The cyber world has been rattled by the recent discovery of a critical zero-day vulnerability in Apache OFBiz, known as CVE-2023-51467. Researchers at SonicWall unveiled this flaw, which poses a significant threat by enabling attackers to bypass authentication and carry out a Server-Side Request Forgery (SSRF). The vulnerability is severe, with a CVSS score of 9.8, and has sparked concerns across various industries relying on Apache OFBiz’s Java-based web framework.
What is Apache OFBiz?
Apache OFBiz is an integral part of the digital backbone of numerous industries, ranging from financial services to healthcare. This open-source Enterprise Resource Planning (ERP) system is a key player in managing complex business processes, which is essential for large enterprises. This is what makes the CVE-2023-51467 vulnerability something more than a technical glitch. Its extensive exploitation can be a potential gateway for catastrophic disruptions in critical services and infrastructure.
Apache OFBiz Vulnerability – Technical side
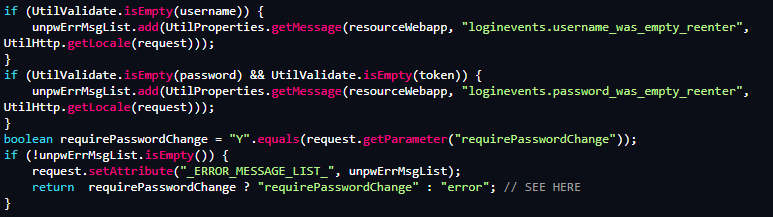
SonicWall’s research team detected this critical zero-day vulnerability and promptly disclosed it to Apache OFBiz’s maintainers. The root of this vulnerability lies in the application’s login functionality. Attackers exploiting CVE-2023-51467 can bypass authentication by manipulating the checkLogin function in Apache OFBiz. By setting the “requirePasswordChange” parameter to “Y” in the URI and supplying null or invalid credentials, the function mistakenly returns a success status, thus allowing unauthorized access. The vulnerability specifically affects the login process of Apache OFBiz.
How does the exploit work?
- Manipulating the CheckLogin Function
The core issue lies in the “checkLogin” function. Normally, this function should validate a user’s credentials before granting access. However, due to a flaw in its implementation, it fails to perform this task correctly under certain conditions. - Exploiting Null or Invalid Credentials
The exploit involves sending a crafted HTTP request where the “USERNAME” and “PASSWORD” parameters are left empty, or invalid values are provided. However, the exploit includes the “requirePasswordChange=Y” parameter in the URI. - Bypassing Authentication Checks
Due to the flawed logic in the “checkLogin” function, when it receives null or invalid credentials along with the “requirePasswordChange=Y” parameter, it incorrectly bypasses the usual authentication checks. Specifically, it fails to enter the conditional block that checks whether the username and password are null. Consequently, it erroneously returns a success status, allowing the authentication process to be bypassed. - Potential for Server-Side Request Forgery (SSRF) or Remote Code Execution (RCE)
By bypassing authentication, an attacker could potentially perform SSRF or RCE, leading to unauthorized access to sensitive data or control over the system.
The exploitation of this flaw could lead to dire consequences. Attackers could potentially gain control over sensitive systems, compromise confidential data, and disrupt essential services. Also, he widespread use of Apache OFBiz in various sectors heightens the risk of large-scale, coordinated attacks that could target multiple facets of society simultaneously.
Patch and Recommendations
In response to this alarming discovery, Apache released a security update. The new version, 18.12.11, addresses the vulnerability and is strongly recommended for immediate implementation. Additionally, organizations are advised to conduct thorough security audits and apply patches to all affected platforms promptly.
Users of Apache OFBiz are strongly advised to:
- Upgrade to Apache OFBiz version 18.12.11, which contains the fix for this vulnerability.
- Regularly audit systems for vulnerabilities and apply necessary patches.
- Keep an eye on system logs and access patterns to detect any signs of exploitation attempts.
- Utilize XDR solutions proactively to prevent cyberattacks by continuously monitoring and correlating data across endpoints, networks, and cloud environments. Early threat detection and rapid response are key.


