A vulnerability in Microsoft Outlook is under active exploitation – that is the worrying notification from Microsoft. World largest software developer warns about Russian state-sponsored hackers using this breach to perform cyberattacks. Despite the fix for the issue being released over 8 months ago, there is still a concerning amount of unpatched instances.
Microsoft Outlook Vulnerability Used by Kremlin-Backed Hackers
Being a privilege escalation bug, CVE-2023-23397 received almost the highest CVSS score of 9.8. The rating was set back in March 2023, when the vulnerability was originally uncovered. And well, the flow of attacks commenced with this vulnerability exploitation confirms every bit of this score.
By its essence, the vulnerability consists of the ability to leak the Net-NTLMv2 hash by sending a specially-crafted email message. It is possible due to the features of the specific transfer format Microsoft uses in the Outlook. Through playing with the PidLidReminderFileParameter settings, adversaries can leak the hash and send it to its command server. That’s it for this exploit, but the main course of actions happens afterwards.
Forest Blizzard Exploits MS Outlook in Attacks on Poland
Microsoft researchers noticed one main threat actor using the CVE-2023-23397 in its cyberattacks – Forest Blizzard a.k.a. APT28/Fancy Bear. This threat actor has a proven connection to the Russian government, particularly to the Main Intelligence Directorate (GRU). In the campaign that exploited the described Outlook vulnerability, hackers primarily targeted Poland.
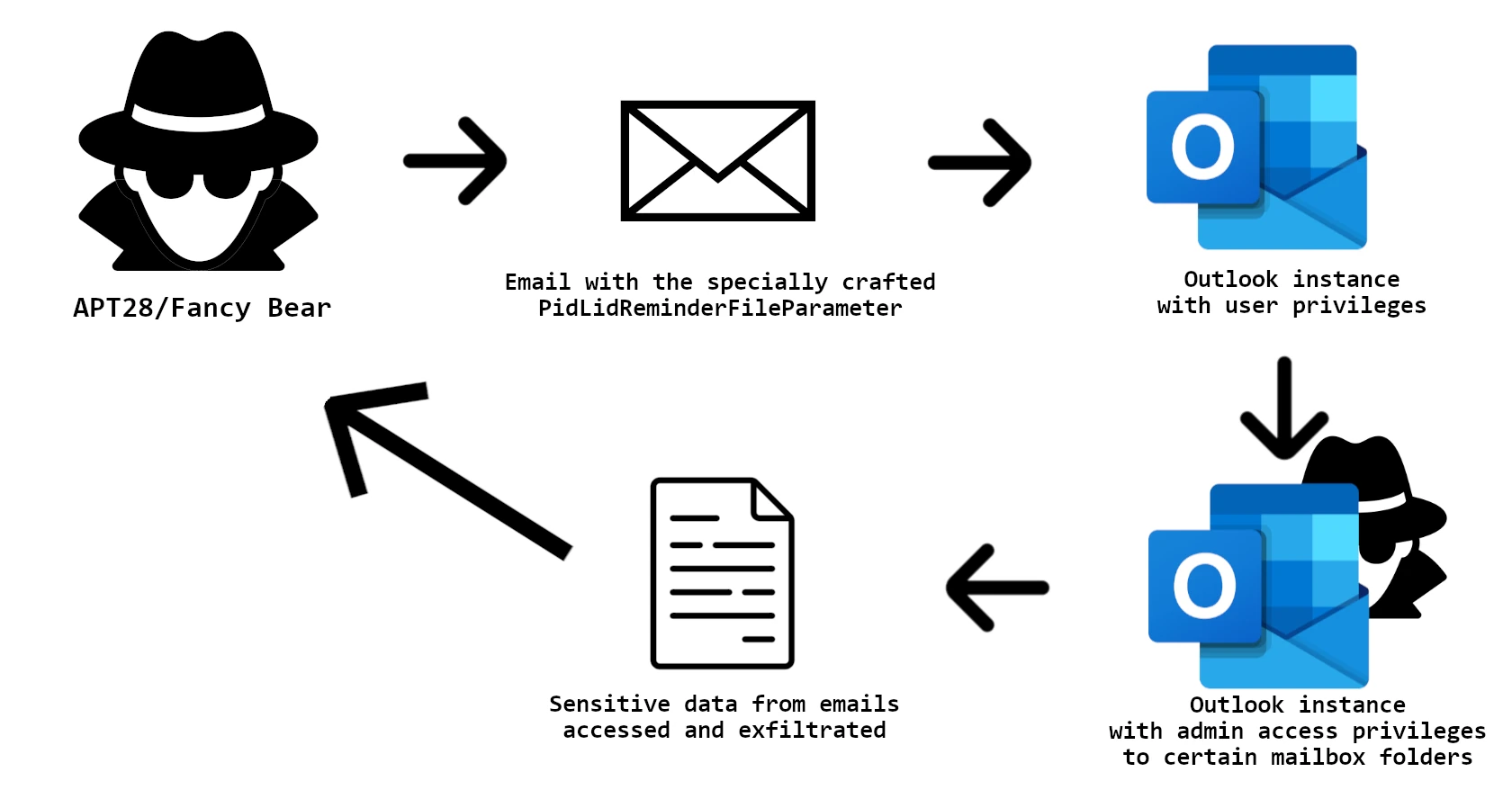
Upon receiving the Net-NTLMv2 hash, adversaries were able to manipulate the access permissions to specific mailbox folders. This, in turn, ended up with the ability to read all of the contents. Hackers specifically aimed at ones that could store any valuable and potentially sensitive information.
Such a targeting is rather obvious – Poland has had its relations with Russia ruined since February 2023. And its participation in supplies delivery to Ukraine is a point of interest for Russian intelligence. While such espionage bears on the same tactics as cybercriminals use in attacks on corporations, the final target is what is different. Though, nothing stops hackers from applying the same tactics in attacks on other countries.
Install the Patch, Microsoft Insists
As I have mentioned at the beginning, the patch for the CVE-2023-23397 was available all the way back in March 2023. Microsoft released it almost immediately after disclosing it. And since it is a vulnerability in the protocol, there is not much you can do to temporarily mitigate the issue. Even though it may be troublesome to update all the instances soon after the patch, it was plenty of time to arrange the update.





