Researchers have identified an updated version of NodeStealer, now rewritten in Python. This version is capable of extracting additional information from Facebook Ads Manager accounts and credit card details stored in web browsers.
What is NodeStealer?
NodeStealer first appeared in May 2023 as JavaScript-based malware. It was created by Vietnamese attackers previously known for developing malware targeting Facebook business accounts that run advertising campaigns. Hackers further employ these accounts in a chain of other scams.
In its recent update, this malware evolved to a Python-based infostealer, gaining more extensive data collecting and detection evasion capabilities. Although Python-based viruses are pretty easy to detect, it still packs enough functionality to remain effective for quite a significant range of applications.
Among the most noticeable things, the updated NodeStealer introduced features such as using Windows Restart Manager in its operations. This feature enabled it to unlock browser database files, inject additional code, and execute a batch script to dynamically generate and run Python scripts.
Experts believe attackers aim to use hijacked ad accounts to launch malicious advertising campaigns. These campaigns typically distribute malware disguised as popular software or games.
NodeStealer Gets Updated to Python
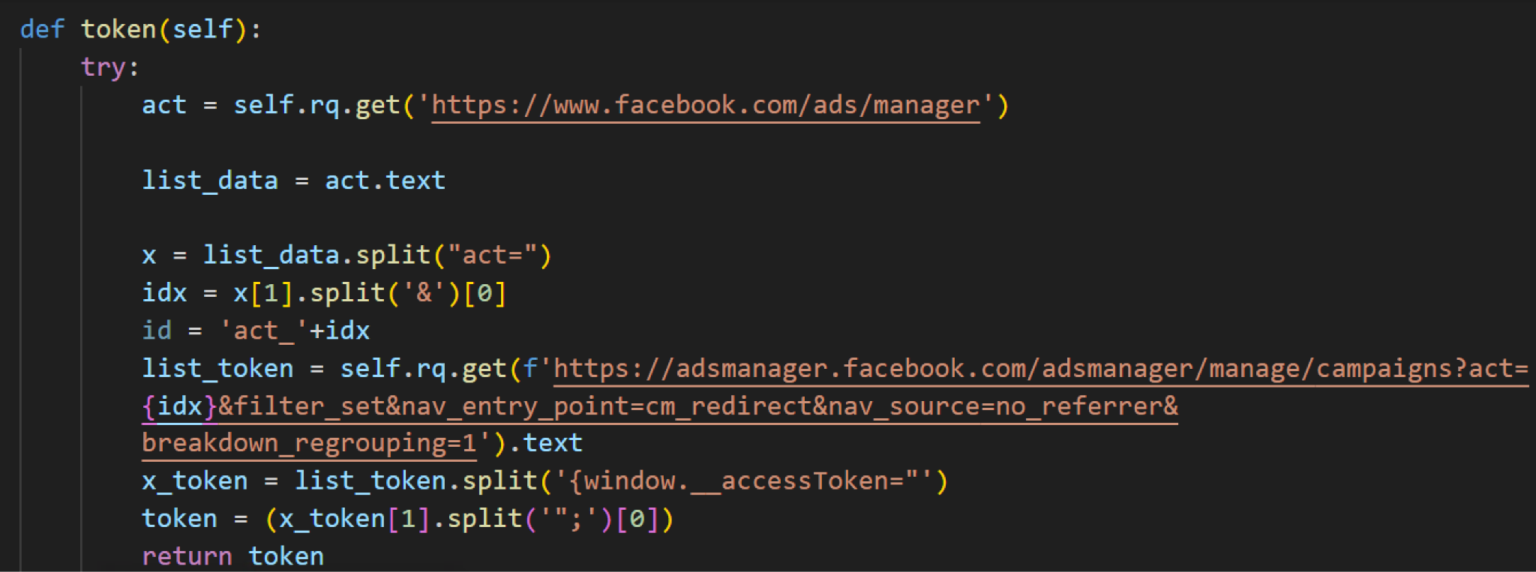
Researchers have identified Python-based NodeStealer samples that retrieve account budget information using the Facebook Graph API. This is achieved by generating an access token during login to adsmanager.facebook[.]com, using cookies harvested from the victim’s device. This feature has already got a rather interesting continuation, I’d get back to it later.
As with many localized malware variants, NodeStealer verifies the victim’s geographic location during execution. If it identifies the victim’s device as being in Vietnam, the malware halts execution. This obviously prevents targeting of local users and avoids drawing attention from local law enforcement.
In certain attack cases, NodeStealer uses the Windows Restart Manager to access some additional functionalities, particularly to access SQLite database files. The latter are used by web browsers to store AutoFill forms, i.e. all the passwords and login information that the user keeps locally. Such an approach is not typical, and is likely used to avoid raising alarm.
Once the necessary manipulations are complete, the malware uploads the stolen data to the attackers’ command-and-control (C2) server. Telegram is commonly employed as the C2 server, favored by attackers for its resistance to tracking, though NodeStealer can be configured to connect to Mastodon, Steam or a stand-alone command server.
It is worth noting the use for the leaked malicious Facebook ads that impersonated the open-source Bitwarden password manager. This campaign aimed to deceive users into installing a malicious Google Chrome extension that parodies the password management tool. The extension, in turn, grabs all the passwords kept in the keychain (it usually more extensive than what is stored in browser files) and sends it to a command server.
How to Protect Yourself?
As we can see, attackers continue their relentless efforts to exploit Internet users. While no solution offers complete protection, certain practices can greatly reduce the risk of falling victim. Users should exercise caution with advertising banners and links on social networks, avoiding clicks on unfamiliar or suspicious advertisements altogether. In general, I would not recommend clicking on any advertising links. Additionally, employing robust anti-malware software, like GridinSoft Anti-Malware, can block malware downloads and execution, providing an essential layer of protection.