
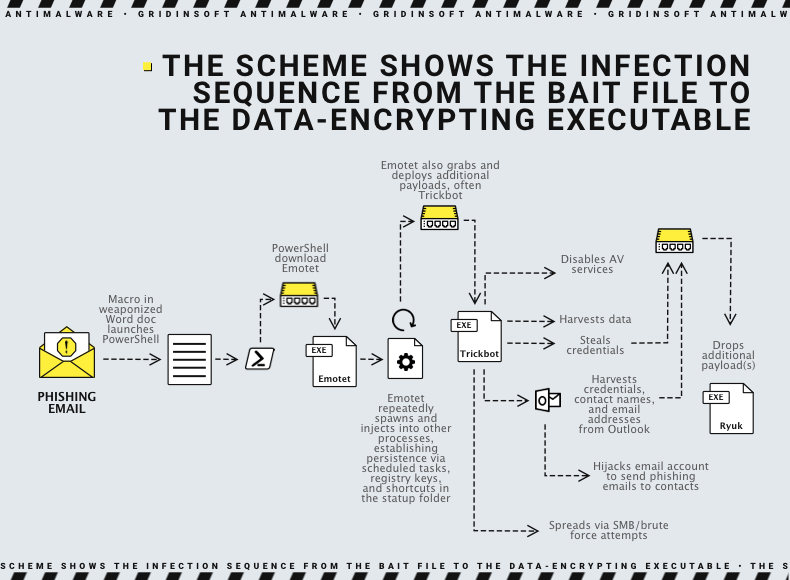
Studies of recent attacks show that the Ryuk ransomware has evolved and can now spread without human involvement, which is more typical for a worm rather than a computer virus. However, the initial data leak is associated with classic social engineering techniques such as phishing, spam, and spoofing.
Ryuk Encryption Routine
Once deployed, Ryuk encrypts all files except those with .dll, .lnk, .hrms, .login, .ini, and .exe extensions. However, it skips files stored in Windows System32, Chrome, Mozilla, Internet Explorer and Recycle Bin directories. These exclusion rules are probably made to keep the system stable and allow the victim to use the browser to make payments.
Ryuk uses strong AES-256-based file encryption. The encrypted files receive a different extension: .ryk. The AES keys are encrypted with a pair of RSA-4096 public and private keys, which are controlled by attackers. Generally, the whole process is a bit more complicated and involves several keys which are encrypted with other keys. As a result, each Ryuk executable is explicitly created for each particular victim, even if employed in several systems, using the generated private key for that individual victim. Thus, even if the RSA private key associated with one victim is revealed and published, it cannot decrypt files belonging to other victims.
Currently, no publicly available tools can decrypt Ryuk files without the ransom paid, and researchers warn that even the decryption tool provided to victims by Ryuk attackers can sometimes corrupt files. This usually happens with large files, where Ryuk intentionally performs only partial encryption to save time. Also, some system files and directories that are whitelisted can still be encrypted by Ryuk, which sometimes results in the inability to boot the system after restarting it. All of these problems can make recovery more difficult and increase costs to victims due to Ryuk attacks. Like most ransomware, Ryuk attempts to delete shadow copies of volumes to prevent data recovery by alternative means. It also contains a kill.bat script that disables various services, including network backup and Windows Defender antivirus.
Examples of Ryuk Ransomware Attacks
Ryuk ransomware attacks follow a similar pattern. Large public or private organizations are targeted, and the hackers launch raid-like offenses. Ryuk attacks have targeted organizations in the United States, the United Kingdom, Germany, Spain, France, and Australia. In early 2021, an analysis of bitcoin transactions from known Ryuk addresses revealed that Ryuk hackers fraudulently obtained more than $150 million in ransomware. The most notable Ryuk ransomware attacks have hit municipalities, school systems, technology and energy companies, and hospitals. Here are the most famous attacks:
- October 2018: Ryuk attacked major Onslow Water and Sewer Authority (OWASA) organizations, disrupting their network.
- December 2018: Tribune Publishing was attacked, affecting its clients like the Los Angeles Times.
- 2019-2020: Ryuk targeted some hospitals in California, New York, and Oregon. It also targeted British and German medical facilities, causing problems accessing patient records and affecting critical care.
Over a dozen hospitals were affected by ransomware attacks in late 2020. In June 2019, Lake City, Florida, paid a $460,000 ransom after an employee had opened an infected email.
How to Remove Ryuk Ransomware?
Because of Ryuk’s complexity, only experienced IT teams should remove it. However, your files will still be encrypted even after Ryuk is removed from your network since only the attackers have the keys to restore assets. You can remove Ryuk in safe mode or through system restore. However, the focus should be on preventing such attacks before losing access to critical assets. Every employee should keep a close eye out for phishing emails. Don’t click on any suspicious content in your inbox.
Most importantly, organizations should establish the proper cybersecurity protocol, strategy, and training program. An AI-based endpoint protection platform that detects and prevents threats is essential to protect your enterprise from attacks. Advanced cybersecurity software can rank and triage threats based on in-depth knowledge of your environment and can conduct thorough investigations to recognize ever-evolving malware.
Related Content: In most cases, Ransom:Win64/Ryuk.A ransomware will certainly instruct its targets to initiate a funds transfer to counter the changes that the Trojan infection actually made to the target’s tool.
Protecting Against Ryuk
While organizations can apply specific technical controls to reduce the likelihood of Ryuk infections, defending against ransomware attacks managed by people generally requires correcting some misconduct among workgroup administrators.
“Some of the most successful human-driven ransomware campaigns have targeted servers that have deliberately disabled antivirus software and other security controls that administrators can do to improve performance,” Microsoft said. “Many of the observed attacks use malware and tools that are already recognized by antivirus programs. The same servers often lack firewall and MFA protection, have weak domain credentials, and use non-random local administrator passwords. Often these protections are intentionally disabled because there is a concern that security controls may negatively impact performance. IT-team can help determine the true impact of these settings and work with security teams to mitigate the effect. Attackers use settings and configurations that IT administrators manage and monitor.
Security services also need to take what appear to be rare infections or common malware more seriously. As Ryuk shows, common threats like Emotet and TrickBot rarely appear on their own and can be a lousy wake-up call for much more severe problems. Simply removing common malware from a system without further investigation can lead to disastrous consequences weeks or months later.
“Infections with commodity malware such as Emotet, Dridex, and Trickbot must be removed and treated as a potential complete compromise of the system, including any credentials present,” Microsoft warned.
Addressing the infrastructure weaknesses that allowed malware to get in and spread is just as critical as protecting the network from lateral movement by maintaining proper credential hygiene and providing access with minimal privileges. In addition, limiting unnecessary SMB (Server Message Block) traffic between endpoints and restricting the use of administrator credentials can positively impact network resilience against human-led attack campaigns.




