Researchers from Imperva have found that the KashmirBlack botnet, active since the end of 2019, is behind attacks on hundreds of thousands of websites powered by popular CMS, including WordPress, Joomla, PrestaShop, Magneto, Drupal, vBulletin, osCommerce, OpenCart and Yeager.
As a rule, a botnet uses the servers of infected resources to mine cryptocurrency, redirects legitimate traffic to spam sites, uses hacked sites to attack other resources and maintain its activity, and sometimes even arranges defaces.
Thus, the researchers argue that KashmirBlack is currently operated by one C&C server, but uses more than 60 servers (mostly compromised resources) in its infrastructure.
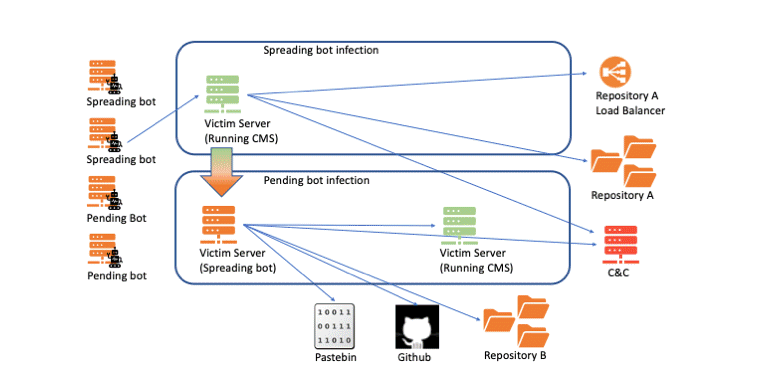
The main distribution method for KashmirBlack is to scan the Internet in search of sites that are running outdated software. The malware then uses exploits for various known vulnerabilities to hack the vulnerable site and take over its server. According to Imperva, the botnet actively abuses 16 vulnerabilities:
- remote execution of PHPUnit code (CVE-2017-9841);
- jQuery file upload vulnerability (CVE-2018-9206);
- ELFinder command injection (CVE-2019-9194);
- remote file upload vulnerability in Joomla;
- Magento Local File Inclusion (CVE-2015-2067);
- Magento web form loading vulnerability;
- the problem of loading an arbitrary file into the CMS Plupload;
- vulnerability in Yeager CMS (CVE-2015-7571);
- multiple vulnerabilities including file upload and RCE in many plugins for different platforms;
- WordPress TimThumb RFI vulnerability (CVE-2011-4106);
- Uploadify RCE vulnerability
- RCE vulnerability in vBulletin widget (CVE-2019-16759);
- RCE vulnerability in WordPress install.php;
- brute force attack on WordPress xmlrpc.php;
- RCE in a number of WordPress plugins (full list here);
- RCE in a number of WordPress themes (full list here);
- file upload vulnerability in Webdav.
Imperva researchers note that, in their opinion, this botnet is the work of a hacker known under the pseudonym Exect1337, participant of the Indonesian hacker group PhantomGhost.
Let me remind you about the most aggressive botnets: for example, IPStorm botnet, that attacks Android, macOS and Linux devices, and Dracula propaganda botnet.




