ESET experts reported that the BlackLotus UEFI bootkit, which is sold on hacker forums for about $ 5,000, is indeed capable of bypassing Secure Boot protection.
According to researchers, the malware poses a threat even to fully updated machines running Windows 11 with UEFI Secure Boot enabled.
Let me remind you that we also wrote that Experts discovered ESPecter UEFI bootkit used for espionage, and also that The expert told how he hacked into a nuclear power plant.
BlackLotus was first spotted in October 2022. Its seller claimed that the bootkit had a built-in Secure Boot bypass, built-in Ring0/Kernel deletion protection, and also ran in recovery mode and safe mode.
In addition, the seller claimed that the malware is equipped with anti-virtualization, anti-debugging and obfuscation, which complicates its detection and analysis. Also, according to his statements, the security software cannot detect and destroy the bootkit, since it runs under the SYSTEM account inside a legitimate process.
In addition, Black Lotus is allegedly capable of disabling security mechanisms on target machines, including Hypervisor-Protected Code Integrity (HVCI) and Windows Defender, as well as bypassing User Account Control (UAC).
The experts who discovered it wrote that Black Lotus has a size of 80 kilobytes, is written in assembler and C, and can determine the geofence of the victim in order to avoid infecting machines in the CIS countries. The malware is offered for sale for $5,000, and each new version will cost another $200.
Let me remind you that at that time the experts admitted that all the above features of Black Lotus are nothing more than a publicity stunt, and in reality the bootkit is far from being so dangerous. Unfortunately, these assumptions were not confirmed.
As ESET information security experts, who have been studying the malware since last fall, now report, rumors that the bootkit easily bypasses Secure Boot “have now become a reality”. According to them, the malware uses a year-old vulnerability CVE-2022-21894 to bypass Secure Boot and gain a foothold in the system.
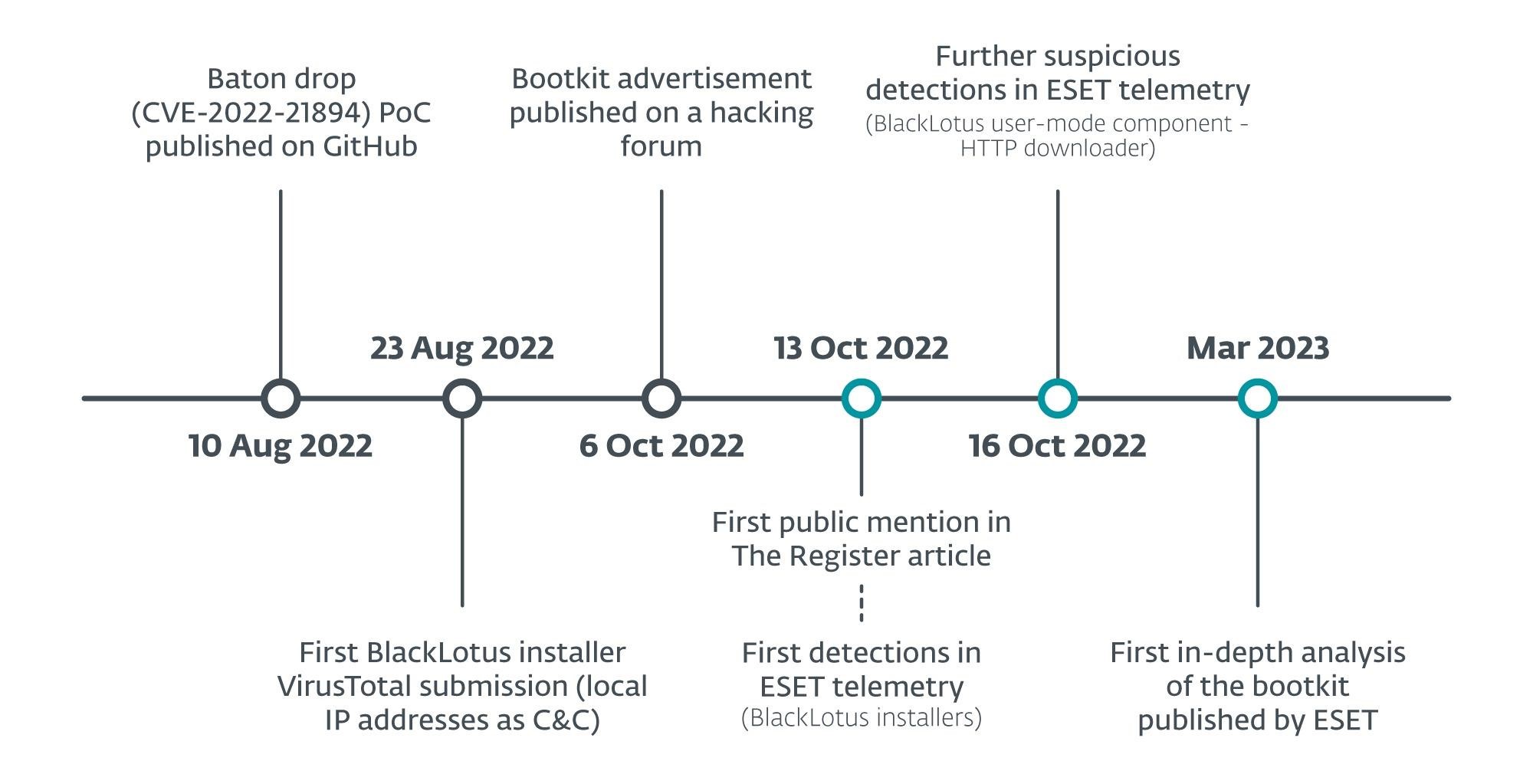
Chronology from vulnerability to bootkit
Microsoft fixed this issue back in January 2022, but attackers can still exploit it because the affected signed binaries were not added to the UEFI revocation list. According to analysts, this is the first documented case of abuse of this vulnerability.
Most likely, information security specialists mean attacks like BYOVD – bring your own vulnerable driver.
Even worse, the PoC exploit for this vulnerability has been available since August 2022, so other cybercriminals may soon take advantage of the problem.
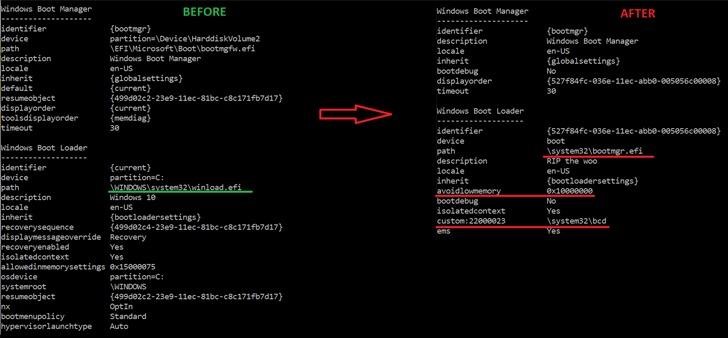
The exact way the bootkit is deployed is still unclear, but the attack begins with the installer component, which is responsible for writing files to the EFI system partition, disabling HVCI and BitLocker, and then rebooting the host.
The researchers say that after exploiting CVE-2022-21894, Black Lotus disables protection mechanisms, deploys a kernel driver and an HTTP loader. The kernel driver, among other things, protects the bootkit files from deletion, while the bootloader communicates with the control server and executes the payload.
While the researchers do not link the malware to any particular hack group or government, they note that the Black Lotus installers they analyzed will not work if the infected computer is located in Armenia, Belarus, Kazakhstan, Moldova, Romania, Russia, and Ukraine.