Microsoft has shared a guide to help organizations detect the installation of the BlackLotus UEFI bootkit that exploits the CVE-2022-21894 vulnerability. The company also explained how best to restore an infected system.
Let me remind you that we also wrote that Experts discovered ESPecter UEFI bootkit used for espionage.
Let me remind you that BlackLotus was first seen in October 2022. Its seller claimed that the bootkit had a built-in Secure Boot bypass, built-in Ring0/Kernel deletion protection, and also ran in recovery mode and safe mode.
It was reported that the malware is equipped with anti-virtualization, anti-debugging and obfuscation, which complicates its detection and analysis. Also, according to the seller, the security software cannot detect and destroy the bootkit, since it runs under the SYSTEM account inside a legitimate process.
In addition, BlackLotus is able to disable security mechanisms on target machines, including Hypervisor-Protected Code Integrity (HVCI) and Windows Defender, as well as bypass User Account Control (UAC).
Black Lotus has a size of 80 kilobytes, is written in assembler and C, and can determine the geofence of the victim in order to avoid infecting machines in the CIS countries. Last year, the malware was offered for sale for $5,000, with each new version priced at another $200.
Later, the threat was studied by analysts from ESET. They confirmed that the bootkit easily bypasses Secure Boot and uses the CVE-2022-21894 vulnerability from a year ago to gain a foothold in the system.
It was highlighted that Microsoft fixed this issue back in January 2022, but attackers can still exploit it because the affected signed binaries were not added to the UEFI revocation list. According to analysts, BlackLotus is the first documented case of abuse of this vulnerability.
As Microsoft experts now say, during the analysis of devices compromised with BlackLotus, they identified a number of features that make it possible to detect infection. The researchers say defenders may be looking for signs of a BlackLotus installation in the following locations:
- newly created and locked bootloader files;
- the presence of an intermediate directory used during the installation of BlackLotus, in the EFI System Partition (ESP);
- changing the Hypervisor-protected Code Integrity (HVCI) registry key;
- online magazines;
- boot configuration logs.
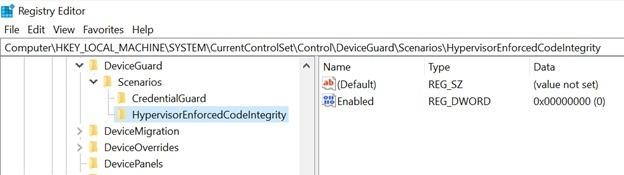
Registry changes
Analysts write that BlackLotus blocks files it writes to EFI (ESP), making them inaccessible. However, their names, creation time, and error messages received when trying to access them should indicate the presence of a bootkit, as well as the presence of a custom directory (/system32/) created and not deleted during installation.
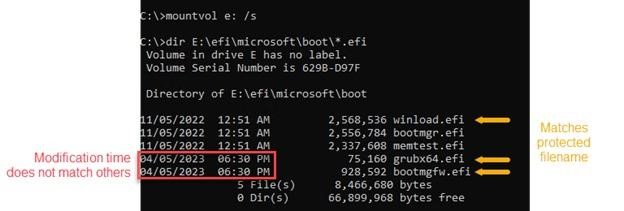
Timestamps for BlackLotus Boot Files
Defenders can also detect bootkit-related registry changes, log entries created when BlackLotus disables Microsoft Defender or adds components to the boot loop, and winlogon.exe’s persistent outgoing network connection on port 80, which also indicates an infection.
To clean up a machine previously infected with BlackLotus, experts recommend isolating it from the network, reformatting and installing a clean OS with an EFI partition, or restoring the system from a clean backup with an EFI partition.
To avoid being infected by BlackLotus or other malware that exploits the CVE-2022-21894 vulnerability, Microsoft recommends that organizations be mindful of the principle of least privilege and maintain credential hygiene.