A new botnet called NoaBot emerged in early 2023. It reportedly targets SSH servers for cryptocurrency mining using the Mirai platform. On top of the Mirai’s functionality, it brings several detection evasion tricks.
NoaBot Involved in Crypto Mining
Cybersecurity experts have discovered a new botnet called NoaBot. It has been active since at least the beginning of 2023, and the purpose of this botnet is illegal crypto mining. It is based on the Mirai botnet, a notorious malware for harnessing infected IoT devices for large-scale network attacks. Despite being a derivative, it keeps all the functionality of the Mirai – a thing that can barely be underestimated.
NoaBot’s primary strategy involves an SSH scanner searching for vulnerable servers to brute-force and deploy an SSH public key, allowing remote access. However, unlike previous Mirai versions, NoaBot has unique features that make it difficult for antivirus software to detect. It is compiled with uClibc, which can cause it to be misidentified as an SSH scanner or generic trojan.
What’s Under the Hood of NoaBot?
As I’ve mentioned, NoaBot developed on the foundation of the infamous Mirai botnet, whose source code was leaked in 2016. At the core of NoaBot’s operations lies a modified version of the XMRig coin miner. Although it is an open-source and widely used cryptocurrency mining program with legitimate uses, it is also popular among attackers. Additionally, it is equipped with a wormable self-spreader and an SSH key backdoor. As a result, this enables it to download and execute additional binaries and extend its reach to new victims.
NoaBot’s lateral movement strategy revolves around SSH credentials dictionary attacks, exploiting weak or default passwords. What sets NoaBot apart in illicit crypto mining is the obfuscation of its configuration and the use of a custom mining pool. Thus, it conceals the miner’s wallet address and obscures the scheme’s profitability. The researchers suspect that the creators of NoaBot are also using pieces of code from a Rust-based P2PInfect worm, which emerged in July. The reason behind this hypothesis is that some samples of P2PInfect contain specific text and inside jokes that are also present in the NoaBot code, such as lyrics from game-related pop songs.
Global Impact
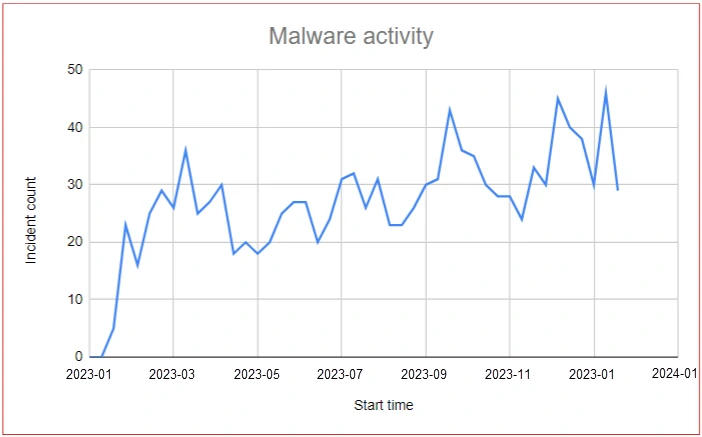
Analysis of victimology reveals that honeypots were attacked by 849 different source IPs across 2023. Upon investigating their geolocation, it was found that the attacks were distributed relatively evenly across the globe. This could be attributed to the wormable nature of the malware, as every infected victim becomes an attacker. However, one particular hotspot of activity stood out, originating from China. This hotspot accounted for almost 10% of all the attacks observed across 2023 and was the most prominent hotspot.
Overall, miner botnets are not something new, although such a botnet targeting Linux machines and capable of self-spreading is rather unusual. Massive amounts of IoT devices that are susceptible to NoaBot can bring lots of profits to its creators. Smart fridges and washing machines have a relatively low calculation power, though the sheer volume of them will cover the difference.
Safety Recommendations
Since the attack involves plain old SSH credentials dictionary attacks, it would be logical to restrict arbitrary internet SSH access and use strong passwords. It will prevent malware from spreading via SSH. Additionally, you can block the known default and vulnerable ports hackers are usually trying to log in through. These two steps will already reduce the chance of malware deployment, regardless of the type and source.