IoT malware has been a major concern over the last decade. However, trends show that things are turning even worse – recent ZScaler research shows a 400% growth in IoT malware attacks in 2023 only. And most likely, it will become worse.
Massive jump in attacks on IoT infrastructure
According to the study, the number of IoT devices is growing, and obviously, the number of attacks grows along them. In the last six months alone, attacks on IoT devices have increased 400% year-to-year. Such a colossal figure, isn’t it? Although these devices were created for our convenience, cybercriminals think otherwise. The IoT, a vast network of interconnected devices, permeates our daily lives. However, if something has firmware that can be updated – sooner or later, cybercriminals will find a way to use it for their dirty deeds.
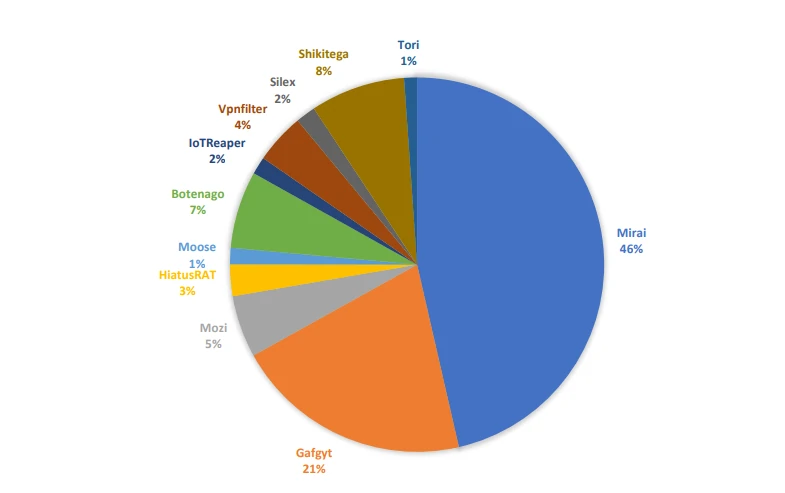
Additionally, research shows that cybercriminals commonly target vulnerabilities that have been around for more than three years. Their target is obvious: creating vast botnets from infected devices. As for malware families, about 66% are backdoors – ones that support botnet creation. For example, the leader is the Mirai botnet, with a 45.9% share. The next one is Gafgyt, which accounts for 20.3% of all infected devices. The main scenario of using such botnets is organizing DDoS attacks against enterprises. Oftentimes, hackers offer their DDoS power for sale on the Darknet – and such a service retains high demand over the years.
Manufacturing Is The Most Targeted Industry
Today, the manufacturing sector is nearly triple the rate of other industries in terms of unique IoT devices. This dramatic growth indicates the industry’s desire to adopt advanced automation and digitization. As this “digitalization” involves adding smart sensors and devices, it expands the attack surface. Not surprisingly, the manufacturing sector receives more than three times as many attacks as any other sector in an average week, accounting for 54.5% of malware attacks.
The problem is that some IoT devices are built for ease of use and accessibility rather than security. This means they may have security vulnerabilities that attackers can exploit. Attacks on OT infrastructure can cause significant disruptions to critical industrial operations, disrupt critical OT processes, and, in some cases, even threaten lives. These are primarily the automotive, heavy manufacturing, plastics, and rubber industries.
Which Countries are at IoT Malware Risk?
According to the report, the U.S., Mexico, Brazil, and Colombia are the most commonly targeted countries. While 96% of IoT malware spreads from compromised IoT devices in the U.S., three of the four most affected countries are in Latin America. This abundance of infected devices in the States is because the U.S. has a high level of IoT integration. In addition to regular users, these devices are connected to critical infrastructure or enterprises. This motivation makes cybercriminals attempt to profit by compromising them.
Latin American countries are particularly vulnerable to IoT malware attacks. For example, Mexico accounts for 46% of all infections. This is due to relatively low levels of cybersecurity awareness and preparedness, as well as proximity to the U.S. The education sector has recently become a prime target for cybercriminals. It’s related to the widespread use of unsecured and shadow IoT devices in school networks. These devices give attackers more accessible access points to sensitive personal data stored on educational institutions’ networks. As a result, the rate of cyber attacks in this sector has increased by a staggering 961%, just shy of 1,000%. That’s not a good sign and demands immediate attention to protect the privacy and security of students, faculty, and staff.
How to Protect Against IoT Malware?
While there is no perfect defense, there are preventative measures that can help avoid most of these problems. The following recommendations will reduce the risk of device compromise:
- Train employees on IoT device security. Forewarned is forearmed. Because humans are the weakest link in the line of defense, training employees in cybersecurity is an effective measure.
- Use a zero-trust policy. A zero-trust philosophy eliminates any cybersecurity cronyism. This means that all devices and users are considered untrusted by default. Any unauthorized shadow IoT devices will be blocked from corporate data by proxy.
- Maintain comprehensive visibility into IoT devices. Keeping your IoT devices secure is essential to knowing all devices connected to your network and what they’re doing, including unmanaged ones. The best way to do this is to use solutions that analyze network logs, which can help you monitor communications and activity.
- Use multi-factor authentication. It adds another one layer of security by requiring users to enter a secondary mode of verification in addition to their password. This can prevent attackers from accessing user accounts if credentials are obtained, stopping lateral threat movement from compromised user devices.