ESET experts discovered the previously unknown ESPecter UEFI bootkit, which was used for targeted attacks and espionage. So far, experts do not associate ESPecter with any specific hack groups or countries.
UEFI attacks are the holy grail for hackers. After all, UEFI is loaded before the operating system and controls all processes at an “early start”. Hence the main danger associated with compromising this environment: if you make changes to the UEFI code, you can take complete control of the computer. For example, change memory or disk contents, or force the operating system to run a malicious file. Since we are talking about low-level malware, it will not work to get rid of it by replacing the hard drive or reinstalling the OS.
The first bootkit for UEFI, LoJax, was discovered by ESET in 2018. Then the researchers concluded that it was the work of the Russian-speaking “government” hack group Fancy Bear.
Since then, UEFI bootkits have been found more than once, and the last such case was described last week: Kaspersky Lab experts spoke about the tools of the Chinese cyber-espionage group GhostEmperor.
Now the list of UEFI bootkits has been replenished with one more item, the ESPecter malware. ESET experts say that the first attacks using this malware were discovered back in 2012. However, then ESPecter was not used as a bootkit for UEFI, its original purpose was to attack systems with BIOS. Only in 2020 did the malware authors update the code and switched to attacks on UEFI.
Researchers still do not know exactly how the attacks of these unknown attackers begin. It is unclear if they are gaining physical access to the target systems or whether they are using classic phishing to deploy ESPecter on the victim’s network.
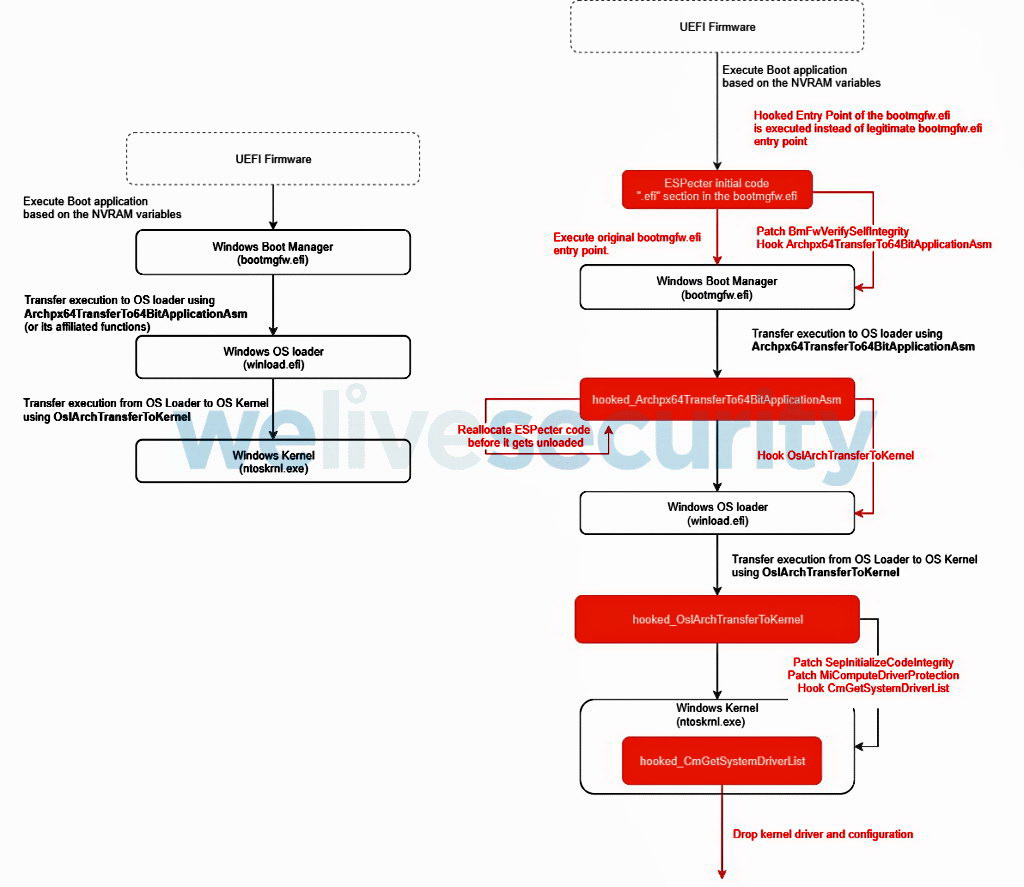
However, once the installation process begins, the initial ESPecter components are known to modify the Windows Boot Manager and bypass the Windows Driver Signature Enforcement (DSE) to load and run an unsigned malicious driver – the actual payload of the ESPecter bootkit.
It is reported that hackers usually use ESPecter to deploy other malware and try to gain a foothold in the system in order to “survive” reinstallation of the OS. The malware detected in such attacks includes a backdoor Trojan that cybercriminals used to search for confidential files on the local system, periodically create screenshots and launch a keylogger.
ESET analysts point out that ESPecter is the second known UEFI bootkit that uses EFI System Partition (ESP) as its entry point. The first malware of this kind was a bootkit recently discovered by Kaspersky Lab, which is part of the FinSpy toolkit. The point is, other UEFI bootkits usually use UEFI SPI flash memory.
Let me remind you that we also told that The expert told how he hacked into a nuclear power plant.