Trend Micro has published a list of the top threats and most attacked vulnerabilities for Linux in the first half of 2021.
The results were obtained from honeypots, sensors and anonymous telemetry.
Linux is considered by many to be a unique operating system because of its stability, flexibility and open-source code. Its reputation is underpinned by numerous notable achievements in recent years. Linux is powerful, versatile, and reliable, but it is not without its drawbacks; like other operating systems, it is still vulnerable to attacks.Trend Micro says.
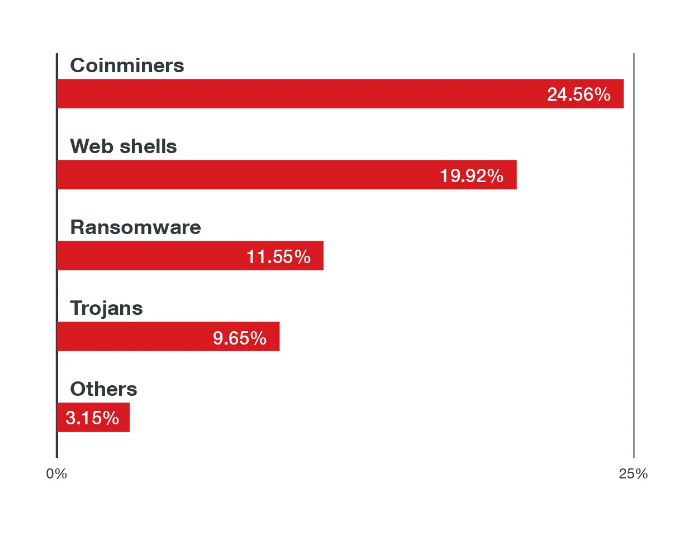
In total, the company recorded about 15,000,000 malicious events targeting Linux-based cloud environments and estimates that miners and ransomware account for 54% of all malware, with web shells accounting for another 29%.
In addition, after analyzing over 50,000,000 events from 100,000 unique Linux hosts over the same time period, the researchers identified 15 different vulnerabilities that are commonly used for attacks and have public exploits:
- CVE-2017-5638 (CVSS: 10.0) – Remote Code Execution (RCE) vulnerability in Apache Struts 2.
- CVE-2017-9805 (CVSS: 8,1) – REST plugin vulnerability for Apache Struts 2, XStream RCE;
- CVE-2018-7600 (CVSS: 9.8) – RCE vulnerability in Drupal Core;
- CVE-2020-14750 (CVSS: 9.8) – Oracle WebLogic Server RCE vulnerability;
- CVE-2020-25213 (CVSS: 10.0) – RCE vulnerability in WordPress File Manager plugin (wp-file-manager);
- CVE-2020-17496 (CVSS: 9.8) – RCE vulnerability in vBulletin ‘subwidgetConfig’;
- CVE-2020-11651 (CVSS: 9.8) – SaltStack Salt authorization vulnerability;
- CVE-2017-12611 (CVSS: 9.8) – RCE vulnerability in -Apache Struts OGNL;
- CVE-2017-7657 (CVSS: 9.8) – Integer overflow in Eclipse Jetty.
- CVE-2021-29441 (CVSS: 9.8) – bypass authentication in Alibaba Nacos AuthFilter;
- CVE-2020-14179 (CVSS: 5.3) Atlassian Jira Disclosure
- CVE-2013-4547 (CVSS: 8.0) – Bypassing Access Restrictions in Nginx;
- CVE-2019-0230 (CVSS: 9.8) – RCE vulnerability in Apache Struts 2;
- CVE-2018-11776 (CVSS: 8,1) – RCE vulnerability in Apache Struts OGNL;
- CVE-2020-7961 (CVSS: 9.8) – Liferay Portal Untrusted Deserialization Vulnerability.
Let me remind you that I talked about New vulnerabilities that help to bypass protection from Specter on Linux systems.




