In recent years, zero-day exploits and attacks have become prominent emerging threats. These attacks take advantage of unknown vulnerabilities within software, which makes them almost impossible to detect and prevent. Zero-day attacks can have dire consequences, allowing attackers to take control of systems, steal data, or install malware.
What is a Zero-Day attack?
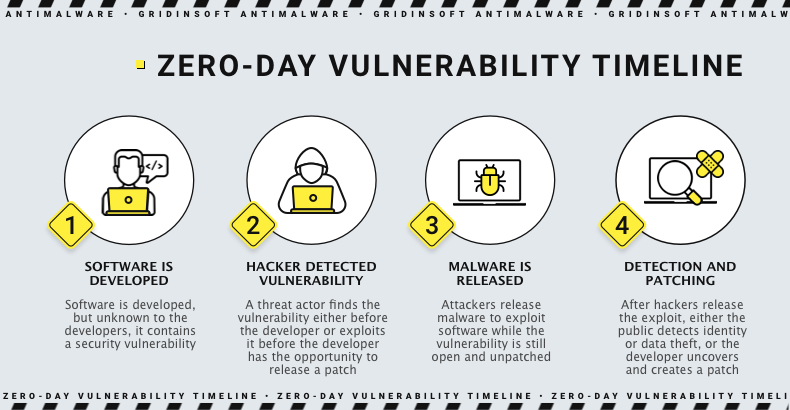
A zero-day attack is a type of vulnerability that has not been detected yet. It can be used for malware deployment and can target any application as a potential attack surface. This makes it difficult to build a trusted lineup of any sort and poses a significant challenge for cybersecurity analysts. However, for those who work in this industry, the challenge is exciting.
Attackers can exploit the undeclared function in a program or operating system to execute their code more beneficially. The most commonly used exploits by cybercriminals are those that provide remote code execution and escalation of privileges, which allow them to do whatever they want in the infected environment. As these attacks require advanced software, they are usually targeted against corporations since they possess more valuable data.
As the only person who knows about the breach is the criminal who discovered it, exploiting it without triggering any alarms or drawing attention is quite simple. Even some EDR solutions can make mistakes by overlooking actions from trusted programs without considering that such activities could be malicious. That’s why using an endpoint protection application that can prevent zero-day attacks is advisable.
Identifying and Addressing Zero-Day Exploits and Attacks
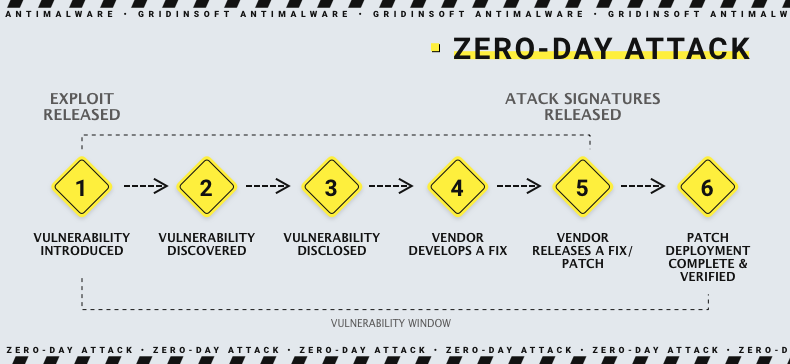
Detecting and mitigating zero-day exploits and attacks can be challenging since there are no known vulnerabilities or signatures to identify them. Nevertheless, there are strategies that can be utilized to identify and eliminate these attacks.
- Monitor network traffic and system logs to identify any suspicious activity that could indicate a zero-day attack.
- Educate users on common attack methods, such as phishing and social engineering, to reduce the likelihood of a successful zero-day attack.
- Stay updated with software, system updates, and patches to minimize vulnerabilities that could be exploited in a zero-day attack.
- Implement intrusion detection and prevention systems to help detect and block zero-day exploits and attacks before they can cause damage.
Patches May Be Ineffective, Here Is Why
Organizations have been struggling with patch management for a long time. One of the reasons is the overwhelming number of patches they need to handle. In 2021, over 20,000 vulnerabilities were fixed, making it increasingly challenging to keep up with all the updates.
Even if staying up-to-date with patches was easy, many users tend to ignore them, thinking they can afford to update their software a few days or weeks after the release. However, this practice can pose significant risks, which many users are unaware of. Furthermore, patch management is often given little attention in security awareness training, despite the Department of Homeland Security recommending that critical patches be applied within 15 days of release.
However, determining which patches are critical can be a dilemma for many security teams. These teams have procedures in place to ensure that patches are tested internally before deployment, as sometimes, they can be buggy or ineffective, causing more harm. IT teams also follow procedures to track patch deployments and to ensure that no device or system is left unpatched.
How to Protect Against Zero-Days?
It is crucial to understand that the threat landscape is always changing, and new versions of zero-day vulnerabilities emerge frequently. To keep yourself informed about the latest developments and types of zero-day vulnerabilities each year, it is recommended to follow reliable sources on cybersecurity and remain up-to-date with current events in this industry.
Moreover, in today’s cybersecurity landscape, Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) solutions are gaining significance. They work best when combined with the zero-trust model of protection.
Implementing updates promptly to improve cybersecurity and reduce risks by addressing known vulnerabilities is essential. By integrating EDR and XDR solutions that feature zero-trust architecture, organizations can detect, respond to, and mitigate security threats more efficiently, whether they involve known vulnerabilities or zero-day exploits. These technologies create a strong security posture prioritizing continuous monitoring, verification, and adaptive responses to evolving cyber threats. This helps to maintain a secure environment.