Researchers at Huntress Labs estimate that over the past few days, about 2,000 Microsoft Exchange mail servers have been compromised and infected with backdoors, because their owners have not installed patches to fix ProxyShell vulnerabilities.
Let me remind you that the vulnerabilities, which were collectively called ProxyShell, were discussed at the Black Hat conference in early August. ProxyShell combines three vulnerabilities that allow remote code execution without authentication on Microsoft Exchange servers.
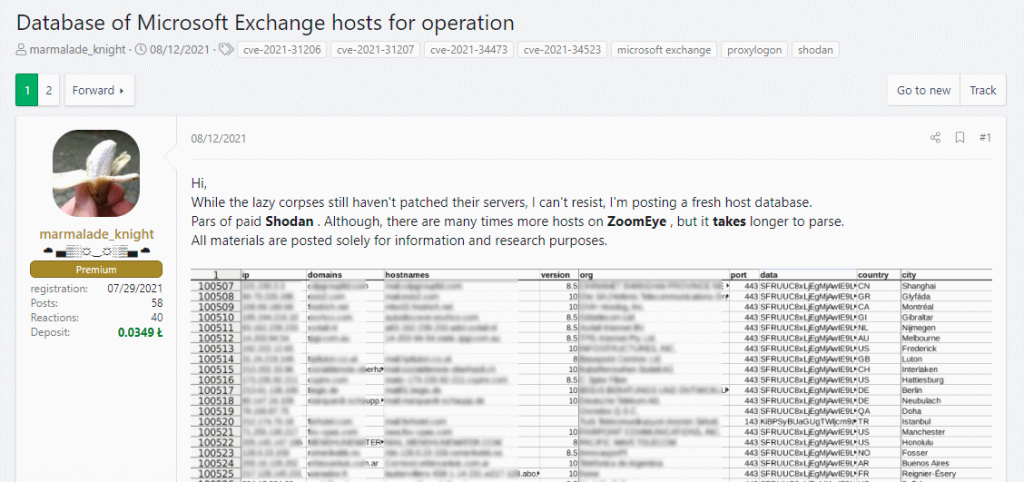
Microsoft Exchange Client Access Service (CAS) exploits these vulnerabilities running on port 443.
- CVE-2021-34473: Path Confusion without authentication leading to ACL bypass (fixed in April in KB5001779);
- CVE-2021-34523: Privilege Escalation in Exchange PowerShell Backend (fixed in April in KB5001779);
- CVE-2021-31207: Writing arbitrary files after authentication, leading to remote code execution (fixed in May in KB5003435).
An exploit for ProxyShell was used during the Pwn2Own 2021 hacker contest in April this year, and then the successful compromise of the server brought the researchers $200,000.
Although Microsoft patched the vulnerabilities, not all administrators installed these patches on time.
For example, a scan conducted on August 8 by ISC SANS (two days after the publication of the PoC exploit) showed that more than 30,400 Exchange servers are still vulnerable to attacks. Moreover, a list of all 100,000 Exchange servers accessible via the Internet was soon published on a well-known hacker forum, which further simplified the task for cybercriminals.
Researchers have already warned that scans have begun in search of vulnerable servers and attempts to hack them. In the past week, these attacks have become more frequent, and the LockFile ransomware was noticed, which has already started using a ProxyShell exploit to penetrate corporate networks.
Huntress Labs researchers who studied Microsoft Exchange servers that were compromised with ProxyShell now report that they have found more than 140 different web shells on more than 1,900 compromised Exchange servers.
Let me remind you that I also wrote that US and UK accused China for attacks on Microsoft Exchange servers.