Threat actors reportedly started using fake TeamViewer to distribute malware. Their particular favourite for the final payload is the infamous njRAT trojan – an old-timer of the scene. Through the tricky spreading scheme, hackers run a multi-stage attack.
njRAT Hides in Trojanized TeamViewer App
For some reason, people show high levels of trust towards downloading links they’re given on various forums or other thematic communities. This is where the major share of trojanized installers are spread. Cybercriminals, or even users they pay for spreading offer this installer as a “hacked full version” of the well-known remote access tool. As it allows for some functions absent in a free version, and folks are exceptionally eager for any free stuff, they inevitably stick to this crack. And, as it often happens, using the crack ends up with some really bad things.
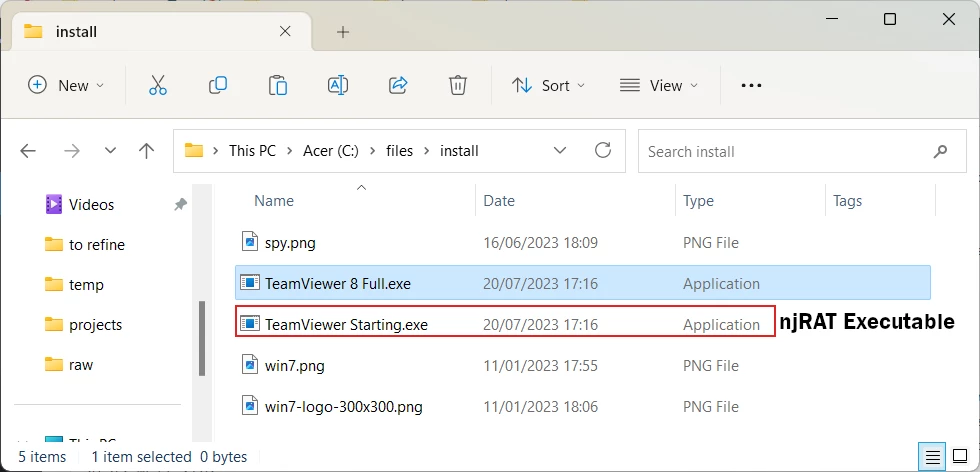
The installer I am talking about looks like a legit thing – neither its name, nor the size calls any suspicion. However, upon execution, it drops two files: the legitimate TeamViewer app installer and an item called “TeamViewer Starting.exe”. This, exactly, is a payload, specifically njRAT – an infamous remote-access trojan from 2013. Then the forged installer runs a legit TeamViewer app, to make the victim think everything is OK.
What is njRAT?
njRAT, also known under the name of Bladabindi, is an old-timer of the malware scene. It appeared almost a decade ago, while some analysts trace it even further in the past – to 2012. Such a long life is already a mark of success, and there are a couple of things going for it.
Being a classic remote access trojan, njRAT manages to conjoin the functionality of a stealer with the one of a backdoor. It grants its masters access to the infected system, which is already beneficial. Commanding to send requests to a target server, using the machine as a dummy for malicious operations, rummaging through the files in a manual mode – cybercriminals are ready to pay for that. And with an extensive botnet, you can do nothing but count money for leasing it to other crooks.
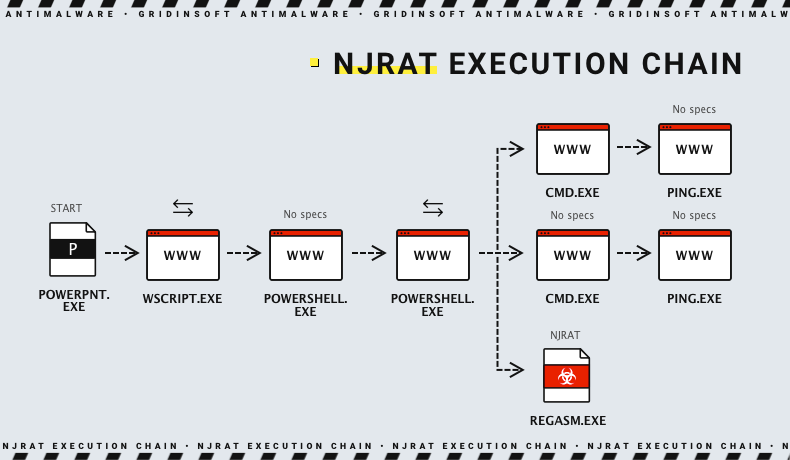
Though that is only one side of njRAT dirty deeds. As I said, it can act as an infostealer, grabbing passwords and logging keystrokes. It particularly targets cryptocurrency wallets, both desktop and ones present as browser add-ons. This appears to be a modern trend – and it would be shortsightedly to ignore it. Stealers that started in 2018 adopted this feature in progress, and njRAT did so as well.
One more thing this malware is distinctive for is detection evasion methods. Aside from heavy obfuscation that is a must-have in modern malware, it also employs hooking itself to critical system processes. This prevents users – and some antiviruses – from stopping the process. Moreover, it seriously disguises the malware, as it hides among system processes rather than user ones in the Task Manager.
How to protect your system in such situations?
Well, there is one major thing that makes this malware spreading campaign happen is users’ trust towards software advised on third-party websites and overall – software cracks. If you would not stick to downloading TeamViewer from warez sites and forums, you would not face njRAT running in your system – that’s plain and simple. Though, there are several other tips that will help you to prevent any infections, regardless of their source.
Use a great anti-malware program. To be sure it will protect you from the trickiest malware samples, choose one with a heuristic system. It allows for detecting threats by their behaviour, thus any obfuscations or mimicking the system processes are useless. GridinSoft Anti-Malware is one that can offer such a feature – consider trying it out.
Use licensed software. Trojanized TeamViewer is just one example of possible malware injection into the programs you get from unofficial sources. Paying for a licence is always less expensive and unpleasant than sorting out the consequences of spyware/backdoor activity. If there is no way to get the program from an official source (a common situation with abandonware) be sure to scan it with anti-malware software before launching.
Keep an eye on cybersecurity news. This is cherry-on-top advice, that does not change much, but will surely help you to know where the traps are. Malicious Google ads, fake installers, email spam campaigns that convincingly mimic legit mailings – awareness sometimes can save you better than any reactive measures.





