Security researchers recently discovered a zero-day vulnerability in Microsoft Office dubbed Follina. The bug can be exploited through the normal opening of a Word document, using it to execute malicious PowerShell commands through the Microsoft Diagnostic Tool (MSDT).
Let me remind you that we also wrote that Lapsus$ hack group stole the source codes of Microsoft products, and also that Microsoft Has Not Fully Coped with PetitPotam Attacks in Windows NTLM Relay.
The discovery of Follina is a very worrying sign, as the vulnerability opens up a new attack vector using Microsoft Office. The fact is that the bug works without elevated privileges, allowing to bypass Windows Defender and does not require the activation of macros to execute binaries or scripts.
The first malicious Word document intended to exploit this bug was discovered by the information security specialist nao_sec, who spotted a file on VirusTotal downloaded from a Belarusian IP address. Apparently, attacks on this problem began as early as April 2022, and hackers used fake interview invitations and sexual extortion as baits for their victims.
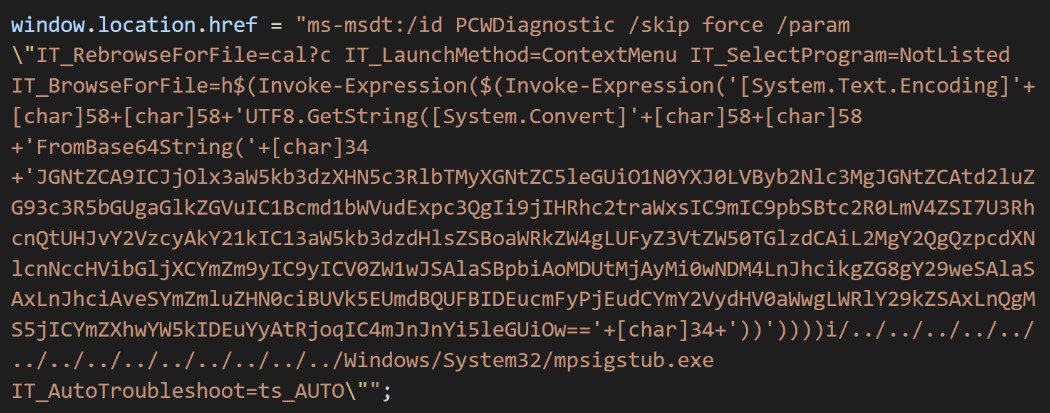

Well-known information security expert Kevin Beaumont studied the find of his colleague, deciphered the code and explained in his blog that this is a command line string that Microsoft Word executes using MSDT, even if macros are disabled. Beaumont elaborates that a malicious Word document uses a remote template feature to download an HTML file from a server. This HTML then uses the Microsoft MS-MSDT URI scheme to load additional code and execute the PowerShell code.
It is noted that this activates the Protected View feature in Microsoft Office, designed to warn about files from potentially unsafe sources, but, according to Beaumont, this warning can be bypassed by using a Rich Text Format (RTF) file. Thus, malicious code can work “even without opening the document, that is, through the preview in Explorer.”
According to Bleeping Computer, many information security specialists have already studied the found malicious document and successfully reproduced the exploit on several versions of Microsoft Office. As a result, the researchers confirmed the presence of a vulnerability in Office 2013, 2016, Office Pro Plus April version (Windows 11 with May updates) and Office 2021 version with all patches.
According to experts, an attacker can use such an exploit to access various places on the victim’s network. Depending on the payload, the attacker can collect password hashes from the victim’s Windows machines, which can be useful for further post-exploitation.
A detailed technical description of the exploit is already available on the Huntress blog.
Interestingly, it now turns out that the Follina vulnerability was discovered back in April of this year, and Microsoft has already been notified about it.
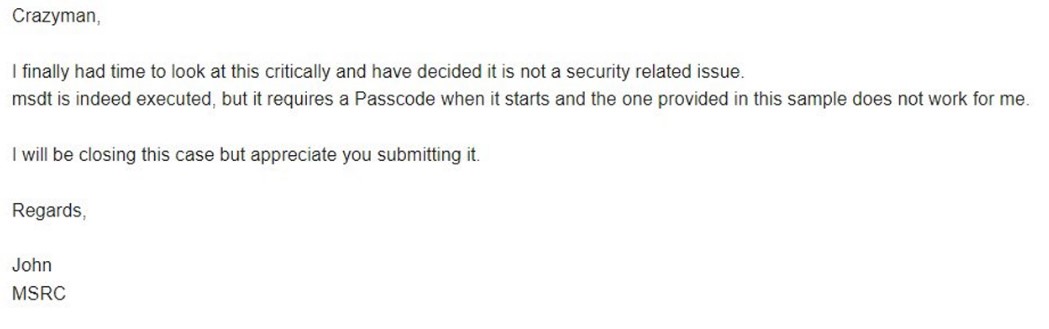
So, according to screenshots posted by crazyman, a member of the Shadow Chaser Group (an association of college students engaged in the search and analysis of APT), Microsoft was informed about the vulnerability, but the company considered it to be “a non-security issue.” Microsoft argued that msdt.exe was indeed running, but it required a password to run, and the company was unable to reproduce the exploit.
Now Microsoft has acknowledged that the problem is still related to security: the vulnerability has already received the identifier CVE-2022-30190, and it is reported that the bug affects all versions of Windows that receive security updates, that is, Windows 7 and newer, as well as Server 2008 and newer.
Since there is no patch yet, administrators and users can block attacks on CVE-2022-30190 by disabling the MSDT URI protocol, which attackers use to launch debuggers and execute code on vulnerable systems.
Although Microsoft Defender version 1.367.719.0 is already able to detect the use of a vulnerability by signatures, and Protected View and Application Guard in Microsoft Office should block attacks, security experts warn that protective functions are powerless if the attack is carried out through a preview in Explorer, and not through opening a document. Therefore, it is also recommended to disable the preview in Windows Explorer.




