A new 0-day Windows Search vulnerability could be used to automatically open a search box and launch remote malware, which is easily done by simply opening a Word document.
Bleeping Computer says the problem is serious because Windows supports the search-ms protocol URI handler, which allows apps and HTML links to run custom searches on the device. And while most searches will search on the local device, it’s also possible to force Windows Search to query file shares on remote hosts and use a custom title for the search box.
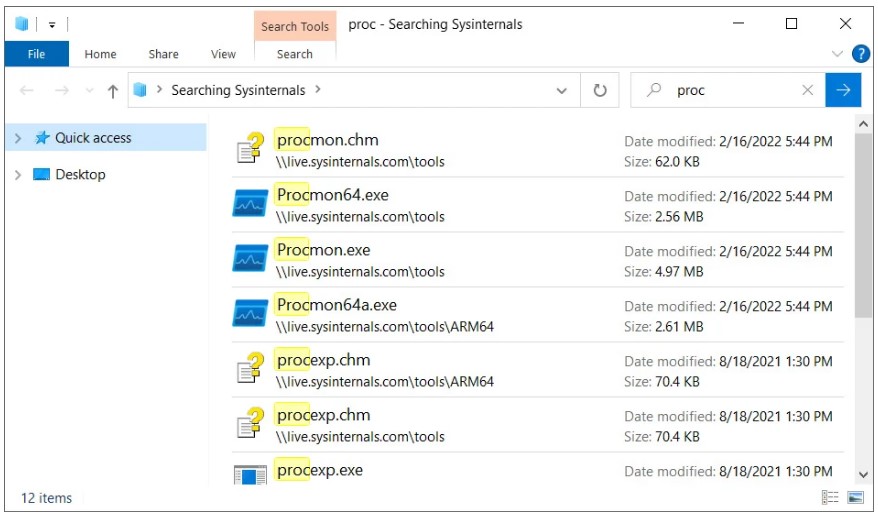
For example, Sysinternals allows remotely mounting live.sysinternals.com as a network share to run its utilities. Users can use the following search-ms URI to find this remote share and display only files that match a specific name: search-ms:query=proc&crumb=location:%5C%5Clive.sysinternals.com&displayname=Searching%20Sysinternals
In this case, the crumb search-ms variable specifies the search location, and the displayname variable specifies the title. When executing this command from the Run dialog box or the browser address bar in Windows 7, Windows 10 and Windows 11, a custom search box will appear, as in the screenshot below. The header says “Searching Sysinternals” as specified in the search-ms URI.
Hackers can use the same approach for attacks, where phishing emails masquerade as updates or patches that supposedly need to be installed urgently. Attackers can set up a remote Windows share that will be used to host malware disguised as security updates, and then use the search-ms URI in their attacks.
It would seem difficult to get the user to click on such a URL, especially given the warning that will be displayed in this case.
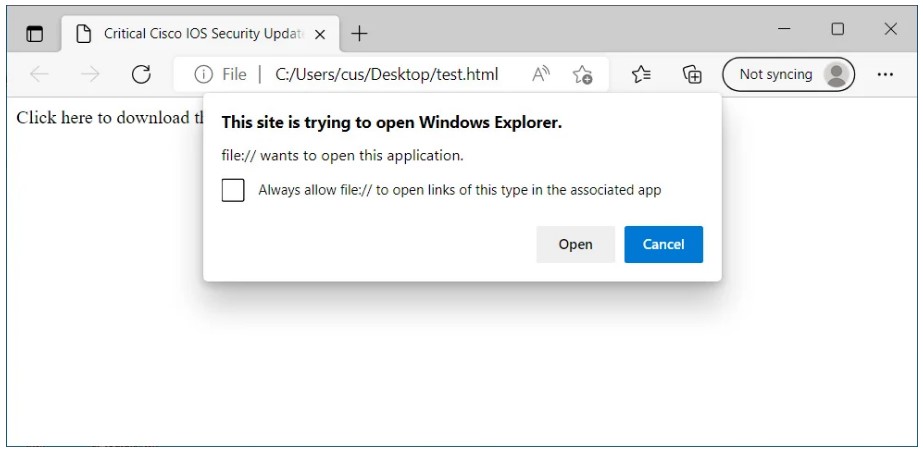
However, Hacker House co-founder and security researcher Matthew Hickey has found a way to combine a newly discovered vulnerability in Microsoft Office with a search-ms handler to open a remote search window by simply opening a Word document.
Let me remind you that the discovery of 0-day Follina became known just a few days ago, although researchers first found this bug back in April 2022, but then Microsoft refused to acknowledge the problem. The vulnerability is now tracked as CVE-2022-30190 and is known to be exploitable through normal Word document opening or File Explorer preview, using malicious PowerShell commands through the Microsoft Diagnostic Tool (MSDT) to execute.
The bug affects all versions of Windows that receive security updates, including Windows 7 and later, as well as Server 2008 and later.

CVE-2022-30190 is known to allow Microsoft Office documents to be modified to bypass Protected View and run URI handlers without user interaction, which can lead to further handler abuse. Hickey discovered yesterday that it is possible to modify existing exploits for Microsoft Word MSDT to abuse search-ms instead.
The new PoC automatically runs the search-ms command when the user opens a Word document. The exploit opens a Windows Search window that lists executable files on a remote SMB share. This shared folder can be named whatever the hacker wants, such as “Critical Updates”, and will prompt users to install the malware under the guise of a patch.
As with the MSDT exploits, Hickey demonstrated that it was possible to create an RTF that would automatically open a Windows Search window while still previewing in Explorer.
Bleeping Computer journalists note that events is the reminiscence of the situation with the PrintNightmare RCE vulnerability discovered and fixed in Print Spooler in 2021. At that time, Microsoft quickly fixed the original bug, but its discovery led to many other local privilege escalation vulnerabilities related to the original problem. Then Microsoft developers were forced to make radical changes to Windows Printing in order to finally get rid of this class of vulnerabilities as a whole.
Now Microsoft will probably have to make it impossible to run URI handlers in Microsoft Office without user interaction. Until that happens, there will be regular reports of new exploits being created.