The media reported that Clop ransomware continues to work: its operators have again begun posting data stolen from victims on their website.
The fact is that last week, as a result of a joint operation carried out with the assistance and coordination of Interpol by the law enforcement agencies of Ukraine, South Korea and the United States, six suspects were detained, somehow connected with Clop, but, obviously, this did not affect the “work” of the group.
Ukrainian police reported that they conducted 21 searches in the capital of the country and in the Kiev region, in the homes of the defendants and in their cars. As a result, were seized: computer equipment, cars (Tesla, Mercedes and Lexus) and about 5,000,000 hrivnias ($182,900) in cash, which, according to the authorities, were received from the victims as ransoms. The suspects’ property was seized.
At the same time, according to the information security company Intel 471, the Ukrainian authorities arrested people who were only involved in money laundering for Clop operators, while the main members of the hack group are most likely hide in Russia.
Although after the arrests Clop’s “work” was suspended for about a week, now Bleeping Computer reports that the ransomware has re-activated and published data on two new victims on its website on the darknet.
The researchers did not disclose the names of the affected companies, but report that the personal details of the employees were released, including documents confirming employment (for loan applications), as well as documents on withholding of wages.
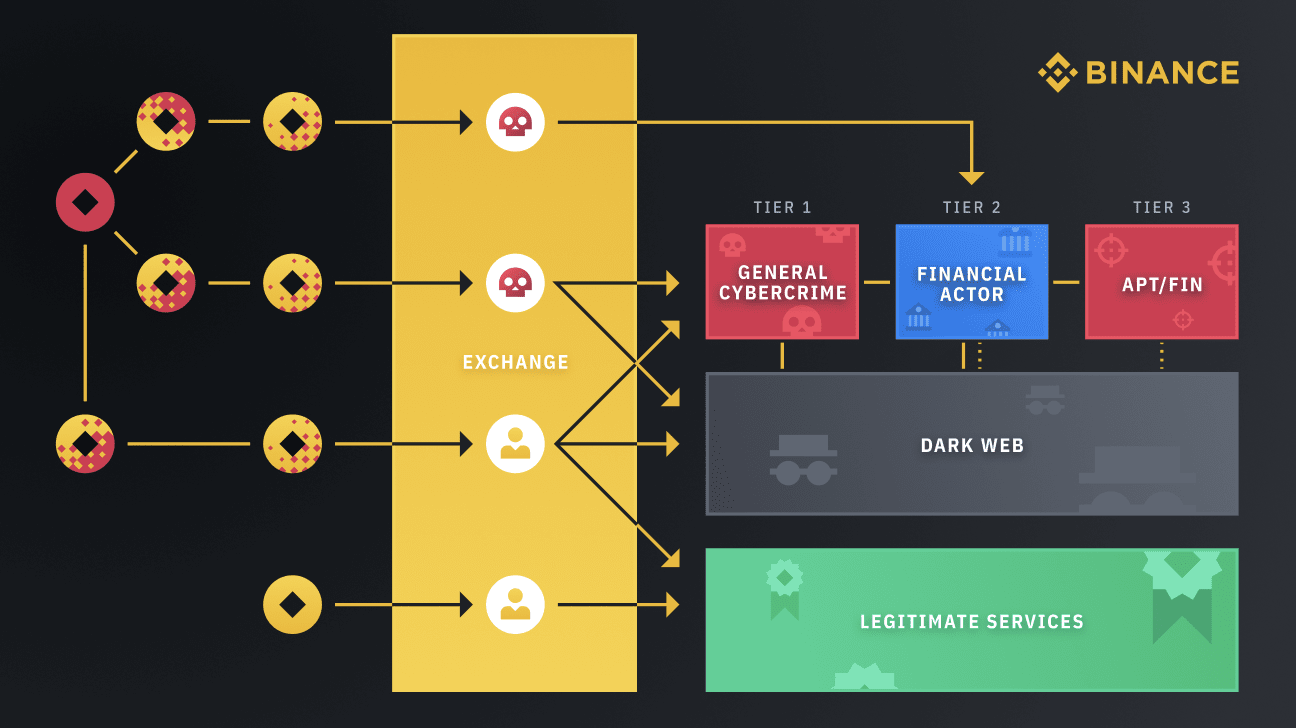
It should also be said that today the Binance cryptocurrency exchange announced that it took part in a recent law enforcement operation and helped identify criminals.
Exchange representatives said that they tracked the FANCYCAT group, which is engaged in various criminal activities, including the management of a “high-risk” cryptocurrency exchange. This group laundered money for ransomware such as Clop and Petya and is generally responsible for more than $500,000,000 in damages related to ransomware, as well as laundering millions of dollars associated with other types of cybercrimes.
Binance claims to have discovered FANCYCAT together with the blockchain analyst firms TRM Labs and Crystal (BitFury), and then provided all the information it gathered to law enforcement, leading to the group’s arrest earlier this month.
Let me remind you that I also wrote that France is looking for LockerGoga ransomware developers in Ukraine.