In a disturbing development, security researchers have uncovered a Linux version of the Qilin ransomware gang’s encryptor, specifically tailored to target VMware ESXi servers. This encryptor is one of the most advanced and customizable Linux encryptors observed.
Qilin Targets VMware ESXi
Today, more and more businesses are adopting virtualization technologies for server hosting. For example, VMware ESXi has become popular due to its effectiveness. However, attackers have quickly adapted to this trend and developed specialized encryptors to compromise these virtualized servers. While many ransomware operations use existing source codes, others use encryptors specifically for Linux servers. Thus, a recent discovery has revealed a Linux ELF64 encryptor for Qilin. It’s highlighting its adaptability across Linux, FreeBSD, and VMware ESXi servers.
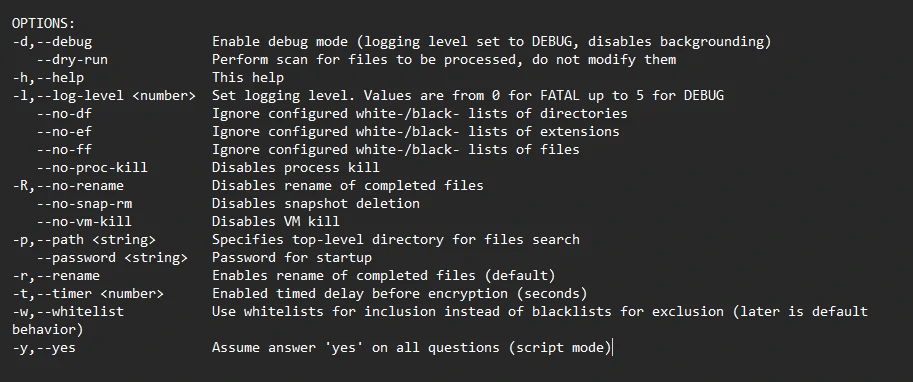
Qilin’s encryptor has embedded configurations that dictate file extension, process termination, file inclusion or exclusion, and folder encryption or exclusion. It also strongly emphasizes virtual machines that go beyond mere file encryption. The Qilin encryptor grants threat actors vast customization capabilities. These options range from enabling debug modes and performing dry runs to tailoring the encryption of virtual machines and their snapshots. Moreover, the encryptor allows threat actors to specify a list of virtual machines exempted from encryption.
What is Qilin Ransomware?
Initially launching as Agenda ransomware in August 2022, the Qilin ransomware operation rebranded in September and has been active under its current name. It is one of a few malware written in Golang, which can possibly grant it with some enhanced anti-detection capabilities. Running the typical modus operandi of enterprise-targeting ransomware, Qilin infiltrates networks, exfiltrates data, and subsequently deploys ransomware to encrypt all connected devices. Ransomware operation of the group has maintained a consistent victim count since its inception. However, it has notably intensified its activities in late 2023. Employing double-extortion tactics, the threat actors leverage stolen data and encrypted files to coerce victims into meeting ransom demands.
As for targets, Qilin opt for enterprises and high-value companies. It focuses on organizations in the healthcare and education sectors in Africa and Asia. TAs gain initial access using spear phishing and known exploitable apps/hardware pieces, such as Citrix and remote desktop protocol (RDP). The encryption setting supports several encryption modes that the ransomware operator can configure.
Safety Recommendations
Here are a few ways you can identify Agenda ransomware in your network:
- Employees Education & Training. The most effective method is to train employees in the basics of cyber hygiene. Forewarned is forearmed.
- Data Backup. The following measure is to back up your data regularly, offline if possible. This will prevent the offline data copies from being corrupted and help restore the data without much effort.
- Security Tools. We recommend using security tools that use signatures, heuristics, or AI algorithms to identify and block suspicious files or activities. It can detect and block known ransomware variants.
- Network Traffic. Monitoring network traffic for any signs of compromise, such as unusual traffic patterns or communication with known command-and-control servers, allows the detection of suspicious activity.
- Security Audits. We recommended regular security audits and assessments to identify network and system vulnerabilities to maintain up-to-date protection.





