Akamai specialist Larry Cashdollar discovered a hacker group that uses hacked WordPress sites in an interesting way. First, hackers run fraudulent online stores over WordPress sites. Second, they poison XML maps to influence search results.
Attackers use brute force attacks to gain access to the site administrator account, next they overwrite the main index file of the WordPress site and add malicious code to it.
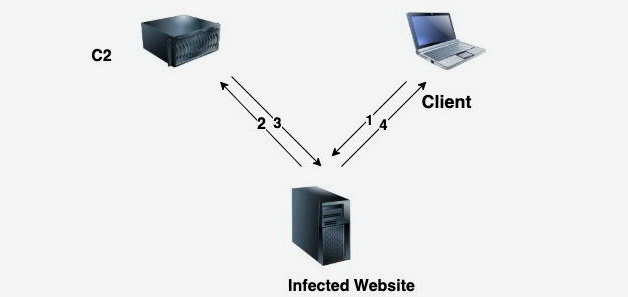
Although this code was heavily obfuscated, Cashdollar writes that the main role of this malware was to act as a proxy and redirect all incoming traffic from compromised sites to a remote server of the criminals. On this server happened the most interesting things.
A typical attack looked like this:
- the user visits the hacked WordPress site;
- the hacked site redirects the user’s request to the malware’s control server;
- if the user meets certain criteria, the hacker’s server tells the site to respond to the visitor with an HTML file with a fraudulent online store selling a wide range of goods;
- The compromised site responds to the user’s request by displaying a fraudulent store instead of the original site that the user intended to view.
According to the expert, by the time the hackers reached his decoy server, they had already launched more than 7,000 fake stores.
While this procedure looks harmless, it actually made a big impact on the affected sites. The point is that, in the end, such XML maps significantly lowered resource rankings in search results.
According to Cashdollar, such malware can be used for SEO-related ransomware. For example, criminals deliberately downgrade a site in search results, and then ask its owners for a ransom in order to eliminate the consequences of the attack and “return everything as it was.”
Let me remind you that recently researchers from Imperva have found that the KashmirBlack botnet, active since the end of 2019, is behind attacks on hundreds of thousands of websites powered by WordPress




