In May, Microsoft released a security update, as it had previously not fully coped with attacks called PetitPotam.
The update and mitigation recommendations target a heavily exploited vulnerability in NTLM Relay called Windows LSA Spoofing Vulnerability with the number CVE-2022-26925.
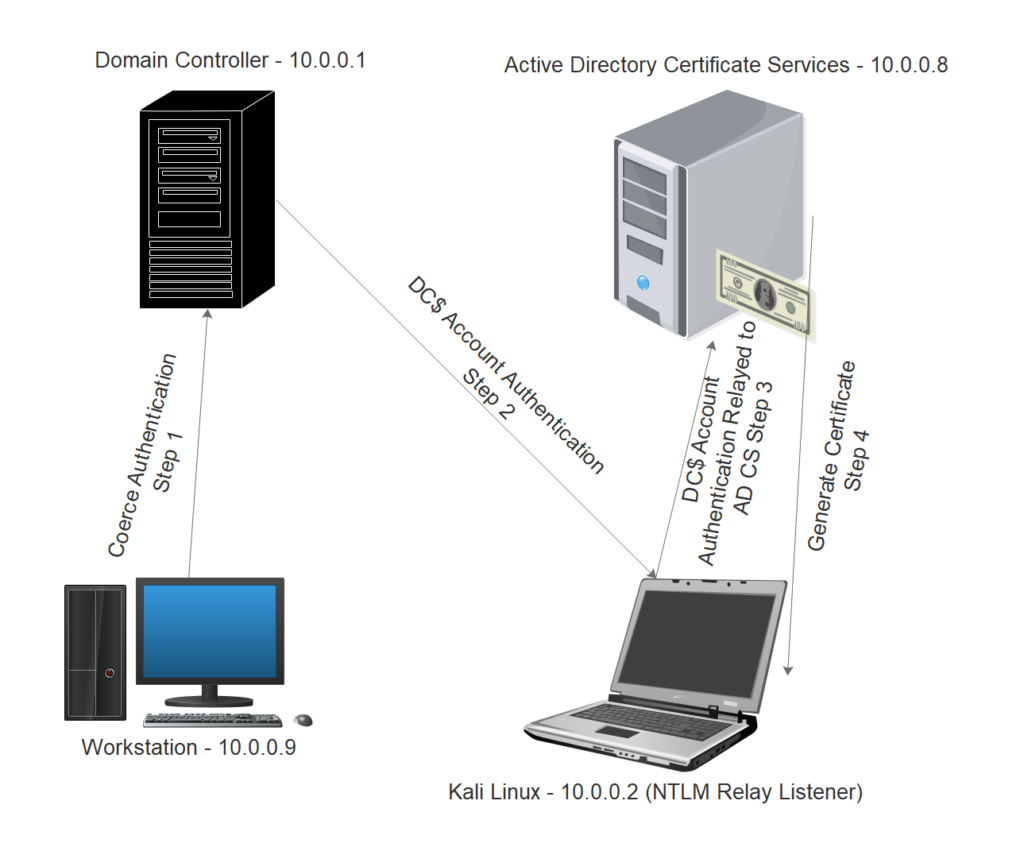
Last July, security researcher Gilles Lionel, also known as Topotam, introduced a new PetitPotam method that could be used by an attacker to force a domain controller to authenticate a server that it controls using the MS-EFSRPC APIs.
As the researcher explained, an attacker can communicate through the Windows LSARPC interface and execute MS-EFSRPC API functions without authentication. These functions, OpenEncryptedFileRawA and OpenEncryptedFileRawW, allow an attacker to force a domain controller to authenticate its NTLM server.
The NTLM relay then forwards the request to the victim’s Active Directory Certificate Services over HTTP to obtain Kerberos TGTs, allowing the attacker to obtain the identity of any device on the network, including the domain controller.
By the way, we previously reported that The LockFile ransomware exploits ProxyShell and PetitPotam Vulnerabilities to Increase its Chances of Hacking and Encrypting Corporate Networks.
The PetitPotam vulnerability could allow a threat actor to authenticate a device against a malicious server. Once authenticated, a malicious server can impersonate a device and gain all its privileges. The error is a serious threat and allows an attacker to take full control of the domain.
Microsoft fixed part of the PetitPotam vulnerability in August 2021, but there are still unpatched vulnerabilities that allowed hackers to carry out attacks. However, a recent update fixing the NTLM Relay Attack bug may actually prevent the PetitPotam attack.
The new security update has fixed the PetitPotam “EfsRpcOpenFileRaw” vector, other EFS attack vectors still exist and allow cybercriminals to operate. As new PetitPotam vectors and other NTLM Relay attacks are discovered in the future, Microsoft has proposed mitigation measures.